
It is observed that threat actors popularly use the password spray attack, not because of its high success rate (as per Microsoft, only 1% of these attacks are successful) but because it largely goes undetected for a substantial amount of time. It gets lost in the daily clutter of failed login attempts, especially in the current scenario of remote working. However, even with a low success rate, it’s worth noting that password spray attacks account for more than a third of account compromise in organizations worldwide. Thus, to further fortify the defenses against them, Microsoft’s Azure AD has now introduced advanced password spray detection that will act as an additional shield against password spray attacks.
Is Password Spray Another Term for Brute Force Attack?
No, both are different. Although password spray is similar to a brute force attack, the striking difference between the two is that brute force is a precisely targeted attack. The threat actor(s) go after specific users and cycle through as many passwords as possible, either by using a commonly used passwords dictionary or by implying social engineering tactics. The latter involves thorough research of the targeted person to check if they can guess the user’s password from their social behavior and information.
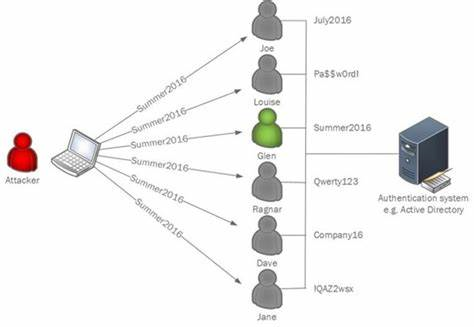
In password spray attacks, threat actor(s) obtain a list of accounts of the targeted organization and attempt to sign-in into all of them in a single go using a small subset (only one or two passwords daily) of the most popular, or most likely, passwords until they get a positive hit.
Evolution of Password Spray Detection
Initially, Microsoft, in its Azure Active Directory (AD), used only an investigative approach, which was based on constant monitoring. It detected a single password being attempted against hundreds of thousands of usernames from multiple IPs across the globe and informed the respective organizations of a malicious attempt of breaking in. But now Microsoft has gone a notch higher and adopted a more heuristic approach based on the learnings from its previous model, which was almost 98% successful as per the tech giant.
Related News:
Microsoft Tops the Chart for Being Most Imitated Brand for Phishing Attacks
Microsoft said, “Our data scientists started researching the use of these patterns (the ones detected from the previous approach) and additional data to train a new supervised machine learning system. We incorporated IP reputation, unfamiliar sign-in properties, and other deviations in account behavior. The results of this research led to this month’s release of the new password spray risk detection. This new machine learning detection yields a 100% increase in recall over the heuristic algorithm described above meaning it detects twice the number of compromised accounts of the previous algorithm. It does this while maintaining the previous algorithm’s amazing 98% precision — meaning if this algorithm says an account fell to password spray, it’s almost certain that it did.”
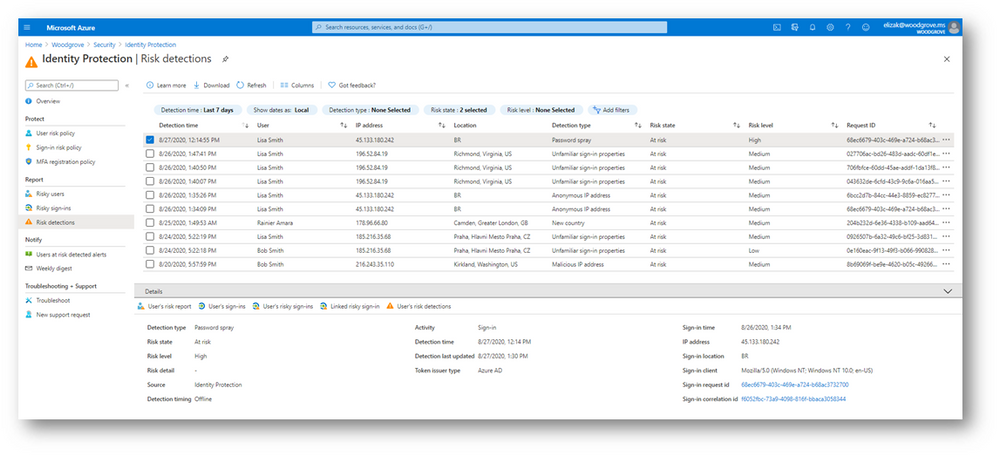
This new detection will be available for Azure AD Identity Protection customers in their Identity Protection portal and APIs, respectively. The following screenshot provides a sample of the new risk detection:
Related News:
CISA Advises Enterprises to Patch Two Critical Microsoft Vulnerabilities
Microsoft Offers $100,000 Bounty to Hack Its Azure Sphere Linux IoT OS






















