
A hack-for-hire campaign has targeted thousands of users and hundreds of organizations across six continents over the past several years, according to a report from Citizen Lab, a laboratory-based at the Munk School of Global Affairs and Public Policy of the University of Toronto.
Dubbed as “Dark Basin,” Citizen Lab linked the hacker group to an Indian technology firm BellTroX InfoTech Services and related entities. It is found that the group spied on American nonprofits, senior politicians, government prosecutors, CEOs, journalists, and human rights defenders.
Based on its investigation that started in 2017, Citizen Lab discovered around 28,000 shortened URLs containing e-mail addresses of targets. Dark Basin was Initially suspected as a state-sponsored campaign but was later identified as a hack-for-hire operation. The group is likely behind the commercial espionage on high-profile public events, criminal cases, financial transactions, news stories, advocacy groups, hedge funds, and multiple industries.
“Over the course of our multi-year investigation, we found that Dark Basin likely conducted commercial espionage on behalf of their clients against opponents involved in high profile public events, criminal cases, financial transactions, news stories, and advocacy,” Citizen Lab said.
Links to Indian Firm
Citizen Lab stressed this cyber-espionage is the work of BellTroX InfoTech Services. Surprisingly, the BellTrox’s director, Sumit Gupta (also known as Sumit Vishnoi), was indicted in 2015 by the U.S. authorities for participating in a similar hack-for-hire scheme, including crimes related to a conspiracy to access the e-mail accounts, Skype accounts, and computers of clients.
“To our knowledge, Gupta was never arrested in relation to the indictment. An aggregator of Indian corporate registration data lists Sumit Gupta as the director of BellTroX, and online postings by a ‘Sumit Vishnoi’ contain references to BellTroX,” Citizen Lab said.
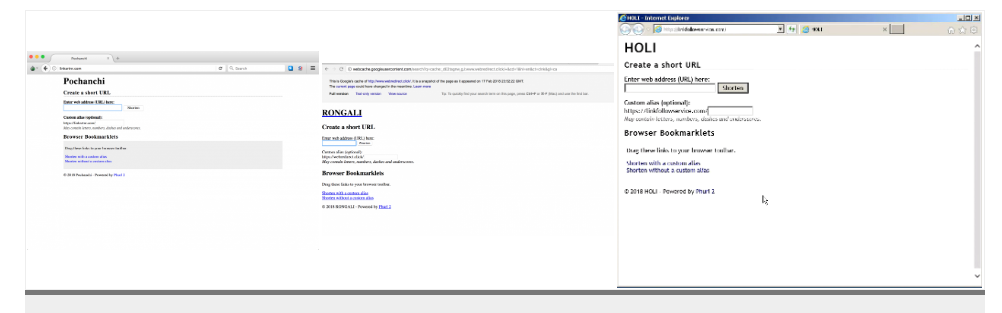
Citizen Lab attributed Dark Basin operations to India as hundreds of phishing emails related to them show timestamps consistent with working hours in India’s time zone (UTC+5:30), and the same timestamps were observed in phishing kit source code that was left open online by the group. Several URL shortening services had names associated with Indian words like Holi, Rongali, and Pochanchi.
Targeting American Organizations
Dark Basin hacking group targeted American advocacy organizations working on domestic and global issues, including the climate advocacy organizations and net neutrality campaigners. “Dark Basin has a remarkable portfolio of targets, from senior government officials and candidates in multiple countries, to financial services firms such as hedge funds and banks, to pharmaceutical companies,” Citizen Lab added.
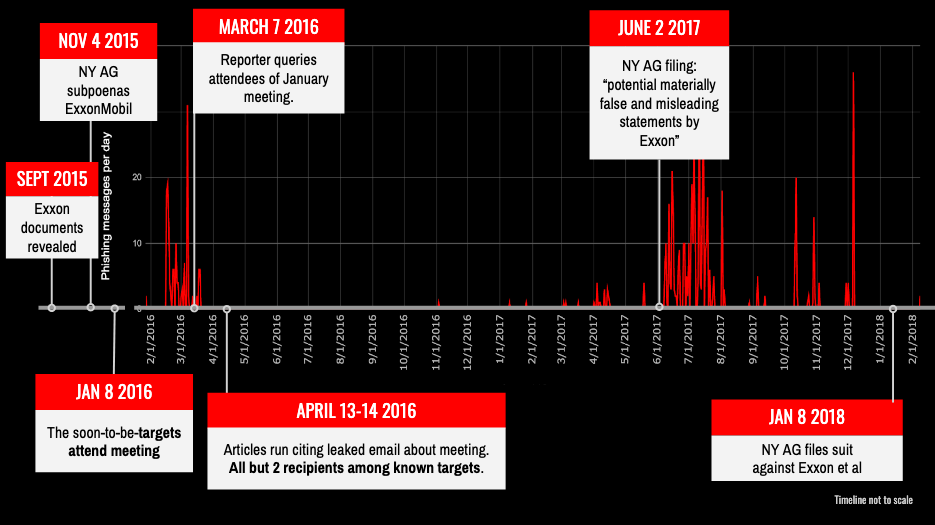
Security pros at CitizenLab discovered a cluster of targeted individuals and organizations that were engaged in environmental issues in the U.S. In 2017, Citizen Lab contacted these organizations, which are linked to the #ExxonKnew campaign, to determine the nature and scope of the attacks.
In 2016, the campaigners of #ExxonKnew were invited to a private meeting via a secret email, which was later leaked to two newspapers. According to Citizen Lab, two recipients of the leaked email were identified as the targets of Dark Basin group. The targeting spiked in February and March 2016, and then in June and July 2017.
Some other targeted organizations include Rockefeller Family Fund, Climate Investigations Center, Greenpeace, Center for International Environmental Law, Oil Change International, Public Citizen, Conservation Law Foundation, and Union of Concerned Scientists.
“We were able to identify several BellTroX employees whose activities overlapped with Dark Basin because they used personal documents, including a CV, as bait content when testing their URL shorteners. They also made social media posts describing and taking credit for attack techniques containing screenshots of links to Dark Basin infrastructure. BellTroX and its employees appear to use euphemisms for promoting their services online, including ethical hacking and certified ethical hacker,” Citizen Lab said.
Citizen Lab notified hundreds of targeted individuals and organizations and provided with assistance in tracking and identifying the hacking campaign. It also shared its investigation findings with the U.S. Department of Justice (DOJ).






















