Over the last two decades, the role of a CISO has gained significant importance for businesses. The life of a CISO can vary quite a bit based on the organization’s size and business complexities. Even though CISOs work for different domains calling for different job responses, they do, however, face similar challenges and often make similar quick decisions to help secure their businesses. In this digitized world, information is a business enabler and a source of sustained competitive advantage. Securing this information is naturally becoming vital for survival. For this reason, an organization’s information security strategy must align with its strategic goals. This, along with many other responsibilities, lies on the shoulders of the CISO. And, although it is the dream of many security professionals in the industry to become a CISO, only a few make it to the top due to the sheer magnitude of the challenge. Nevertheless, here is what a day in the life of a modern CISO typically looks like for all those aspiring to join this elite circle.
By Ramiro Rodrigues, Cyber & Digital Security Associate Director – Latin America, Accenture
Who is a Chief Information Security Officer?
A Chief Information Security Officer (CISO) is the highest-ranking in the company’s information security organization. One of the primary objectives of a CISO is to build a security posture that is compliant with legal, regulatory, and contractual obligations of information security. CISOs are also capable of protecting the organization from emerging external and internal threats.
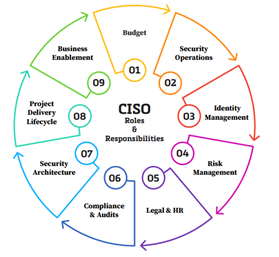
A CISO achieves this objective through various organization-level controls and disciplines.
- Establish a Security Strategy
- Risk Assessment
- Security Governance
- Vulnerability Management
- Verifications (Audits, Penetration tests, red team exercises)
- Program Management
- Leadership
- People Management
CISOs have a team of people who help them in achieving the objectives. A CISO always operates within the risk appetite of the organization. While the responsibilities are strategic, there are some basic disciplines that CISOs are usually concerned with.
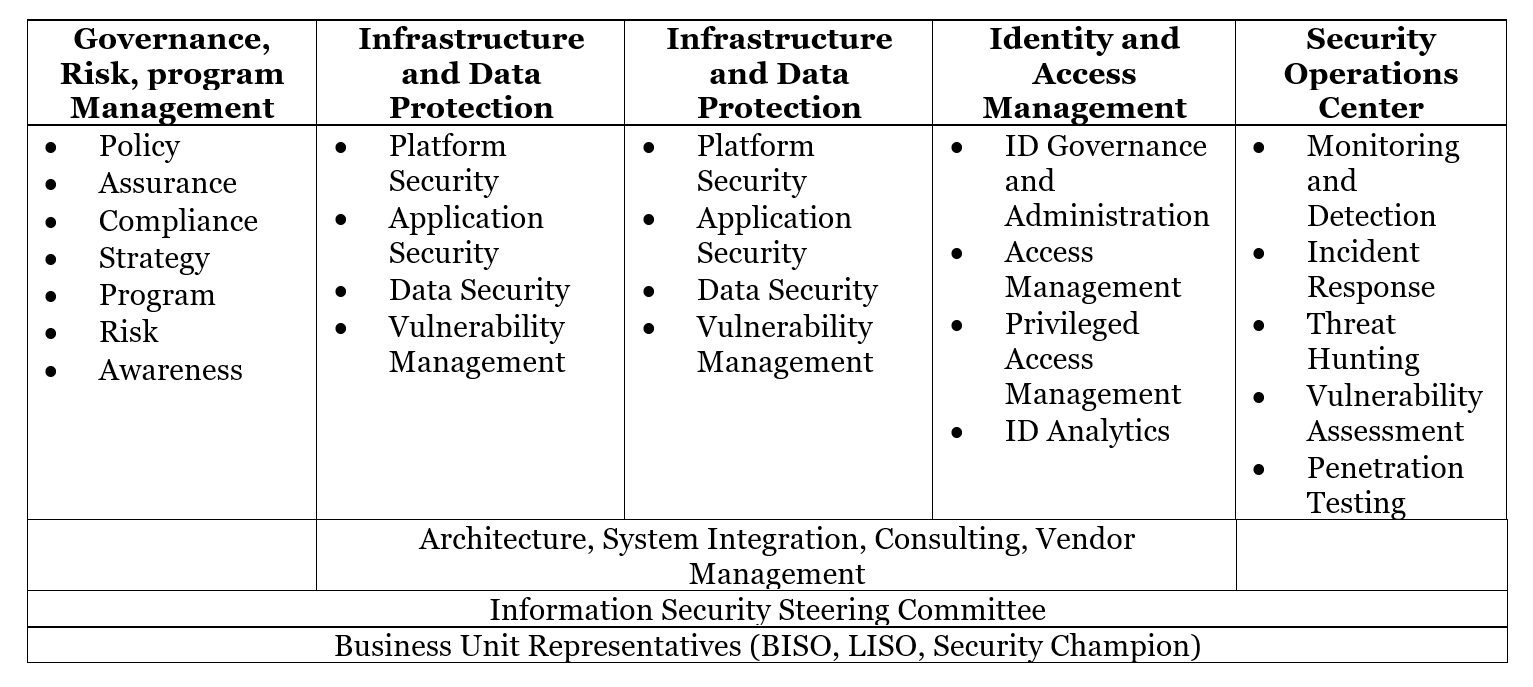

A Day in the life of a CISO
Each day in the life of a CISO is different; it comes with new challenges, emergency meetings, cyberthreats, and security issues, to name a few. Predicting the coming day is next to impossible for them, although they can anticipate threats and vulnerabilities.
Here’s how a typical day in the life of a CISO looks like:
05:15 AM | Before leaving for office
The first thing a CISO does as soon they wake up in the morning is checking their inbox, text messages, WhatsApp, LinkedIn, Instagram, and Twitter to ensure that nothing urgent has cropped up through the night. The morning starts with the hope that everything related to security is going to be well and that the company’s critical processes are operating as expected.
Like everyone, they also spend some time for physical exercise, to maintain fitness and overall health, following a healthy breakfast as per the weekly diet plan. In between, they find some time to scroll through cyber communities for news/updates, reading the news, and responding to messages.
Maintaining a balance between personal and professional life is a bit tricky, but they are right on this front. Chat with family members, listening to their kids talking about their activities and learning at school is a part of their routine.
08:00 AM | Driving to the office
While driving to the office they think about the day ahead, meetings, key things to do and fix, recollecting anything missing on the calendar, and spend the remaining time listening to cybersecurity podcasts. In the back of their mind, they are also making a note of the number of email notifications.
Morning (barring a late-night attack): As they start their day, the first thing on their mind is how safe their organization is and what new attacks the hackers will come up with today. They need to keep up with the latest threat reports and attacks by reviewing a summary from their research team or by performing personal research through email, security sites, and other news sites and feeds.
08:30 AM | Reached Office
Security Dashboard
As soon as a CISO reaches the office, they will look into the security and digital dashboard.
The security dashboard lets you view your organization’s internal and external security posture and enables the CISO to review the Threat Protection status and act on security alerts.
The objective of a Security Dashboard
- Threat Management Summary
- Threat Protection Status
- Threat Detections
- Information on Attack – How and When?
- Information on Intruders – Why, How, and When?
- IP Address being attacked – When?
- IPS Events & Logs
- Attacks Blocked
- Packets Blocked
- System, firewall, and security alert log files
- Show Impact & Improvements
- Show trending information within the security
- Communicate both security and organizational objectives
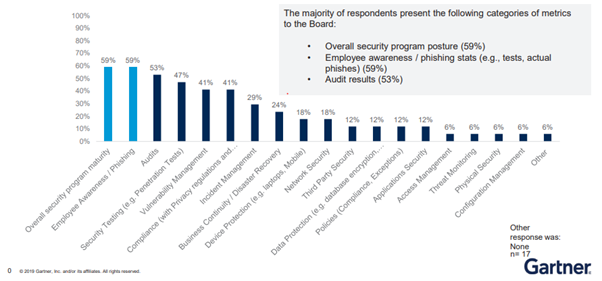
Please check the categories of security metrics that are presented to the Board.
After the security dashboard, a CISO spends some time checking and responding to emails, a glance at the calendar, and the to-do list.
Next is a quick 15-minute huddle with SPOCs from Information Privacy, Compliance, and Governance Team to ensure that they are updated with the prevailing laws and regulations in the country.
01:00 PM | Lunch Time
After all these meetings, the CISO has to find some time for the product business unit representative as the calendar is full, and discussion is also essential. Thus, making lunchtime more fruitful by discussing with him how agile security practices create value for products.
CISOs seek to provide greater value to the business and demonstrate tangible benefits of security to the broader organization. Product security could serve as an opportunity for CISOs to create new value.
By meeting with BU product owners, it is the opportunity for CISOs to add greater value to their organization, contribute to the overall customer experience, and elevate their profile/visibility by involving themselves in customer-facing product security efforts.
Business leaders, while familiar with non-security aspects of the company-consumer relationship, lack the in-depth security knowledge of career security professionals. They understand customers want a secure experience but are not fully qualified to publicly “sell” a secure customer experience. CISOs, on the other hand, routinely secure business-to-consumer products, but rarely deal directly with customers. As a result, many CISOs focus on securing business operations and products before they are delivered to the customer, but do not view customer-facing product security as a major potential value-add the CISO can bring to the business.
01:45 PM | Post Lunch
Cybersecurity Campaign
A CISO, along with 2-3 members of the team, plans a cybersecurity campaign, a real-time phishing attack, to understand the employees’ level of awareness on the phishing attacks. Post that they create a report on many employees who:
- Opened the email
- Deleted the email
- Clicked the malicious link in the email
- Reported the email to the security team
Based on the above report, they’ll know of their employees’ security awareness/alertness and decide on suitable training for them.
This is followed by a quick 30-minute meeting with a Security Architecture leader, along with the Learning and Development team about the security concerns for home-based working employees.
The primary security concerns for work from home employees are:
- Devices not secured
- Data security
- Insecure VPN
- Third-party applications
- Shadow IT
- Awareness training on phishing and malicious attacks
Possible Security Precautions
- Set-up strong defense
- Security software to monitor and identify for unusual activity
- Patch the holes in their network security
- Configure security tools
- Integrated cybersecurity architecture
Call from Developer Security
Before stepping into another task, the CISO gets a developer security team call, announcing the successful end of the sprint using the security toolchain. Then spends some time looking at the security checklist and their integration at multiple points.
Unexpected Risk Forum Meeting
Now, the risk forum meeting is 5 minutes overdue, and a CISO has to run to the meeting room. So, this meeting was not on the calendar and came up suddenly as the security team found an employee not following the Secure Computer User policy. The CISO wants to address this issue by meeting the culprit and the line manager and re-educating them about the security concerns.
Meeting with CIO
It’s time for a meeting with the CIO. At larger companies, CISOs usually report to the CIO, with a dotted line to the CEO and Board. The discussion with CIO is about information security risk management while supporting the business objectives, and vendor risk management for a new third-party vendor. They also discuss some points for the upcoming Board meeting.
Stakeholder Meeting
A one-hour meeting with critical stakeholders – COO, CFO, CRO, HR, BU GM, or CAE – to monitor their security levels and check how they effectively support or derail your program.
CISOs are tired of too many meetings and would like to spend some time having coffee with CFO to discuss the security aspects of the company’s acquisition. After a refreshment break, they go to the cabin, look at the next day’s calendar plan and schedule it accordingly.
06:00 PM | Driving Back to Home
While driving, they would love to listen to news about the market and the business of the company.
Once they reach home and relax for some time, they spend some time in virtual meetings with industry peers to discuss, share, and collaborate on a topic of common interest.
07:00 PM | Family Time
Spend some time with spouses and kids – chat about their daily activities, studies, sports, latest movies, and upcoming family trips, promising time for football practice with kids for their school sports competition, and sharing useful tips on how they used to play football during their college days. This is the only time when they are trying not to think about the work too much. Then it is time for dinner.
After dinner, a CISO spends some time reading cybersecurity magazines, writing articles, and a few minutes on cybersecurity communities for news and updates.
09:00 PM | Going to Bed
Before going to bed, a CISO final checks that all is well and once again checks the news feed, e-mails, LinkedIn, Instagram, and Twitter.
How to become a Chief Information Security Officer (CISO)
Business, technology, and security, each talks their own language. A CISO needs to be multilingual, or will need someone to help bridge that gap if they can’t.
– Mike Gentle, Editor, The CISO Handbook
CISO careers begin with undergraduate degrees. Learners can earn associate degrees in CS&IT, but CISOs usually earn graduation in IT or a related discipline.
| With an undergraduate education | With an undergraduate education in the IT field, aspiring CISOs become entry-level network and system analysts. |
As a system analyst, individuals detect, protect, investigate cyberthreats. And then, by gaining valuable experience in the field, individuals can advance to the Managerial level.
| Mid-level Infosec professionals | Mid-level Infosec professionals, such as security engineers, security auditors, security consultants, and so on. |
CISOs may work as mid-level infosec professionals to develop their skills and knowledge in the technical field and improve their leadership aspects to the position.
| Senior-level professionals | Senior-level professionals such as security architects, IT managers, might represent the next steps for future CISOs. |
CISOs may work as senior-level professionals to build their leadership skills, managerial skills, and technical knowledge. To advance their skills, many CISOs earn graduate as well as a postgraduate degree in IT; Business administration may also boost their career goals and earning potential.
Career Paths for CISO
Here are five career and education phases toward becoming a CISO:
- Step – 1: Get the IT education to become a Security Analyst
- Step – 2: Get Additional Cybersecurity Certifications & Trainings
- Step – 3: Manage a Security Team
- Step – 4: Attain a Business Administration degree aligned with IT Security/Information Systems
- Step – 5: Promotion to Chief Information Security Officer
| Cybersecurity Certifications | The students or professionals to become specialized in any cybersecurity subfields, supporting their pursuit of the positions. |
Cybersecurity certifications in network defense, ethical hacking, security analyst, security incident management, and C|CISO further enhance an individual’s abilities to thrive as CISOs.
About the Author
 With more than 22 years of experience in information security and IT risk management, Ramiro Rodrigues is currently the Cyber & Digital Security Associate Director – Latin America, Accenture. He also served as the CISO and Director of Security and Risk Management at Gartner. His specializations include cybersecurity architecture and strategy planning, information security organization and talent management, privacy, and data protection officer (LGPD/GDPR), application and products security in Agile (DevOps and DevSecOps), cloud security strategy for platforms (IaaS, SaaS, PaaS), third-party risk management, threat and vulnerabilities management, incident response and cyber investigations, consumer identity and access management, and culture hacking mindset.
With more than 22 years of experience in information security and IT risk management, Ramiro Rodrigues is currently the Cyber & Digital Security Associate Director – Latin America, Accenture. He also served as the CISO and Director of Security and Risk Management at Gartner. His specializations include cybersecurity architecture and strategy planning, information security organization and talent management, privacy, and data protection officer (LGPD/GDPR), application and products security in Agile (DevOps and DevSecOps), cloud security strategy for platforms (IaaS, SaaS, PaaS), third-party risk management, threat and vulnerabilities management, incident response and cyber investigations, consumer identity and access management, and culture hacking mindset.
Disclaimer
Views expressed in this are personal.
References
- https://medium.com/@remeshr/how-to-become-a-chief-information-security-officerciso-f6a4eeb718ff
- https://www.businessnewsdaily.com/10814-become-a-chief-information-securityofficer.html
- https://www.cyberdegrees.org/jobs/chief-information-security-officer-ciso/
- https://infosecaddicts.com/career-path/why-and-how-to-become-a-ciso/
- https://www.cybersecurityeducation.org/careers/chief-information-security-officer/
- https://www.gartner.com/document/3823187?ref=solrAll&refval=256128995















