
Nyotron’s research team has discovered a new ransomware technique that goes undetected in most antivirus, anti-ransomware and Endpoint Detection and Response (EDR) solutions. The researchers have named it “RIplace”, as it bypasses latest security products by replacing all sensitive files on victim’s machine.
What’s different in RIplace Ransomware Technique?
Generally, all ransomwares follow a similar flow as shown below.
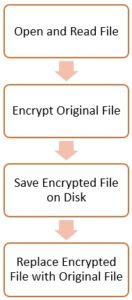
But the RIplace technique is different when it comes to the last step. It creates a new encrypted file and replaces both, the original and sensitive data files using the Rename request (specifically, IRP_MJ_SET_INFORMATION with FileInformationClass set to FileRenameInformation). The Rename operation is used widely by Microsoft and other security vendors to call filter drivers. If prior to calling Rename, DefineDosDevice (a legacy function that creates a symlink) function is called, then an arbitrary name can be passed as the device name, and the original file path, as the target to point on.
The RIPlace discovery team further stated that “the callback function filter driver fails to parse the destination path when using the common routine FltGetDestinationFileNameInformation. It returns an error when passing a DosDevice path (instead of returning the path, postprocessed); however, the Rename call succeeds. “
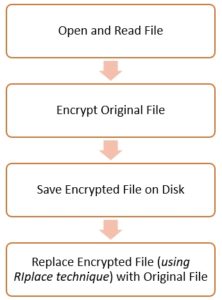
Using this technique, it is possible to maliciously encrypt files and bypass antivirus/anti-ransomware products that do not properly handle IRP_MJ_SET_INFORMATION callback.
Nyotron Raises the Red Flag
Nyotron told BleepingComputer that they tested RIPlace technique over a dozen vendors including Microsoft, Symantec, Sophos, McAfee, Carbon Black, Kaspersky, Trend Micro, Cylance, SentinelOne, Crowdstrike, PANW Traps, and Malwarebytes. They have followed the responsible disclosure policy by informing Microsoft and other security vendors and all relevant law enforcement and regulatory authorities.
Nyotron also released a demo video of the RIPlace evasion technique with Windows Controlled Folder Access (CFA) and announced a free testing tool any organization can download to check its systems.















