
Security researchers from ThreatFabric discovered a new banking Trojan “BlackRock,” which is targeting Android banking apps and also stealing login credentials from social networking sites, dating and cryptocurrency, and non-banking apps.
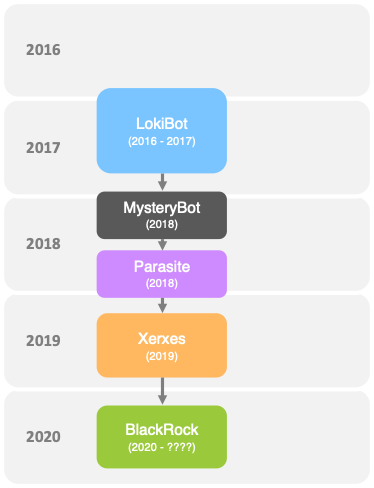
It is found that the malware targeted over 337 non-financial Android applications till now. The BlackRock malware is derived from the leaked code of the “Xerxes” banking malware, which is also a strain of the “LokiBot” Android banking Trojan that was active from 2016 to 2017.
Most of the targeted banking apps are related to banks and financial institutions operating in Europe, Australia, the U.S., and Canada. In addition to financial apps, threat actors also targeted shopping, communication, and business apps related to German online car selling services, Polish online shopping sites, and email service providers.
How BlackRock Attacks
Once the malware installs on the device, it hides its icon from the app drawer and accesses the victim’s accessibility service privileges. The BlackRock then grants itself additional permissions to function without the victim’s knowledge. The malware receives commands from the C2 or C&C server and launches overlay attacks to steal login credentials.
BlackRock Features
The researchers stated that BlackRock poses a variety of features, allowing it to remain in stealth mode and steal personal information from the victim’s device. The Trojan can perform:
- Overlaying: Dynamic (Local injects obtained from C2)
- Keylogging
- SMS harvesting: SMS listing
- SMS harvesting: SMS forwarding
- Device info collection
- SMS: Sending
- Remote actions: Screen-locking
- Self-protection: Hiding the App icon
- Self-protection: Preventing removal
- Notifications collection
- Grant permissions
- AV detection
“BlackRock offers a quite common set of capabilities compared to average Android banking Trojans. It can perform the infamous overlay attacks, send, spam and steal SMS messages, lock the victim in the launcher activity (HOME screen of the device), steal and hide notifications, deflect usage of antivirus software on the device and act as a keylogger. Interestingly, the Xerxes Trojan itself offers more features, but it seems that actors have removed some of them in order to only keep those that they consider useful to steal personal information,” the researchers said.






















