
The FBI is warning users and organizations about the Mamba ransomware that is targeting various entities including local governments, legal agencies, transportation services, technology providers, industrial, commercial, manufacturing, and construction businesses. In a security advisory, the FBI stated the Mamba ransomware is abusing the DiskCryptor – an open-source tool to encrypt files, drives, and operating system. Also referred to as HDDCryptor, the Mamba ransomware is active for the past five years.
Ransomware operators globally succeeded in targeting popular organizations and forcing ransom payments. The Mamba ransomware, used in 4.8% of cyberattacks, was listed as one of the top ransomware variants in Q1 of 2020. The operators behind Mamba misused the company’s content before encrypting the data and holding it hostage, threatening to post it unless the target agrees to pay.
How Mamba Ransomware Works
- Mamba ransomware often abuses freeware or open-source software like DiskCryptor to restrict victim access.
- The ransomware encrypts the victim’s hard drives by a modified bootloader. It can encrypt resources in network shares like folders, files, drives, printers, and serial ports.
- Once encrypted, the system displays a ransom note including the actor’s email address, ransomware file name, the host system name, and a place to enter the decryption key.
- Victims are instructed to contact the actor’s email address to pay the ransom in exchange for the decryption key.
Mamba Ransom Note

Mamba’s Limitation
The FBI also revealed a weak spot in the Mamba ransomware encryption process that could help victim organizations recover their corporate data without paying any ransom.
As stated earlier, Mamba ransomware relies on DiskCryptor to encrypt victim systems which require the system to restart and add necessary drivers within two minutes. While the encryption key and the shutdown time variable are stored in DiskCryptor’s configuration in a plaintext file myConf.txt, a second restart happens after the encryption process two hours later. The FBI claims that this two-hour time gap is a chance for the victims to decrypt their locked files by paying the ransom.
“If any of the DiskCryptor files are detected, attempts should be made to determine if the myConf.txt is still accessible. If so, then the password can be recovered without paying the ransom. This opportunity is limited to the point in which the system reboots for the second time,” the FBI said.
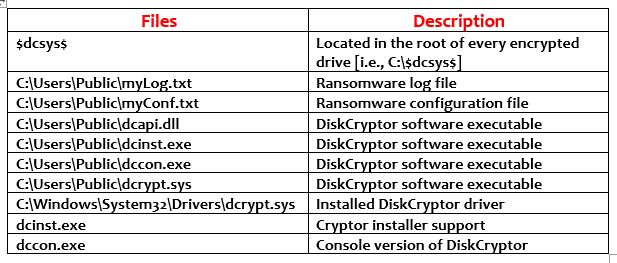
Mamba’s Key Artifacts
Mitigation Measures
The FBI also recommended certain security measures to prevent ransomware attacks. These include:
- Regularly back up data, air gap, and password-protect backup copies offline. Ensure copies of critical data are not accessible for modification or deletion from the system where the data resides.
- Implement network segmentation. Require administrator credentials to install the software.
- If DiskCryptor is not used by the organization, add the key artifact files used by DiskCryptor to the organization’s execution blacklist. Any attempts to install or run this encryption program and its associated files should be prevented.
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, secure location (i.e., hard drive, storage device, the cloud).
- Install updates/patch operating systems, software, and firmware as soon as they are released.
- Focus on awareness and training. Provide users with training on information security principles and techniques as well as overall emerging cybersecurity risks and vulnerabilities (i.e., ransomware and phishing scams).
FBI on Paying Ransom
FBI stated that it is against ransom payments, as it encourages threat actors to continue their ransomware attacks by targeting other companies. The agency urged users and organizations to report ransomware incidents to the FBI’s Internet Crime Complaint Center (IC3) at https://ic3.gov.
“The FBI does not encourage paying ransoms. Payment does not guarantee files will be recovered. It may also embolden adversaries to target additional organizations, encourage other criminal actors to engage in the distribution of ransomware, and/or fund illicit activities. However, the FBI understands that when victims are faced with an inability to function, all options are evaluated to protect shareholders, employees, and customers,” the FBI said.
Related Stories:






















