
In January 2021, the phone numbers of Facebook’s 533 million users went on sale on the online messaging platform, Telegram. Cybercriminals are known to leverage popular messaging platforms to sell the data exfiltrated during their malicious campaigns. However, to everyone’s surprise, they used a Telegram bot to make the sale. The bot was trained to charge a minimal fee of $20 per search. However, a new report from cybersecurity firm Group-IB has now revealed that growing usage of Telegram bots and Google Forms has been observed in phishing toolkits to automate their malicious phishing campaigns.
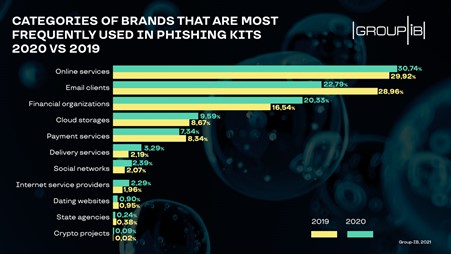
Group-IB’s CERT closely analyzed the tools used to create the phishing toolkits. They discovered that, in 2020, most of the toolkits were used to imitate online services that included online tools to view documents, online shopping, streaming services, etc. (30.7%), email clients (22.8%), and financial organizations (20.33%). In addition to this, their analysis of last year also identified phishing kits targeting over 260 unique brands, with Microsoft, PayPal, Google, and Yahoo leading the list of most exploited brands.
But what is a phishing toolkit?
A phishing toolkit is a set of tools that helps create and operate phishing web pages mimicking a specific brand or company or even several at once. Phishing toolkits are usually sold on underground forums to cybercriminals who lack strong coding skills. These phishing kits help them to effortlessly build an infrastructure for large-scale phishing campaigns. By extracting phishing toolkits, cybersecurity analysts can dissect the mechanism behind the phishing attack and figure out where the exfiltrated data is sent. In addition, a thorough examination of phishing toolkits can help forensic analysts detect digital traces that might lead to their developers.
The functionality of phishing kits is not just limited to generating fake websites or pages to steal user data. Some drop malicious payloads on the victim’s system. Sellers of the phishing toolkits sometimes use this technique to deceive their buyers and attempt to mint money twice. By using a special script embedded in the text body of the phishing kit, they can direct the stolen data to their network hosts or also intercept access to their customers’ hosting service.
Stolen Data Collection Methodology
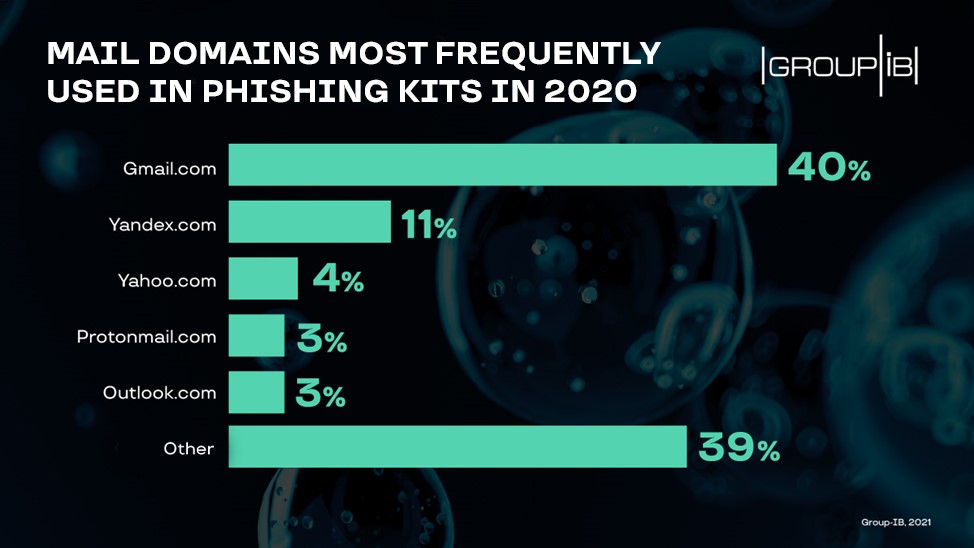
For collecting the data, cybercriminals mainly use free email services to which all the information harvested on phishing websites is automatically sent. This tactic is so widely used that it accounts for 66% of the total number of emails found in the phishing toolkits. Additionally, the analysis also shows that most email accounts detected were created using Gmail and Yandex mailing services.
The analysts further divided alternative ways for cybercriminals to obtain data into two major categories:
- Local: Where the data is stored in a file located on the phishing resource itself.
- Remote: Where it is sent to a different server (like a C2 server).
Cybercriminals actively use legitimate services to obtain compromised data. However, a new trend was recorded over the reporting period: successful leveraging of Google Forms.
Not only are Google Forms easy to create, but they also come with the advantage of being hosted under the google.com domain which helps gain potential victims’ trust. Cybersecurity awareness training often teaches users to look out for mistakes or tricks that can betray a scam. However, when the shared URL begins with docs.google.com, it might just be enough to fool people into entering their password and other credentials required in the form.
Yaroslav Kargalev, Deputy Head of CERT-GIB, said,
Phishing kits have changed the rules of the game in this segment of the fight against cybercrime. In the past, cybercriminals stopped their campaigns after the fraudulent resources had been blocked and quickly switched to other brands. Today, they automate their attacks and instantly replace the blocked phishing websites with new web pages. In turn, automating such attacks leads to the spread of more complex social engineering used in large-scale attacks rather than separate incidents, as used to be the case. This keeps one of the oldest cybercriminal professions afloat.
The traditional approach consisting of monitoring and blocking phishing websites is far from enough today. Companies must identify all the elements of the attackers’ infrastructure and block the entire network of fraudulent resources than separate modules. For this, you need to have a Cyber Threat Intelligence (CTI) analyst on board who can analyze phishing and other forms of attacks, and attribute them to a specific cybercriminal group targeting your firm.
However, the employment gap in cybersecurity is currently concerning, with 3.5 million unfilled positions globally. So, if you are interestedin training your employees or gaining hands-on knowledge in the CTI field, check out EC-Council’s Certified Threat Intelligence Analyst (CTIA) course.
Related News:
Phone Numbers of 533 Mn Facebook Users on Sale via Telegram Bot






















