
In a new kind of insider threat campaign, cybersecurity researchers found a Nigerian cybercriminal group enticing unwitting employees by offering them a share of their presumed ransom if they deploy Black Kingdom ransomware, also known as DemonWare or DEMON, on corporate network systems. The ransomware operators reportedly offered one million or 40% of the $2.5 million ransom as bribe to employees if they deployed the ransomware physically or remotely.
Abnormal Security claimed that it blocked multiple emails sent to its employees, requesting them to be a part of the ransomware campaign. “We identified and blocked several emails sent to Abnormal Security customers soliciting them to become accomplices in an insider threat scheme. The goal was for them to infect the companies’ networks with ransomware. These emails allege to come from someone with ties to the DemonWare ransomware group,” Abnormal Security spokesperson said.
Active since 2019, Black Kingdom ransomware was used by threat actors to exploit Microsoft Exchange vulnerability CVE-2021-27065.
How Black Kingdom Ransomware Spreads?
The Black Kingdom operators provided two options to interested employees for further communication: Outlook email or Telegram. The attackers delivered the ransomware via email attachments or using direct network access. Abnormal Security set up a fictitious persona to contact the ransomware operators.
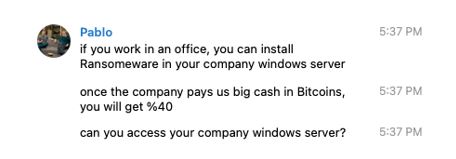
“As the conversation continued, it became clear that the actor was quite flexible in the amount of money he was willing to accept for the ransom. While the initial email insinuated the ransom would be $2.5 million, the actor quickly lowered expectations by indicating he hoped he could charge our fake company just $250,000. After our persona mentioned the company we worked for had annual revenue of $50 million, the actor pivoted and lowered the number even further to $120,000.
“The tactic used by this actor, however, allowed us to understand it better. Since the actor invited a target to get in touch with him, we did just that. We constructed a fictitious persona and reached out to the actor on Telegram to see if we could get a response. It didn’t take long for a response to come back, and the resulting conversation gave us an incredible inside look at the mindset of this threat actor,” Abnormal Security added.






















