Organizations can boost their overall cybersecurity posture by regularly updating their network systems and patch vulnerabilities. Understanding how attackers leverage malicious techniques and the security gaps to exploit flaws and bugs will help businesses develop better defensive measures to thwart evolving threats. Several international cybersecurity agencies stated that threat actors are targeting publicly known or existing flaws to break into organizations’ network systems.
Recently, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Australian Cyber Security Centre (ACSC), the U.K. National Cyber Security Centre (NCSC), and the FBI published a joint cybersecurity advisory listing the top exploited security flaws in 2020 and 2021. The advisory provides technical details of over 30 vulnerabilities that are constantly exploited by cybercriminals.
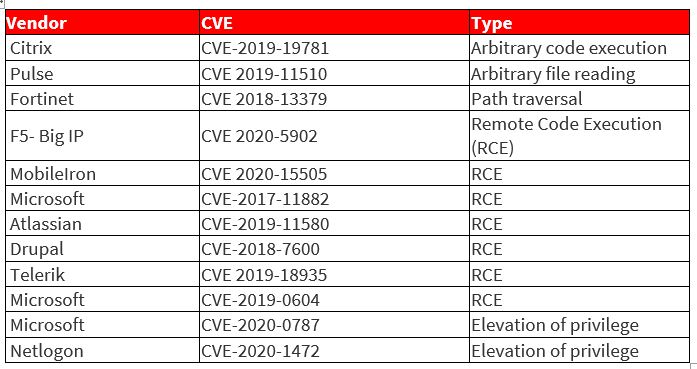
Top Routinely Exploited Vulnerabilities in 2020:
Top Routinely Exploited Vulnerabilities in 2021:
The advisory stated that threat actors mostly targeted security flaws in perimeter-type devices in 2021. These include:
CVE-2021-26855
CVE-2021-26857
CVE-2021-26858
CVE-2021-27065
CVE-2021-22893
CVE-2021-22894
CVE-2021-22899
CVE-2021-22900
CVE-2021-27101
CVE-2021-27102
CVE-2021-27103
CVE-2021-27104
CVE-2021-21985
CVE-2018-13379
CVE-2020-12812
CVE-2019-5591
Inconsistent Patch Management
The federal agencies stated that most of the vulnerabilities stemmed due to the distributed work environment amid the COVID-19 pandemic. The increased use of remote working tools like virtual private networks (VPNs) and cloud computing environments become an additional burden to security admins, making it difficult to keep pace with the regular patch management procedures.
Mitigate Risk
The best way to mitigate the vulnerabilities is to update the systems with the latest software versions whenever they are available. In case the patch is unavailable, apply temporary fixes provided by the vendor to mitigate the risks. Addressing the critical vulnerabilities on priority will help to defend against potential cyber intrusions.
“Cyber actors continue to exploit publicly known—and often dated—software vulnerabilities against broad target sets, including public and private sector organizations worldwide. However, entities worldwide can mitigate the vulnerabilities listed in this report by applying the available patches to their systems and implementing a centralized patch management system,” the advisory stated.