
Researchers at Barracuda, a provider of cloud-enabled security solutions, has warned users about threat actors who create accounts with legitimate email services and use them to launch business email compromise (BEC) attacks. The researchers identified 6,170 malicious accounts that use Gmail, AOL, and other email service providers and were responsible for more than 100,000 BEC attacks on nearly 6,600 organizations since the beginning of 2020.
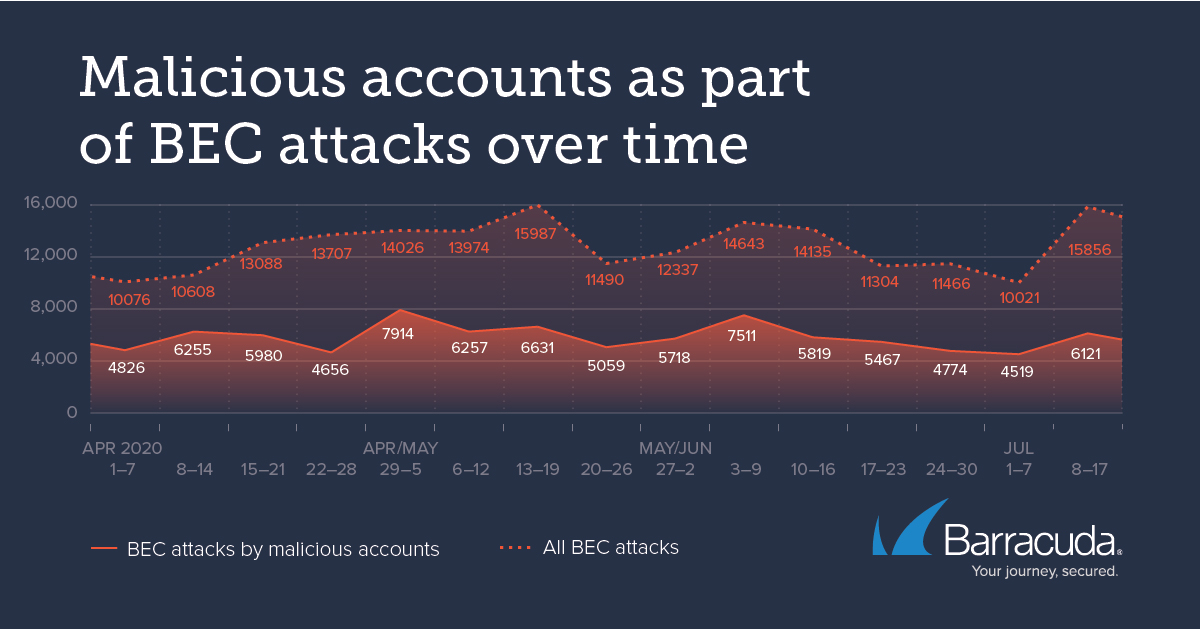
The number of organizations attacked by a malicious email account ranged from one to a single mass scale attack that impacted 256 organizations and the number of email attacks sent by a malicious account ranged from one to over 600 emails, with the average being only 19.
Malicious Email Accounts
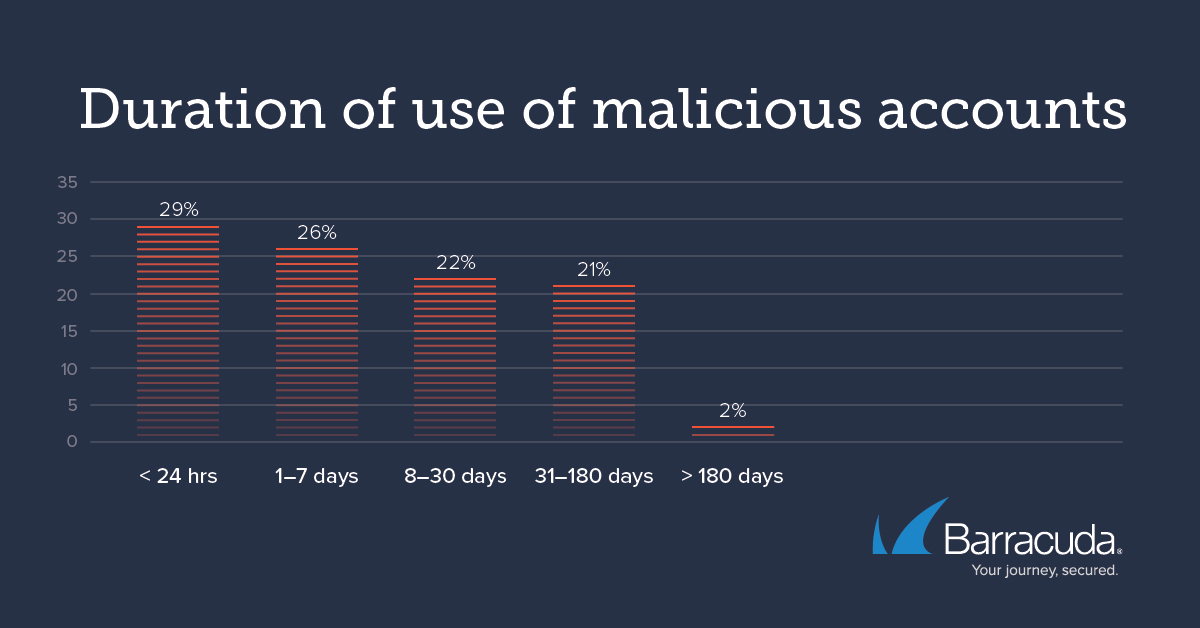
According to the researchers, malicious email accounts were responsible for 45% of all BEC attacks detected since April 1, 2020. Cybercriminals targeted several enterprises with multiple attacks from the same email accounts with specially crafted messages and URLs. Usually, attackers do not use their malicious accounts for a long period of time. Nearly 29% of malicious accounts were used for only a 24-hour period.
Cybercriminals design BEC attacks to bypass email gateways which is the reason why they only use each malicious account in a small number of attacks to avoid detection.
“While most malicious accounts are used by attackers for a short period of time, some cybercriminals used these accounts to launch attacks for over year. It is not unusual for cybercriminals to return and re-use an email address in attacks after a long break,” researchers said.
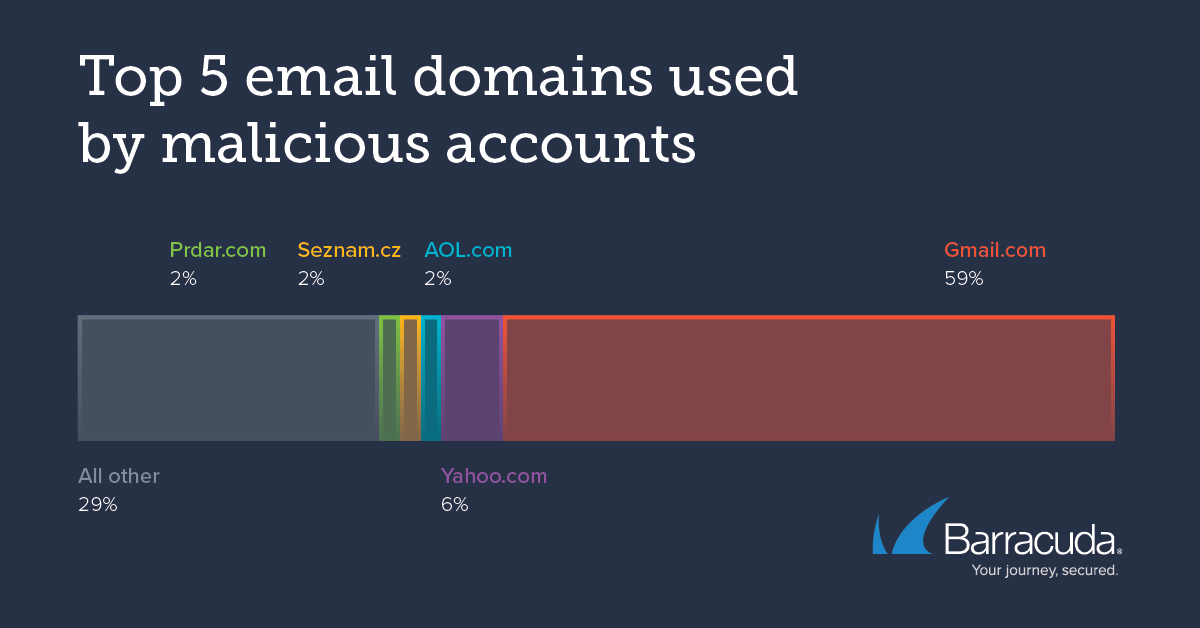
Attackers Prefer Gmail
Hackers prefer Gmail for their malicious accounts as it is easily-accessible, free, easy to register, and is able to pass through email security filters. Gmail accounted for 59% of all email domains used by cybercriminals. Yahoo! was the second most popular one, with 6% of all observed malicious account attacks.
“By nature, business email compromise is a highly targeted attack. After an initial research period, cybercriminals will impersonate an employee or trusted partner in an email attack. Usually, email is used first to establish contact and trust. Attackers will expect replies to their BEC attacks. Therefore, these attacks are usually very low volume and highly personalized to ensure a higher chance of reply,” researchers added.
How to Protect against Malicious Accounts
- Barracuda researchers concluded that identifying accounts used by attackers is not always easy. Threat actors use the technique of spoofing, wherein they pretend to be someone else in an attempt to gain illegitimate advantage. However, organizations can implement the following measures to avoid BEC attacks:Leveraging artificial intelligence to identify unusual senders, requests, and other communications will help detect BEC attacks and other fraud.
- Working with a vendor that can share this type of threat intelligence between different organizations in real time will allow for a greater level of protection.
- Train your users to recognize targeted phishing attacks. User training should always be part in your security posture. Make sure your employees know how to recognize messages that come from outside of your organization and are aware of the latest tactics used by cybercriminals.










