
These days, it’s not a matter of if, but when an organization experiences some kind of data breach. Incidents are increasing in number and severity. Data breaches have become more expensive to resolve and more challenging to defend against.
See also: How to Ensure Data Management Excellence
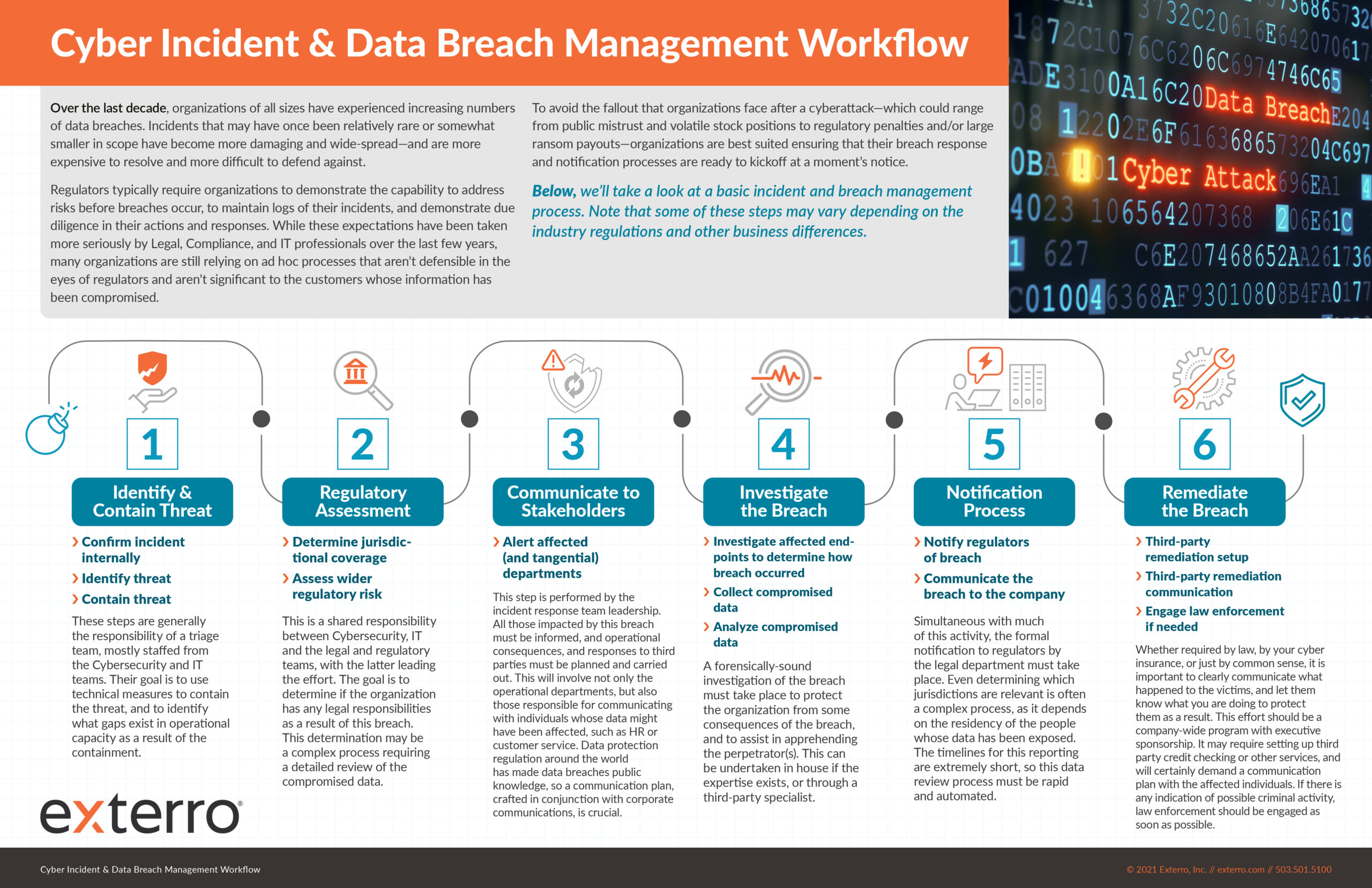
The stakes are high for organizations who experience a breach — loss of revenue, lost customers, and a negative impression in the market are just a few of the consequences. That’s why your first step in incident response should start long before anything happens. Being well prepared and having a comprehensive plan in place with optimal workflows, like the basic incident and breach management workflow offered here, will allow your organization to get the job done accurately and efficiently.
To avoid the fallout that organizations face after a cyberattack – which could range from public mistrust and volatile stock positions to regulator penalties and/or large ransom payouts – organizations are best suited to ensure that their breach response and notification processes are ready to kick off a moment’s notice.
The following infographic highlights:
- The 6-step process to a defensible incident and breach response, and,
- How technology can orchestrate a strong and defensible breach response process

Schedule a demo at https://marketing.accessdata.com/l/46432/2021-08-10/8qkk4t









![How To Find a Phishing Email [INFOGRAPHIC] Phishing email](https://cisomag.com/wp-content/uploads/2021/10/MicrosoftTeams-image-38-238x178.png)












