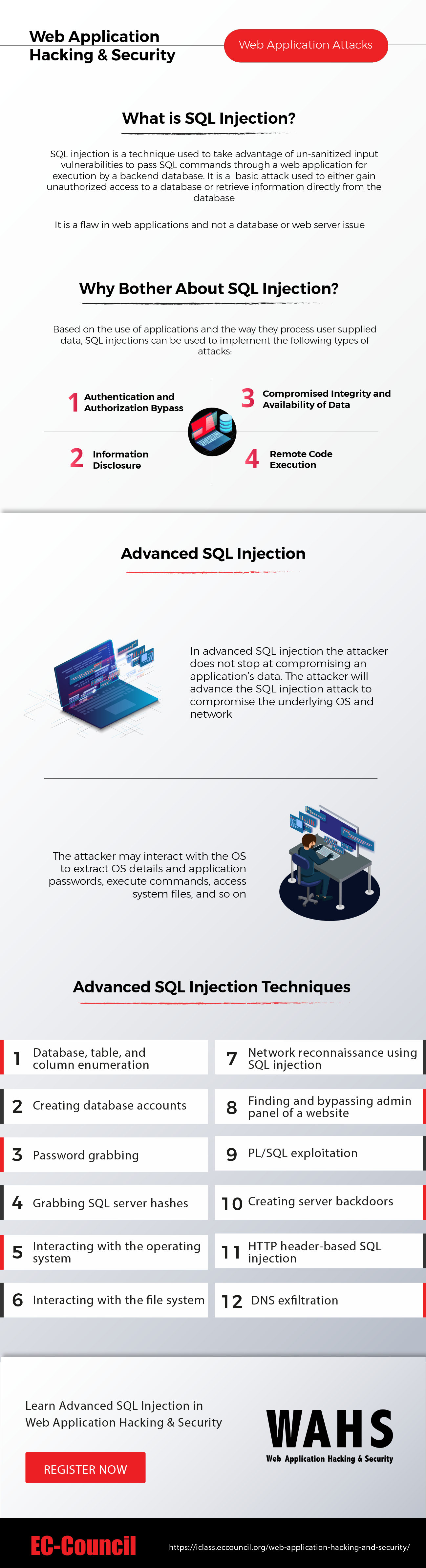
SQL Injection Attacks are amongst the most prevalent type of attacks today, which primarily targets web applications. With the rise in the use of web applications because of their efficiency and convenience, attackers have developed various techniques to infiltrate the vulnerability in web apps and gain unauthorized access to obtain confidential data.
One such method is the SQL injection, which utilizes malicious SQL commands that, when executed, modify the backend code, that is, edit, delete, or insert data into the database affecting the CIA triad — Confidentiality, Integrity, and Authenticity of the data. On successfully executing the SQL injection commands, the attacker can spoof identity, tamper with data, disclose data, take complete control over the database, cause repudiation issues, etc. In simple terms, SQL injection, also known as SQLI, is a code injection method used by attackers to gain access and modify the data present in the database of web applications.
See also: What is an SQL Injection Attack and How to Prevent it?
Various organizations, as well as customers, utilize web applications based on their necessities. Upon successful execution of an SQL injection attack, the impact on the businesses is devastating. Apart from the exposure or manipulation of data, the trust between the organization and its customers is affected, tarnishing the company’s reputation in the market. There are numerous types of SQL injection methods such as:
Error-based SQL injection: This type of injection technique causes the SQL databases to send error messages. As a result, the attackers gain information about the structure of the database of the web applications.
Blind SQL injection: Also known as Inferential SQLI, it is the act where an attacker sends payloads to the server. It is aimed at asking true or false questions to the database. Based on the response and the behavior of the sent payload, the attacker learns about the database structure. However, the attacker cannot view the data or information transmitted from the website database, and thus, it is known as name-blind SQLI.
Union-based SQL injection: In this SQL injection attack, the attacker uses the SQL UNION operator, which merges the results of two or more SQL SELECT operators, displayed as a part of the HTTP response.
Organizations and professional experts need to understand the intensity of such attacks. SQL injection attack prevention is essential for every organization to secure and protect its confidential data. One can become a professional web app hacker and security expert to judge and verify the security strategies of an organization’s web applications.
EC-Council’s Web Application Hacking and Security certification provide the necessary skills required to identify and mitigate web app vulnerabilities and exploitable threat factors. Become a certified Web Application Hacking and Security Professional today.