
The drive-by download attack volume has been witnessing a steep surge since 2018, with India being the second highest in terms of volume of attacks in the Asia Pacific region. The number is nearly three times higher than the regional and global average. In fact, India, together with Hong Kong and Singapore, continued to face high drive-by download attack volume, according to findings from the latest edition of Microsoft’s “Security Endpoint Threat Report 2019.” The country moved from 11th to second highest attack volume YoY across the region. The report also asserted that cybercriminals remain focused on stealing financial information or intellectual property.
India also recorded the second highest in cryptocurrency mining encounter rate in the Asia Pacific. Even though there has been a considerable decline in the cryptocurrency mining encounter rate compared to 2018, India was still 4.6 times higher than the regional and global average. During these attacks, victims’ computers were infected with cryptocurrency mining malware, allowing criminals to leverage the computing power of their computers without their knowledge.
Ransomware Hogs the Limelight
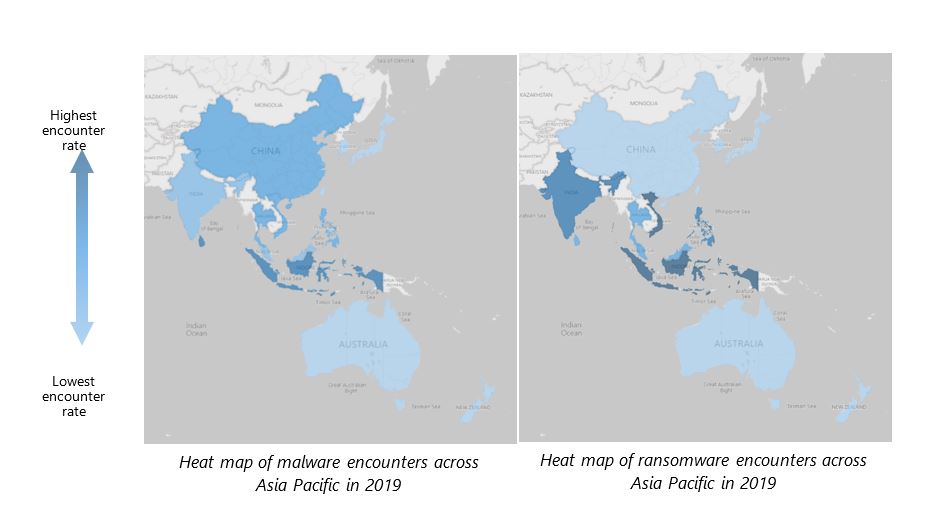
With respect to ransomware attacks, the report also highlighted that the Asia Pacific continued to experience a higher-than-average encounter rate for malware and ransomware attacks – 1.6 and 1.7 times higher than the rest of the world with India continuing to rank the third-highest for ransomware attacks. This was despite a 35% and 29% decrease in malware and ransomware encounters respectively over the past year.
Talking to CISO MAG about this alarming trend around ransomware, Keshav Dhakad, Group Head & Assistant General Counsel – Corporate, External & Legal Affairs, Microsoft India, said, “With the modes of attacks, cybercriminals are shifting their efforts to customized campaigns targeting specific to geographical areas, industries, and businesses.”

Countries with lowest encounter rate were Japan, New Zealand, and Australia.
In an ensuing statement, he added, “While overall cyber hygiene in India has improved, we believe there is more to be done. Typically, high malware encounters are a result of excessive usage of unlicensed and/or pirated software, and the proliferation of sites that illegitimately offer free software or content, such as video streaming. Consumer education is important – users should regularly patch and update programs and devices and be able to identify unsafe websites and illegitimate software.”
Cybersecurity in Times of Pandemic
COVID-19 has changed the cybersecurity landscape and remains the top-of-mind concern for individuals, organizations, and governments around the world. Ever since the onset of the pandemic, every country in the world has seen at least one COVID-19-themed attack with a continuous increase in the volume of successful attacks.
Among phishing messages seen globally each day, over 60,000 include COVID-19-related malicious attachments or malicious URLs with attackers impersonating establishments like the World Health Organization (WHO), Centers for Disease Control and Prevention (CDC), and the Department of Health.
Dhakad further explained, “Attacks have affected aid organizations, medical billing companies, manufacturing transport, government institutions, and educational software providers.”
He stated, “According to our data, we found that COVID-19 themed threats are mostly retreads of existing attacks that have been slightly altered to tie to the pandemic. This means that attackers have been pivoting their existing infrastructure, like ransomware, phishing, and other malware delivery tools, to include COVID-19 keywords, to capitalize on people’s fear. Once users click on these malicious links, attackers can infiltrate networks, steal information, and monetize their attacks.”
When asked, with COVID-19 seeing mass layoffs in several companies across the world and many of these may have been employees with privileged access. Doesn’t it pose a bigger insider threat challenge? Dhakad responded to this question: “Zero trust has been principal for organizations. It is important that all the accesses are verified. Fortunately, technology is well advanced to easily spot the anomalies. To stress again, zero trust policy must be mandatory for every organization during these times.”
Microsoft has also issued guidance for businesses and individuals:
Guidance for Businesses
- Safeguard employees with strong tools and infrastructure.
- Turn on two-factor authentication (2FA) or multi-factor authentication (MFA) as employees work from home.
- Include end-to-end encryption on trusted applications for audio/video calling and filesharing.
- Guide employees on how to identify phishing attempts and distinguish between official communications and suspicious messages.
Guidance for Individuals
- Update all devices with the latest security updates and ensure that an antivirus service is included.
- Watch out for malicious or compromised websites and avoid pirated content.
- Recognize and report suspected attack attempts.
- Verify all links and attachments before opening them.






















