
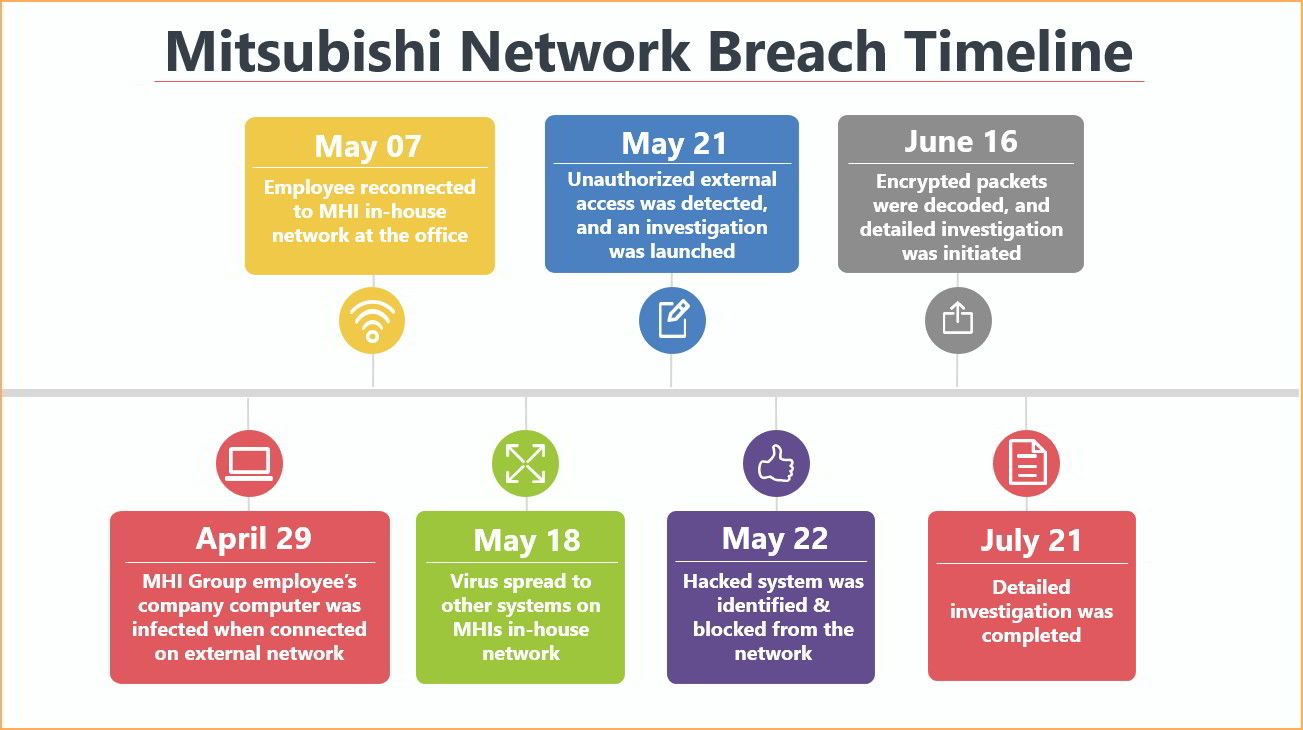
Mitsubishi Heavy Industries (MHI Group) has confirmed a third-party unauthorized network access to its systems located in the Nagoya region of Japan. The network breach was observed on May 21, by its IT team when an unauthorized external communication was detected on a Group server located in Nagoya. As per reports from the MHI Group, no confidential personal or business data was compromised in this network breach.
Key Highlights
- MHI Group confirmed that its network system in Nagoya, Japan, was accessed by an unauthorized third-party.
- The hack took place in the form of social engineering through social media misuse.
- At the time of the incident, there was no preventive protocol to restrict connection of a company mobile computer to an external network, this led to a successful social engineering compromise.
- As per the MHI Group’s internal investigation, no confidential personal or business data was compromised in this network breach and there was no reason to worry for its business affiliates.
How the Investigation Unfolded
Upon discovery of the unauthorized access, the IT team instantaneously launched an internal investigation to find and curb further damages. In a day’s time, they were able to identify the source of the hack and the affected stakeholders by analyzing the Nagoya region’s unauthorized data communications. The affected systems were immediately blocked from the network to stop the spread.
The MHI Group has operations across various critical projects related to power systems, aircraft, defense, and space. Thus, they store a lot of confidential and highly sensitive data which, if compromised, would have resulted in a major setback to the technology giant.
Cause of the Hack
The company in its announcement attributed this incident to being a social engineering attack carried out in the form of social media misuse. According to a detailed analysis, an MHI Group employee connected to an external network while working from home on April 29. Instead of using a secured MHI in-house network, the employee used a social networking service (SNS) to connect. It was here that he unknowingly downloaded a virus-infected file from a third-party, which infected the employee’s company mobile computer. Further, on May 7, when the employee joined back and connected on the in-house MHI Group network, the virus entered into its internal network.
Within the next 10 days, it began spreading to the other systems on the MHIs in-house network and started exfiltrating data in the form of encrypted packets. On carefully decoding the encrypted data packets, it was found that the leaked information consisted mainly of employees’ personal data (names and email addresses) using the MHI Group network. Additionally, other information including server logs, communication packets, server setting information, and IT-related information of the Nagoya region network was also leaked.
The Way Forward
The investigation precisely pointed to the cause and spread of this network breach. At the time of the incident, there was no preventive protocol or measures to restrict the connection of a company mobile computer to an external network, which led to a successful social engineering compromise. Thus, going forward whenever an employee wants to connect a company’s computer to an external network, it can be only done through an in-house virtual private network (VPN) connection.
Similarly, while investigating the cause of the spread, the IT team found out that “privileged local accounts of several servers within the affected area used the identical password.” Hence, it is believed that these passwords were reused to log in to the other systems for spreading the infection. Thus, the IT team has now changed all the passwords of privileged local accounts so that no two remain the same.
Mitsubishi Heavy Industries has already informed all the affected stakeholders and are keeping them updated about the network breach investigation proceedings. Meanwhile, they are also strengthening and improving their internal monitoring systems to avoid similar incidents in the future.






















