
With people becoming more dependent on the app ecosystem, threat actors targeting unwitting users with fake mobile apps to compromise their accounts or steal sensitive data have become rampant. Despite multiple security checks and scans, many counterfeits and malicious apps remain undetected and make their way to the app markets. Recently, Google removed 164 malicious applications for spreading disruptive ads, these apps were downloaded over 10 million times from the Play Store.
Hundreds of CopyCatz Apps!
Security experts from the WhiteOps Satori Threat Intelligence Team stated that they found a large number of fake mobile apps, dubbed “CopyCatz” on Google’s Play Store that were mimicking apps of popular brands to get downloads and then trick the users into seeing unwanted ads.
How the Apps Infect the Device
Scammers Victimized Popular Brands
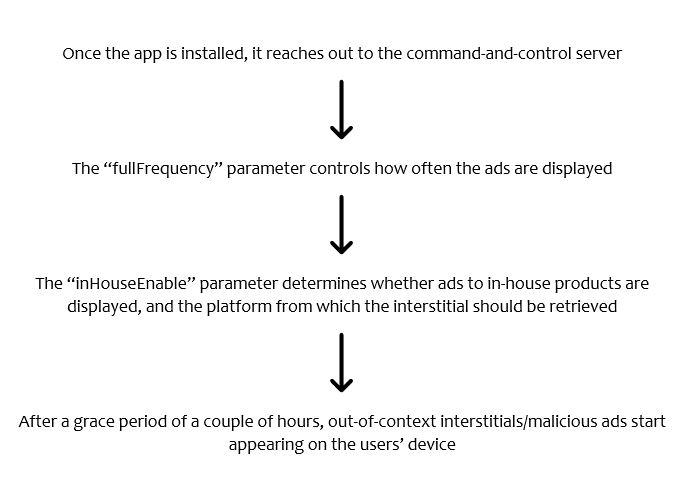
The researchers claimed that these fake apps contain a malicious code that displays out-of-context ads under the com.tdc.adservice package. It was found that these apps were controlled by a command-and-control JSON hosted on Dropbox, which was also a victim of CopyCatz operation. For instance, attackers used Assistive Touch 2020, which was a copy of the legitimate app – Assistive Touch, to trigger out-of-context ads on users’ devices.
“The URL of the JSON differs from app to app, but the structure is very similar, indicating the frequency of the ads and the Publisher ID to be used. Interestingly, the apps didn’t really try to cover their tracks. All of them have the open-source Evernote job scheduler embedded inside used as a persistence mechanism,” the researchers said.
Related Story: How to Spot Malicious or Fake Apps















