
Today, 266 vulnerabilities are associated with ransomware, and attackers are increasingly exploiting these weaknesses to launch devastating ransomware attacks. Therefore, identifying and remediating these vulnerabilities needs to be a critical priority for organizations if they wish to remain safe from ransomware attacks.
By Ram Movva, Chairman and Co-founder of Cyber Security Works
We have witnessed dangerously disruptive ransomware attacks in 2021. The ransomware attacks on Colonial Pipeline, JBS USA Holdings, Kaseya, and Accenture — the most recent victim of LockBit — are proof that the lack of cyber hygiene is rampant. These attacks highlight the need for the continual assessment of vulnerabilities and the prioritization of remediation.
As our research in ransomware expands, we have updated our Q1 report with new ransomware markers and emerging trends that would help organizations worldwide to stay a step ahead of attackers and proactively defend themselves against such attacks.
In the Q2 Index Update, we highlight the following:
- Insights about vulnerabilities that have recently become associated with ransomware
- New Advanced Persistent Threat (APT) groups using ransomware in their attack arsenal
- Newly discovered ransomware families
- Categories of weaknesses that have contributed vulnerabilities to ransomware
- Emerging ransomware trends
New Vulnerabilities in the Ransomware Arsenal
In this quarter, our research shows that six vulnerabilities have become associated with seven ransomware strains; among them are the infamous Darkside, Conti, FiveHands, and the newly christened, Qlocker.
With this update, the total number of vulnerabilities associated with ransomware has increased to 266. We have also noticed a 1.5% increase in the number of actively exploited vulnerabilities that are trending currently, reiterating that a risk-based approach for the remediation of vulnerabilities is the need of the hour.
One of the most compelling observations during this quarter was the exploitation of zero-day vulnerabilities even before vendors published their discovery or released patches.
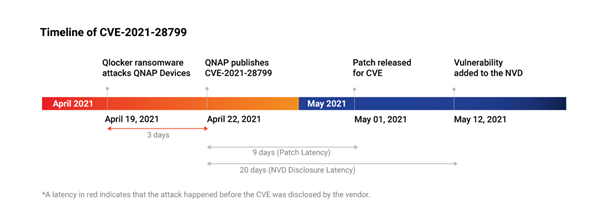
On April 19, 2021, thousands of QNAP devices were attacked by Qlocker, causing service disruptions and data loss for its users. Qlocker had compromised CVE-2021-28799, a QNAP zero-day vulnerability discovered only on April 22, 2021—for which a patch was published on May 1, 2021. Meanwhile, the attackers had already made more than $350,000 in ransom money, even while the vendor was still investigating the incident. The National Vulnerability Database (NVD) released details about this vulnerability 11 days after the patch was released.
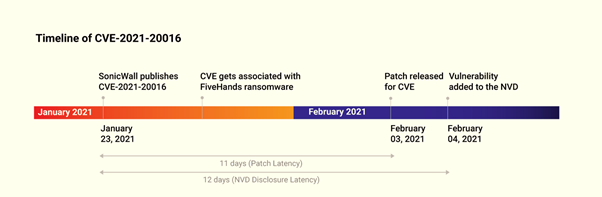
The FiveHands ransomware attack on SonicWall Virtual Private Network (VPN) devices is yet another example that showcases the need for a risk-based approach. In this case, SonicWall had published details about CVE-2021-20016 on January 23, 2021, and the patch was scheduled to be released on February 03, 2021. However, attackers struck before the patch was published. The NVD added the vulnerability to its database on February 04, 2021.
Both incidents highlight the following:
- Organizations that depend only on updates released by the NVD to plan their remediation and patch management need to rethink their strategy and adopt a risk-based approach to mitigate trending threats.
- With ransomware attackers going after zero-day vulnerabilities, vendors must proactively release patches without delays.
- Software developers need to be more mindful about coding errors and misconfigurations, ensuring they do not introduce weaknesses that attackers could compromise to launch crippling attacks.
Vulnerability Analyses
Exploit Type
Our research also focuses on the type of exploit linked to ransomware-related vulnerabilities. For instance, Remote Code Execution (RCE) and Privilege Escalation (PE) are the most dangerous vulnerabilities that attackers weaponize and exploit.
Since the publication of the ransomware report in February 2021, we have observed that 43 vulnerabilities have become associated with ransomware this year, and 35% (15 vulnerabilities) have been categorized as RCE/PE exploit types. In this quarterly update, we observed that RCE/web application exploit CVE-2018-13374 has been associated with Conti ransomware.
Overall, 40% of vulnerabilities (107) tied to ransomware are categorized as RCE/PE exploits. Our recommendation to organizations is to prioritize these vulnerabilities and patch them first.
Low-Scoring Vulnerabilities
Low-scoring vulnerabilities deceptively fly under the radar. Security teams tend to sideline low-scoring vulnerabilities and patch vulnerabilities based only on their Common Vulnerability Scoring System (CVSS) version3 (v3) or version2 (v2) scores. Such organizations will still be vulnerable to ransomware attacks because 59% of the vulnerabilities associated with ransomware are low-scoring* ones.
In our quarterly update, we have seen a 3.9% increase in low-scoring vulnerabilities linked to ransomware. While security teams may overlook these vulnerabilities, risk-based platforms will flag these vulnerabilities as high-risk despite the low score provided by the NVD. However, many organizations do not use or remain unaware of such tools, leaving their low-scoring vulnerabilities unpatched and their network open to a ransomware attack.
*CVSS v2 scores less than eight were considered low-scoring for the ransomware research report.
Actively Exploited Vulnerabilities
While vulnerabilities that have become associated with ransomware should always be considered high risk and must be prioritized for remediation, we also look at those Common Vulnerabilities and Exposures (CVEs) that are currently trending in hacker channels and being exploited in the wild.
At present, 134 vulnerabilities are being actively exploited. Security teams will need to move these vulnerabilities to the top of their patching list because these weaknesses are being increasingly compromised to launch damaging ransomware attacks.
New APT Groups
We have been observing an increase in APT group attacks since the beginning of this year. From SolarWinds to DarkSide’s attack on the Colonial Pipeline, APT groups have targeted critical industries and sectors and have added ransomware to their arsenal to mount disruptive attacks.
In this quarter, we have noted a 17% increase in the number of APT groups adopting ransomware as part of their arsenal to mount attacks on their targets. This brings the total number of APT groups with ransomware associations to 40.
New Ransomware Families
This quarter also brought about a 4.2% increase in ransomware families, with six new families joining the fray. Our findings show that the Crypwall ransomware family retains its position as the biggest ransomware family in the world, with 66 CVEs within its fold. In this quarter, we have also noted that the Cerber strain has overtaken Locky with 65 CVEs tied to ransomware.
Comparatively, new ransomware families are focused on much smaller vulnerability packages for exploitation. For instance, Apostle, DarkRadiation, FiveHands, and Qlocker exploit one vulnerability each. The Epsilon Red Group has three CVE associations, DarkSide has four associations, and Pay2Key has five associations.
New CWE Categories
Significantly, we have spotted two new Common Weakness Enumeration (CWE) categories during our research—CWE-134 (Use of Externally Controlled Format String) and CWE-732 (Incorrect Permission Assignment for Critical Resource).
CWE-134 is a weakness that, when combined with an unauthenticated RCE vector, can directly allow hackers to access the victim’s machine. Also, attackers can use these CWEs along with others in a chain to achieve their malicious motives.
CWE-732 leads to incorrect Permission Assignment for Critical Resource that can result in the exposure of sensitive information. It exposes VPN credentials in cleartext or an easily readable format, thereby allowing the VPN to be easily compromised. There is also a strong possibility of attackers using attack chaining to infiltrate the victim’s network. Software developers need to ensure that they do not introduce these weaknesses in their products while they write code.
Old Vulnerabilities
There has been a marginal increase in the number of old vulnerabilities that have recently become associated with ransomware. CVE-2017-1000253, CVE-2018-13374, and CVE-2019-1579 have been linked to DarkRadiation, Conti, and Pay2Key, respectively, in this quarter. This brings the total count of older vulnerabilities (published in or before 2020) associated with ransomware to 255, which is 95% of the total number of ransomware vulnerabilities.
The Way Forward
The most recent ransomware attacks have been so disruptive that they are considered acts of war, prompting world leaders to politicize these attacks with those countries where the ransomware seems to have originated.
Based on our research, ransomware vulnerabilities have been steadily increasing each quarter, and attackers are finding innovative ways to compromise and exploit weaknesses in software products and devices. As we head into Q3, we will be tracking zero-day exploits and the association between APT groups and ransomware.
Organizations can combat ransomware only with accurate vulnerability data aligned with the relevant threat context. A risk-based approach to detect, prioritize, and remediate these vulnerabilities would keep the attackers at bay. Our recommendation would be to adopt continuous vulnerability management to help organizations mitigate ransomware threats, even as they trend.
Watch out for our next quarterly update to get the latest statistics, exploits, and trends on ransomware!
Ransomware Research
RiskSense, a risk-based vulnerability management company (recently acquired by Ivanti), has been tracking ransomware attacks since 2019 — when they published their first report. In 2020, RiskSense, along with Cyber Security Works, investigated and identified the vulnerabilities tied to ransomware, and the Spotlight Report was published in February 2021. Since the vulnerabilities associated with ransomware have been steadily increasing, we have decided to release quarterly reports with updates on important metrics. The next quarterly report is due in October 2021.
About the Author
 Ram Movva, the Chairman and Co-founder of Cyber Security Works (CSW), is an industry expert in offensive security and intrusion detection. With a master’s degree from Georgia Tech, Movva was with TIBCO for over a decade. He was also part of the founding team at RiskSense, a risk-based vulnerability management company. After spending 15 years in the U.S., Movva co-founded CSW in 2008. Under his strategic leadership, CSW has enabled companies worldwide to improve their security posture.
Ram Movva, the Chairman and Co-founder of Cyber Security Works (CSW), is an industry expert in offensive security and intrusion detection. With a master’s degree from Georgia Tech, Movva was with TIBCO for over a decade. He was also part of the founding team at RiskSense, a risk-based vulnerability management company. After spending 15 years in the U.S., Movva co-founded CSW in 2008. Under his strategic leadership, CSW has enabled companies worldwide to improve their security posture.
Disclaimer
Views expressed in this article are personal. The facts, opinions, and language in the article do not reflect the views of CISO MAG and CISO MAG does not assume any responsibility or liability for the same.






















