
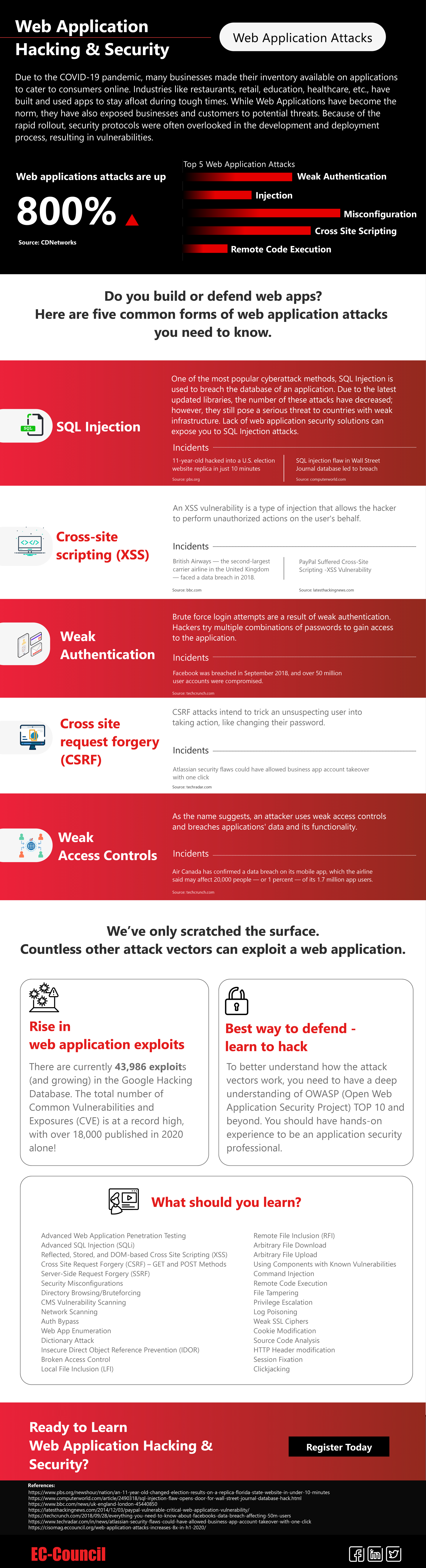
Amidst the pandemic, there has been an exponential rise in the number of businesses embracing digital transformations like web applications to streamline their workload and digitally exchange data and transactions. While this has numerous benefits for users, it also highlights significant weaknesses and vulnerabilities in web browsers that lead to web application attacks. You can avoid falling prey to data breaches and other such attacks by being well-versed in mitigating the risk of web applications attacks.
It would also help to know about the most popular web-based attacks to build a strategy to mitigate such risks.
- Weak authentication is a scenario where the layers of security are weaker or incompatible with the value of protected assets. Moreover, weak authentication can also point towards a situation where the authentication process is flawed or vulnerable.
- On the other hand, a Cross-Site Request Forgery or Session Riding attack can disrupt the operation between the business and the user. The attacker leverages social engineering techniques to trick the target into executing a forged request in their server. Hence, it becomes impossible for the user to distinguish between what’s legitimate and what’s not. Thus, it leads to disruptive web-based attacks.
- Since access control design decisions are made by humans and not machines, the scope of errors creeping in through weak access controls is relatively high. As a result, attackers quickly make their way through a web application attack and breach the accessibility and privacy of the stored data in case of weak access controls.
- Further, attackers can interfere with an application’s query to its database through an SQL attack. Through this, they can access data unavailable to them in normal circumstances and risk privacy and the authenticity of the data.
To steer away from these web application attacks, you must have complete visibility of the code being run on your website and conduct regular security assessments. Web Application Hacking and Security (WAHS) Course is crafted by the same team that developed the C|EH to give you hands-on training in a lab-based environment.
Brace yourself to fight against the topmost web-based attacks through a guided mastery course at EC-Council. Become a Certified Web Application Security Professional today.




![How To Find a Phishing Email [INFOGRAPHIC] Phishing email](https://cisomag.com/wp-content/uploads/2021/10/MicrosoftTeams-image-38-238x178.png)





