
On 24th August, 79AD, the eruption of Mount Vesuvius caught the 20,000 local residents of Pompeii off guard, burying the magnificent Roman trading town for the next 1520 years. Walking through the archaeological site today, we can’t help but feel the distress of the people whose petrified casts we see, frozen in the moment of horror when the city was destroyed. Yet there is something curious too about the scenes.
By Julia O’Toole, Founder and CEO of MyCena Security Solutions
We now know there were clear signs of the impending eruption: an earthquake in 59AD, ground raising up, underground springs drying up, and animals acting strangely. Yet right up to the fatal eruption, the city was bustling with activity. In the final years of Pompeii, the rich had kept pouring their savings into a building and decorating their villas and gardens, enriching them with beautiful fountains and baths that were connected to a state-of-the-art city water heating and distribution system, all as if nothing had happened. But why did people keep building on an obviously active volcano? Was it a race for social status? The certainty that the gods would protect the city? Collective blindness?
Why cybersecurity feels like Pompeii
In the last few months, we have witnessed a couple of big eruptions in cybersecurity. From the SolarWinds hack to the Microsoft Exchange Servers vulnerabilities exploitation, we discovered how one intern’s password led to a massive operation of cyber-espionage, how a remote access password almost led to the water poisoning of a 20,000 people town, how unpatched vulnerabilities at one software supplier led, in a matter of days, to a massive and indiscriminate supply-chain attack on hundreds of thousands of customers.
The terrifying part of the story isn’t the breaches themselves. No system is unbreachable, as hackers go around firewalls, antivirus, IDS, IPS, WAF, DLP, MFA … and look for an easy door to open. What’s terrifying is that after they set foot inside a network, hackers can go unnoticed for very long periods of time yet launch rapid attacks from the inside of critical services, Fortune 500 companies, cybersecurity leaders, federal agencies… not just once, but time and time again.
Those eruptions are the emerging signs of a more profound problem at the heart of our digital infrastructure: the over-bearing presence of single points of failure, all from which a domino effect can start and wipe out entire sections of our networks. Yet as supply-chain integration increases, the number and impact of single points of failure grow exponentially too, to the point some fear “the” single eruption that can wipe out everything that was built before.
If cyber-resilience is the aim, segmentation is the game
After the recent attacks, the consensus is we need to build back better. But to build back stronger will require more than shuffling a few policies and technologies at the fringe. It requires building cyber-resilience from the core. For that, we need to go back to the drawing board and remove single points of failure from our digital infrastructure so that single wipe-out events can never happen again.
Thankfully, going back to the drawing board doesn’t require reinventing the wheel. Cybersecurity can take a leaf out of the best practices in buildings security. For example, to prevent a fire started in one room from spreading and burning the rest of the building, many countries have fire door regulations in place. To prevent a breach in one system from spreading and infecting the rest of the digital infrastructure, we could have systems segmentation regulations, which would require the segmentation of networks into smaller clusters, separate strong unique access for each cluster, and credentials decentralization to remove single points of access (and failure).
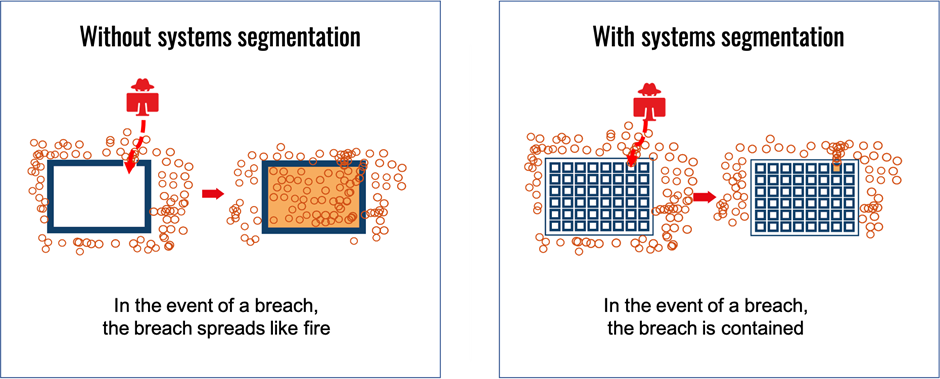
If that all seems logical, the question remains – how to segment and control each access individually when people can’t remember dozens of strong passwords like 7%uet£%Er@fhRAw4853?
Rediscovering Christopher Alexander and the system-thinking human-centred approach
There is a classic trap in mathematics. You start solving one piece of a complex equation and by the time you get so deep into your calculations, you forget which equation you were trying to solve in the first place. This happened with passwords. People were so focused on solving one problem – people forgetting passwords – that they lost sight of the stakes and the main goal, which is segmentation.
To avoid this trap, let’s turn to one of the most influential thinkers on complex networks: British-American architect and design theorist Christopher Alexander. As an introduction, Alexander is regarded as the father of the pattern language movement. Trained in mathematics, biology, physics, cognition, computer science, and architecture, his work has influenced programming language design, modular programming, object-oriented programming, software engineering, agile software development, and other design methodologies. Throughout the 1960s and 1970s, his seminal book “Notes on the Synthesis of Form” was considered required reading for researchers in computer science.
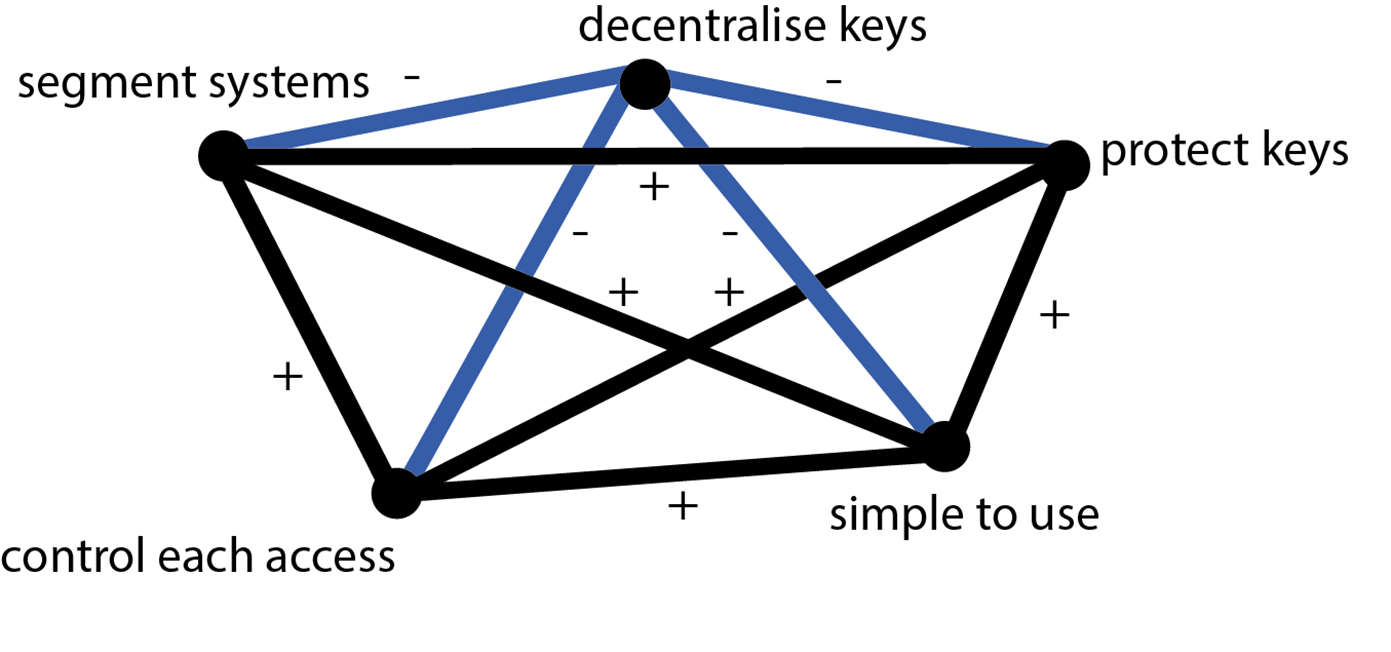
Central to Alexander’s work is the concern for “design wholeness”, which I call a system-thinking human-centred approach. For a design to solve a complex problem, all the conditions critical to the solution have to be satisfied individually, simultaneously and be easy to use by humans. In our cyber-resilience challenge, this would mean segment systems, control each system access individually and independently, decentralize access keys so they don’t all sit in the same basket, protect access keys so that only the rightful owner can access and use them, and make the whole system simple to use so that people can quickly access any system whenever they need, all at the same time. This challenge is like solving complex mathematical equations, except the solution has to come in a design form. Below is what a good solution to our cyber-resilience challenge would look like. The positive (+) inferences between two conditions mean they co-exist. For example, satisfying the condition “protect keys” does not cancel out the condition “segment systems”, and vice-versa.
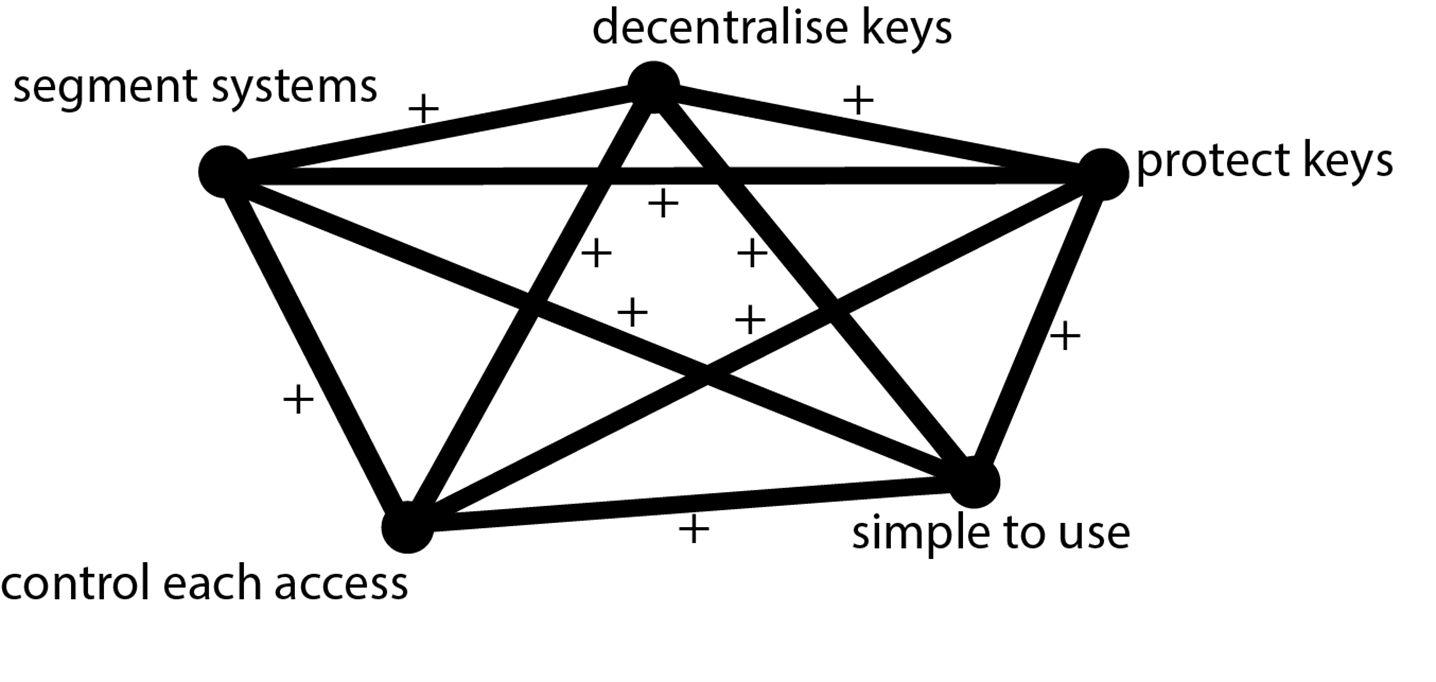
Three situations encountered in companies today
Now let’s compare this challenge with three situations often encountered in companies today:
Situation 1:
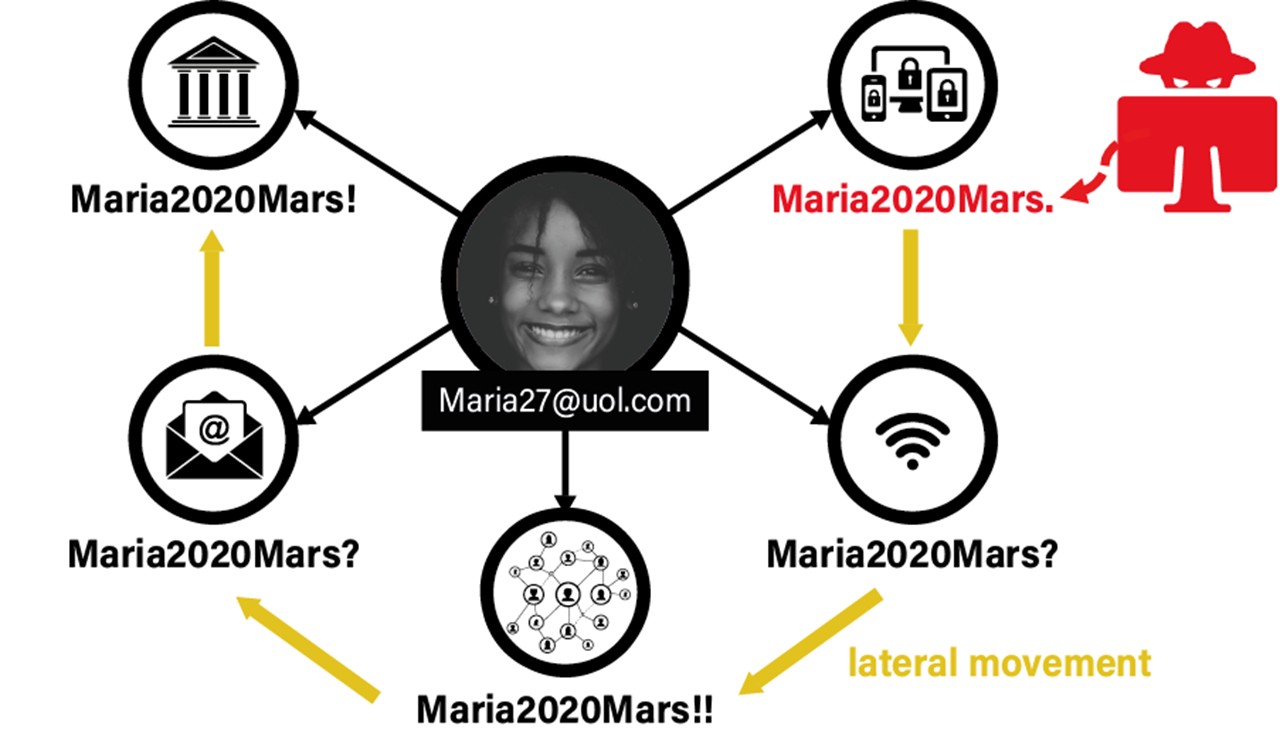
The company lets employees create their own passwords to access company assets and systems… Since people can’t remember their passwords, they use simple passwords like 123456, or recycled patterns with endings like 123, 123., 123!, 123?. Therefore, there is no segmentation of systems as all passwords are easy to crack using common credentials attacks like credentials stuffing, social engineering, brute force, password spraying, dictionary attacks… As soon as a hacker gets hold of one password, they can quickly find the others and move laterally through the network. Therefore, handing over credentials security and management to employees does not satisfy any of the conditions and is not a solution to the cyber-resilience challenge.
Situation 2:
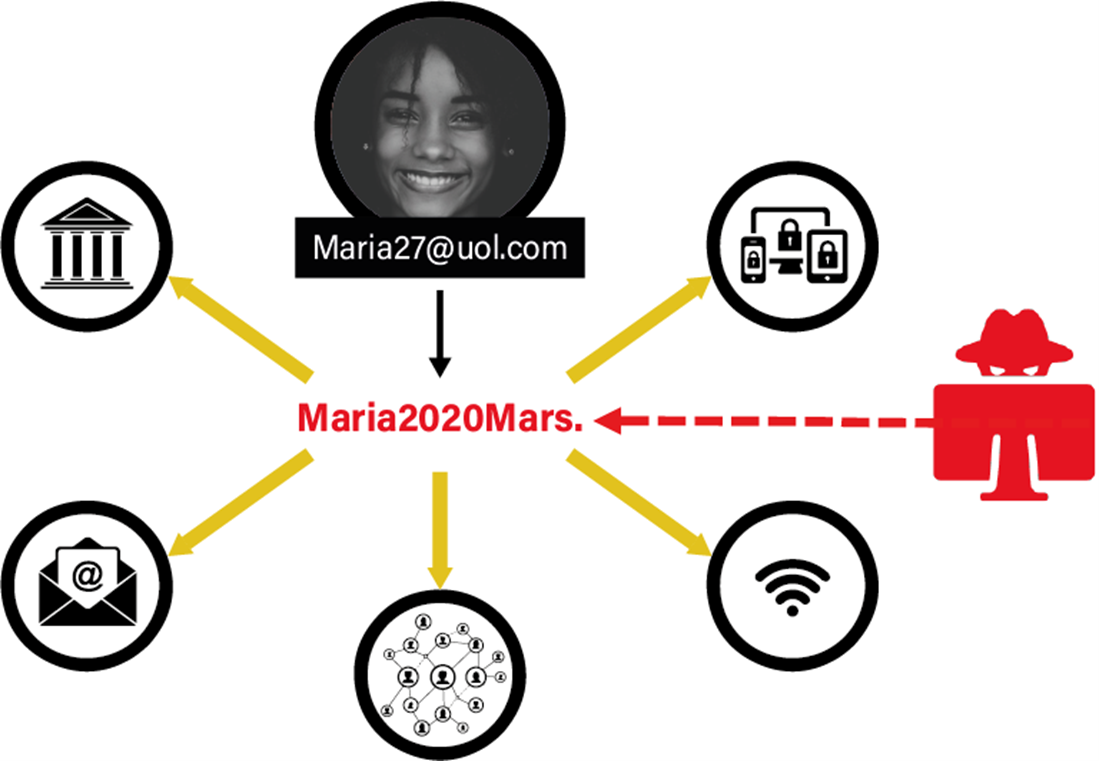
The company creates strong passwords for each system but then puts them behind a single point of access (Single Sign On, passwords managers, identity, excel spreadsheet, notebook, post-its, browser…) which contradicts “segment systems” and “control each access”, meaning this is not a solution to the cyber-resilience challenge.
Situation 3:
The company uses MFA and a zero-trust approach. This is the same configuration as situation 2, but with extra verification. MFA provides extra verification on the perimeter of the system. But if the hacker intercepts tokens (e.g. SIM swap) to get inside the network, they can access everything at once. A zero-trust approach provides extra layers of verification inside the network. But if the hacker steals your identity (e.g. deepfakes) they can pass every security check and access everything. Since neither satisfies the condition “decentralize keys”, neither is a solution to the cyber-resilience challenge.
How to solve complex design problems using the mathematical scarcity of good sequences
As with complex mathematical problems, people can spend years looking for solutions without finding them. It took almost 100 years and many failed attempts by generations of mathematicians before Grigori Perelman solved the Poincaré conjecture in 2003.
Thankfully, Alexander offers us a pragmatic approach to find good design solutions. In his seminal 4-tome book series which took him and his team 30 years to write and publish, ‘The Nature of Order, Volume 2 The Process of Creating Life, The Sequence of Unfolding §7’, he calls it “the Mathematical Scarcity of Good Sequences”. To solve complex design problems you can, through tests and trials, identify and eliminate from the trillions of possible sequences, those including previously found bad subsequences, which narrows down the range of potential good sequences. The main quality of good sequences is their stability: once a good sequence, always a good sequence. They are unambiguously and timelessly backtrack-free, which means there will never in the future be a need to backtrack and undo the process. If backtracking is necessary, it means the sequence was bad in the first place and should have been discarded.
This experimental approach is actually how people have designed and built houses, towns, and cities throughout centuries, each generation of builders standing on the shoulders of previous generations, incrementally solving new design problems and creating new patterns. However, this slow development of form has been compromised in recent decades by the rapid increase in the quantity, complexity, and difficulty of new problems. With no one to turn to for help, individual builders have had to solve contemporary design problems which lie beyond a single individual’s grasp.
Borrowing patterns from nature and the past
If there is no one to turn to, then where should one look for answers or inspiration? Nature is a good place to start, as it abounds with good sequences everyone can see and use. Another place to look for and identify good patterns is in the past. Interestingly, once you engage in the process of identifying good sequences for complex design problems, it becomes second nature. That’s why inventors often unexpectedly trip over the missing piece of the puzzle they have long been looking for.
I had been looking for over 20 years (thankfully not 100) to solve my own password problems using mathematics, neuroscience, and technology, when I tripped over the missing piece during a visit to the 3000-year-old ancient Greek city of Mycenae. To enter the city, you had to pass through a first gate called the Lion’s Gate; once inside the city, you had to pass a second gate to get to the garrison, and once inside the garrison’s quarter, you had to pass the third gate to get to the king’s palace.
Suddenly the penny dropped: a password is a key. No one ever cuts or remembers how to cut a key before they open a door. People just pick the right key and use it. By using a method of access for structured stored data, we could ensure only the rightful owner could access their own keys. A good sequence to the cyber-resilience design challenge could therefore include a local private digital credentials fortress which only the owner can access to find their keys, after passing multiple layers of security like in the ancient city, as shown below. This sequence satisfies the condition “protect keys” and, at the same time, satisfies the conditions “segment systems,” “control access” and decentralize keys.”
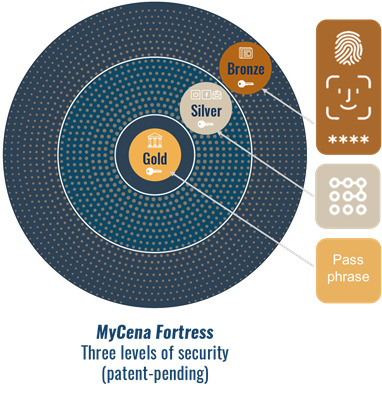
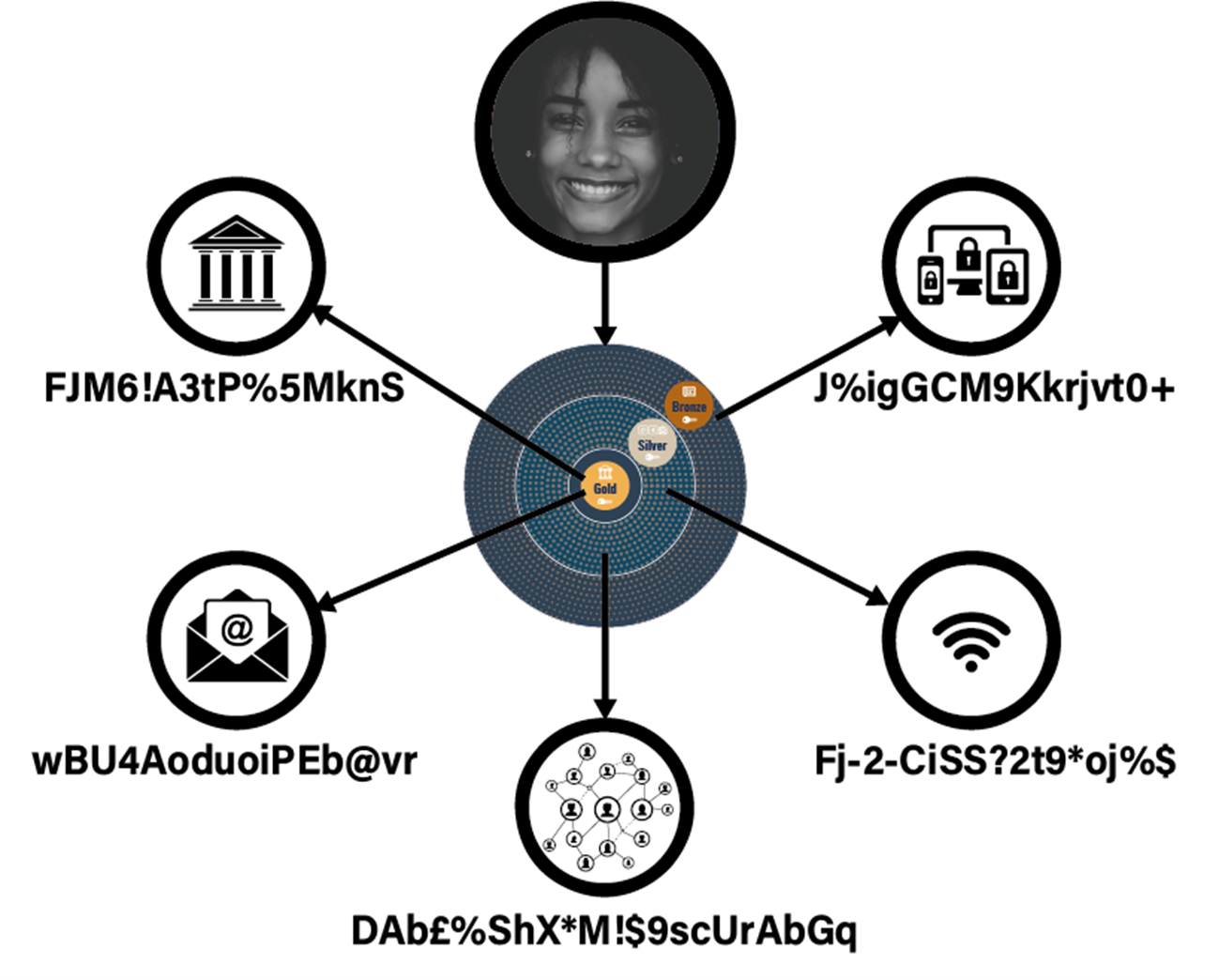
The illustration below shows an absence of a master key, central repository, or single points of failure in the model. You can keep as many keys as there are segmented systems. Each system key is strong, unique, and totally independent from the others. You can segregate and keep the most sensitive keys in the deepest and most secure levels. All keys are decentralized, locally encrypted, and only accessible by the owner.
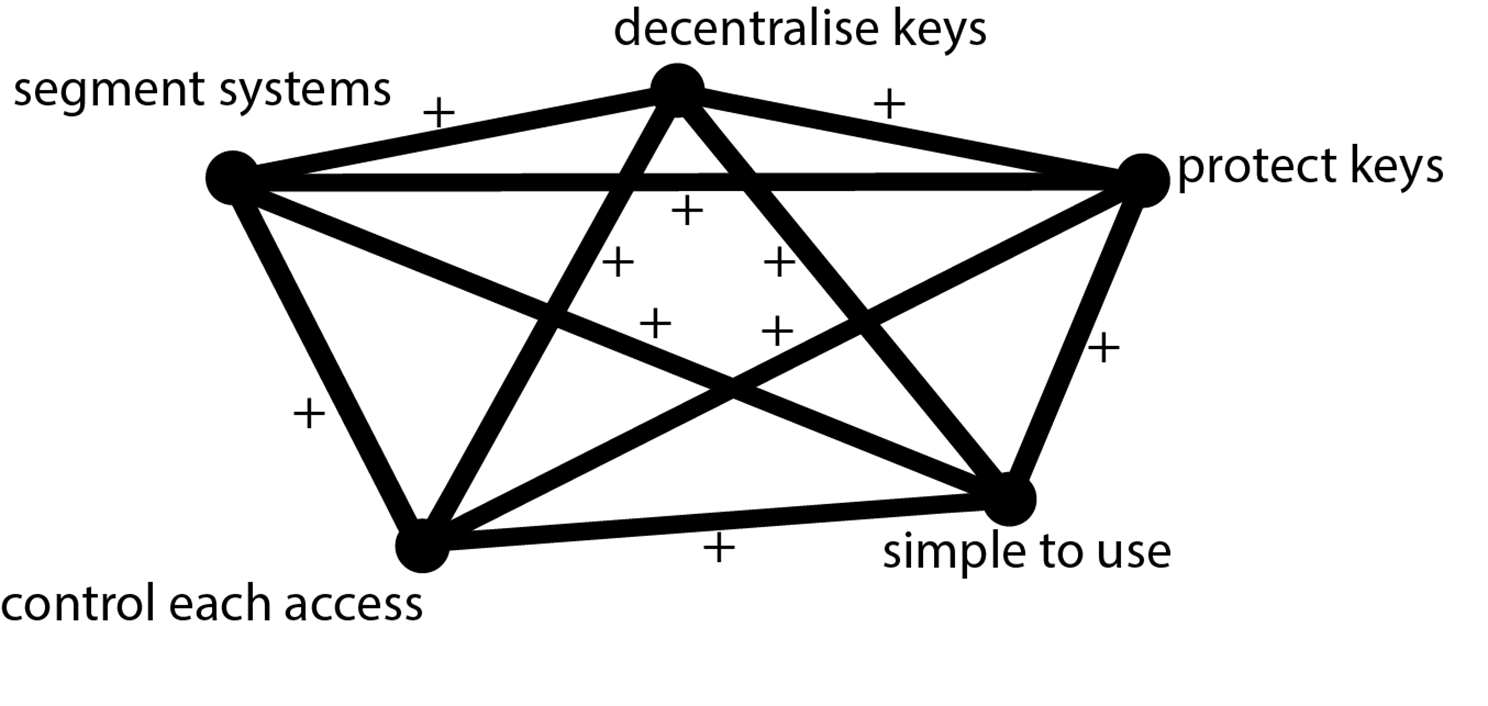
There is one last condition to satisfy in order to solve the cyber-resilience design challenge: it has to be simple to use. Here again, we used an iterative à la Alexander process and spent a few years working with our clients to find and develop the shortest path for the brain in daily situations. That includes no more passwords to create, remember, type, or see; working for all systems (IT, OT, IoT, ICS, legacy…), minimizing frictions on deployment, user enrolment, credentials distribution, daily management, setting roles and permissions, usage monitoring… Having satisfied the last condition, our system diagram now looks like this, satisfying all of the critical conditions for cyber-resilience.
Conclusion
Remember the moral of Aesop’s fable of the hare and the tortoise: “Slow and steady wins the race”. We believe that in the mad rush to take everything digital, it pays to step back and rethink cybersecurity with a more long-term, system-thinking human-centred approach.
There will be more and bigger eruptions in the months to come. As we witness hackers taking over networks by becoming super-admins time and again, the cost of not removing single points of failure (master key, SSO, centralized and privileged access, identity, super-admin accounts…) from your digital infrastructure could be fatal. To be cyber-resilient and reduce the risks of lateral movement, identity theft, ransomware attacks, supply-chain attacks… segmentation is key! The other advantage of moving away from the reach of single wipe-out events is that you can sleep without fearing “the next Pompeii.”
WRITE FOR CISO MAG
Do you want to write for CISO MAG? Please read our guidelines here.
About the Author
 Julia O’Toole is a French inventor and entrepreneur. She is the founder and CEO of MyCena Security Solutions. Using maths, neuroscience, and technology, Julia and her team research and design innovative and easy-to-use solutions to complex problems. She uses revolutionary ways to solve the biggest problem in cybersecurity: passwords.
Julia O’Toole is a French inventor and entrepreneur. She is the founder and CEO of MyCena Security Solutions. Using maths, neuroscience, and technology, Julia and her team research and design innovative and easy-to-use solutions to complex problems. She uses revolutionary ways to solve the biggest problem in cybersecurity: passwords.
Disclaimer
Views expressed in this article are personal. The facts, opinions, and language in the article do not reflect the views of CISO MAG and CISO MAG does not assume any responsibility or liability for the same.















