
The world today is increasingly digital. And with rapid digital transformation and technology adoption, hackers are misusing the situation with more targeted attacks. A report from cyberthreat intelligence provider Check Point Research stated that threat actors exploited Google Cloud to host malicious payloads and launch phishing attacks.
By Pooja Tikekar, Feature Writer at CISO MAG
The Google Cloud Phishing Journey
- A PDF was uploaded to Google Drive.
- The PDF was disguised to resemble a Microsoft SharePoint notice, which contained a link to an MS Access Document.
- Once clicked, it redirected the user to a phishing page, which was hosted on googleapis.com/asharepoint-unwearied-439052791/index.html.
- The user was then prompted with a popup to login with their Microsoft Office 365 credentials or organizational e-mail ID and password.
- Once the login credentials were entered, the user was led to a real PDF report published by renowned global consulting firm. The final PDF left little or no suspicion in the mind of the user because he was tricked into viewing useful information.
Security professionals find it difficult to identify or detect such phishing campaigns as they are hosted on public cloud services.
During all these stages, the user never gets suspicious since the phishing page is hosted on Google Cloud Storage. However, viewing the phishing page’s source code has revealed that most of the resources are loaded from a website that belongs to the attackers, prvtsmtp[.]com:, the report stated.
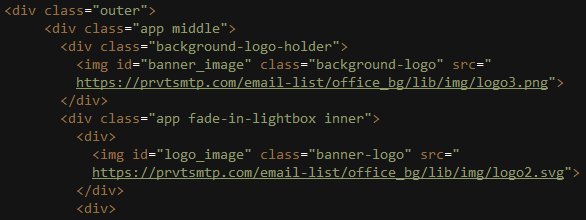
Investigating prvtsmtp[.]com showed that it resolved to a Ukrainian IP address (31.28.168[.]4). Many other domains related to this phishing attack resolved to the same IP address, or to different ones on the same netblock, the report added.
Google has a zero-day tolerance policy; hence it suspended the phishing URL and all the URLs associated with it. In the past, the hackers used Dropbox and Microsoft Azure to host phishing pages.
Precautionary Measures
To stay protected against phishing attacks, Check Point suggested the following practical precautions:
- Beware of lookalike domains and double-check spelling errors in emails and websites.
- Be cautious with files received via email from unknown senders, especially if they prompt for a certain action you would not usually do.
- Do not click on promotional links or emails. Order goods from authentic sources.
- Beware of “special” offers. “An exclusive cure for coronavirus for $150” is usually not a reliable or trustworthy purchase opportunity.
- Do not reuse passwords between different applications and accounts.
About the Author
Pooja Tikekar is a Feature Writer, and part of the editorial team at CISO MAG. She writes news and feature stories on cybersecurity trends.























