
As the world steps up to COVID-19 vaccine campaigns, state-sponsored actors are tapping the situation with targeted cyberattacks and scams. From targeting vaccine research centers to spreading imposter vaccine versions on the dark web, threat actors are capitalizing on the pandemic with Coronavirus vaccine-related phishing campaigns.
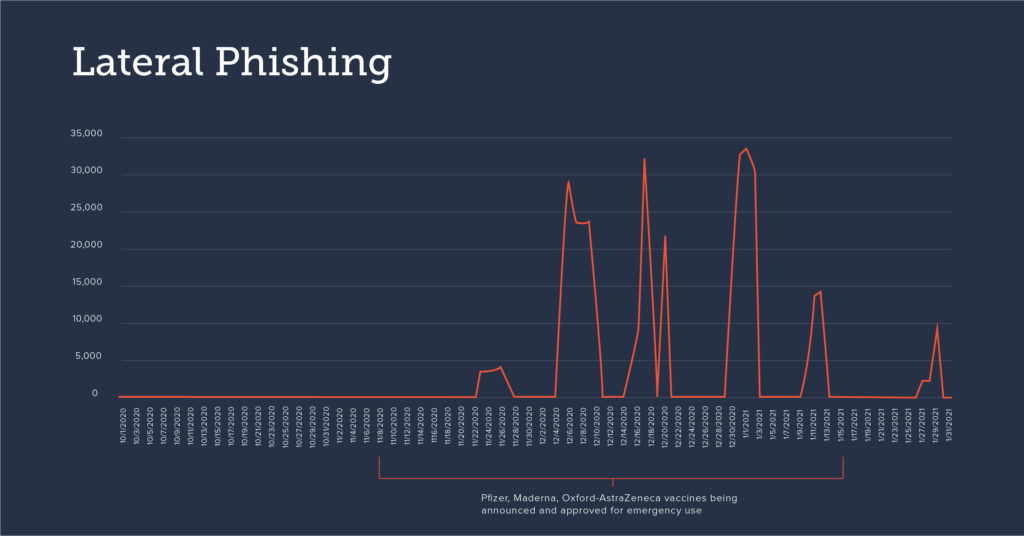
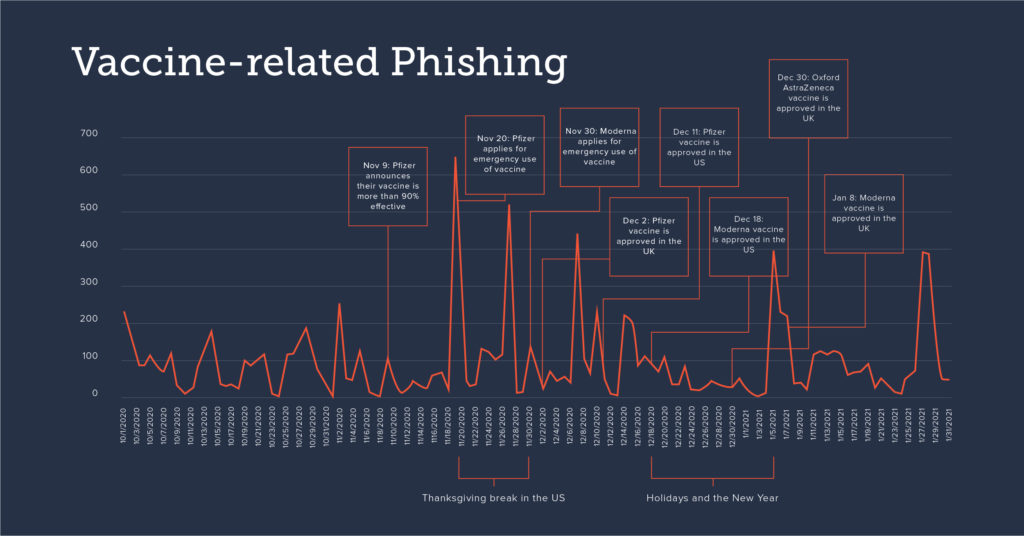
A recent analysis from Barracuda, conducted between October 2020 and January 2021, found that threat actors are leveraging vaccine-related emails in their targeted spear-phishing attacks. The research revealed that the number of vaccine-related phishing campaigns increased by 12% after some pharmaceutical companies announced the availability of vaccines in November 2020.
“Cybercriminals use phishing attacks to compromise and take over business accounts. Once inside, more sophisticated hackers will conduct reconnaissance activity before launching targeted attacks. More often than not, they use these legitimate accounts to send mass phishing and spam campaigns to as many individuals as possible before their activity is detected, and they are locked out of an account,” Barracuda said.
Types of Phishing Attacks
Barracuda researchers stated that attackers used two types of spear-phishing attacks: Brand Impersonation and Business Email Compromise attacks.
- In brand impersonation attacks, scammers leveraged COVID-19 vaccine-related phishing emails mimicking popular pharmaceutical companies. The phishing emails contained links to fraudulent websites that are advertising early access to vaccines and asking victims for payment. Besides, the fraudsters impersonated health care professionals, tricking users to reveal their personal information to check eligibility for a vaccine.
- In business email compromise (BEC) attacks, scammers posed HR specialists, recommending vaccines to their employees. In a BEC attack, cybercriminals first steal legitimate business email account credentials, which are later used to launch financial fraud campaigns like fraudulent email messages, requests for out-of-channel funds transfers, and deleted accounting trails.
Barracuda researchers stated they found various phishing emails claiming: “offers to get the COVID-19 vaccine early,” “join a vaccine waiting list,” and “have the vaccine shipped directly to the home.” Researchers urged users to avoid clicking/opening such fraudulent links or attachments that they receive from unverified sources.
State-Sponsored Attacks on COVID-19 Vaccine Research
Recently, the U.K.’s National Cyber Security Centre (NCSC), Canada’s Communications Security Establishment (CSE), and the National Security Agency (NSA) of the U.S. stated that a cyberespionage group “APT29” which is linked to Russian intelligence services, tried to steal information and intellectual property related to the testing and development of Coronavirus vaccines. The group is using its custom malware known as WellMess and WellMail and other techniques to target government entities. Read the full story here…






















