
CISO MAG Survey: With increased digitalization and cloud migration, the corporate network now extends further out into the Internet — beyond the boundaries and firewalls of an organization. Even the concept of WAN and branch offices is extended. Partners, customers, suppliers, and employees connect to the corporate network from remote locations around the globe. Employees are working from home, especially under the prevalent COVID-19 situation, with social distancing becoming a norm. In that sense, it is a borderless network of interconnected networks. That ups the risk quotient for data security, network security, and endpoint security. The threat landscape has broadened to include threats to both, wired and wireless networks.
And then, there’s the “extended” network. Now that employees work from home, CISOs need to ask: How secure are home networks and endpoint devices? How many employees use company VPNs when working from home? With businesses outsourcing more functions to external third-parties, one needs to evaluate the infrastructure security of partners, suppliers, contractors, and the Nth party services (the entire supply chain). That calls for vendor risk assessments and management.
To gauge a deeper insight on the precautions companies are taking to combat the threats looming on the cyberspace, CISO MAG recently reached out to all the respondents who participated in the Network Security survey.
The key findings of the snap poll were:
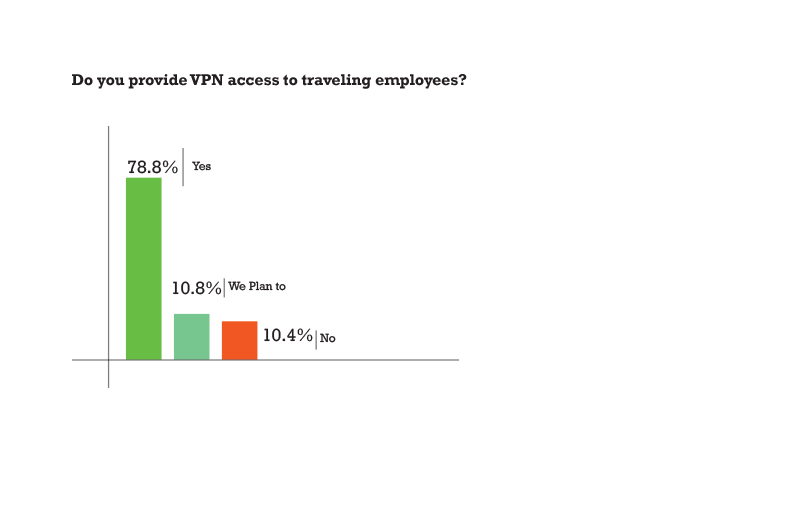
- Only 70% respondents stated that they were using company VPNs to securely log in to the company network, while 30% did not.
- Almost all the companies have secured endpoint devices (laptop/ phone) of employees.
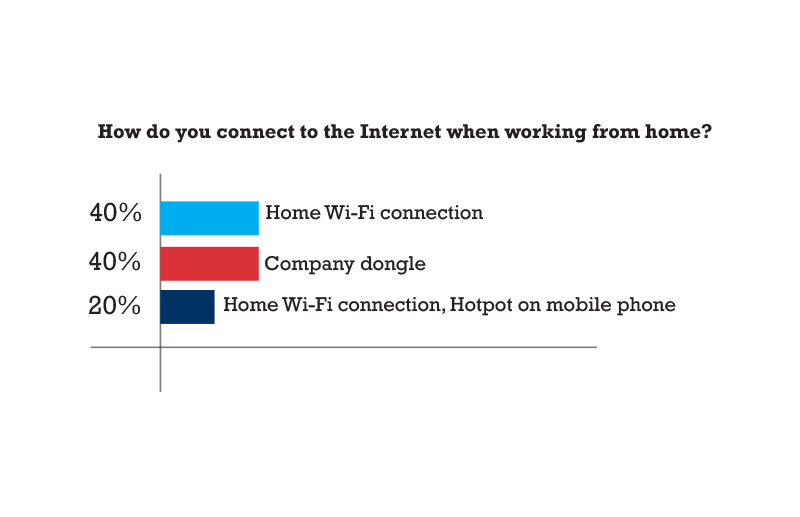
- Employees connect to the Internet either using home Wi-Fi connections or hotspot on mobile phone, while nearly 25% use company dongles along with home Wi-Fi and phone hotspot.
 With more and more software as a service (SaaS) models emerging, demand for security has increased at endpoints and even cloud systems.
With more and more software as a service (SaaS) models emerging, demand for security has increased at endpoints and even cloud systems.
CISO MAG Survey Findings:
- Even though the adoption of multiple layers of protection is more than 60%, several organizations rely on Antivirus and Firewall solutions from vendors at 36%.
- 6% of respondents suggest using an amalgamation of NAC policies including Identity Awareness, Centralized management and monitoring, and Ease of Deployment
- 5% companies still believe in some sort of a supervision on machine learning solutions on network traffic analysis
- When it comes to Perimeter Security, nearly 30% organizations consider securing Internet, WAN, LAN, and Cloud together
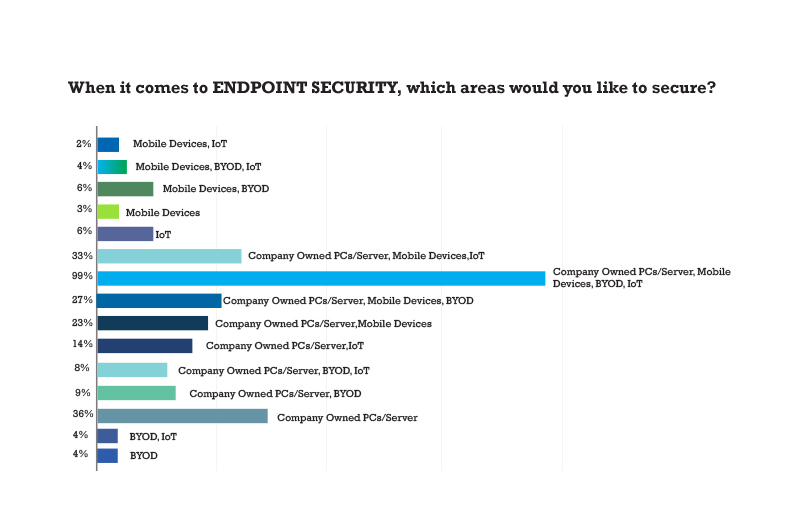
- 35% of respondents suggest that while securing Endpoints the key areas they focus on are Company Owned PCs/Server, Mobile Devices, BYOD, and IoT
- When it comes to intrusion sensors and modules, IPS tops the chart with 22.3% followed by UTM at 18.7% and IDS at 10.8%
- 7% opt for the hybrid approach for Network Security management 36.6% companies are already using SDN architecture while 63.3% are in the adoption stage
- 6% organizations still consider data security as the biggest security risk in cloud migration
The CISO MAG survey was based on the results of an online survey that was conducted by CISO MAG readers from EC-Council’s database. The respondents represent a cross-section of organizations from over 56 countries ranging from Argentina, Australia, U.S., U.K., Russia, India, France, Germany, Greece, Indonesia, Italy, Jordan, Kenya, Kuwait, Lebanon, Lithuania and even smaller countries and islands like Malawi, Mali, Nauru. Puerto Rico, Rwanda, Togo, Trinidad and Tobago, among several others. The survey was prepared in consultation with security experts and industry analysts.
Find the full survey report at: bit.ly/cisomagfree
Use coupon code CISOMAG19 at checkout for three months of free subscription of CISO MAG















