
Cybersecurity researchers have observed a recent trend of Ursnif malware spam specifically targeting German nationals using a spam email message written in German language. Once the target system is compromised, Ursnif steals system information and attempts to steal banking and online account credentials through various mediums including web browsers.
What is Ursnif?
Ursnif malware spam is popular in the Windows banking Trojan family. Its source code has been active in some form or another since 2007 when it first appeared in the Gozi banking Trojan. Gozi’s source code was mistakenly leaked by its developers in 2010, which gave birth to its advanced version of malware, now known as Ursnif.
How Ursnif Works?
Although there are multiple variants of Ursnif, this version seen in Germany follows this workflow:
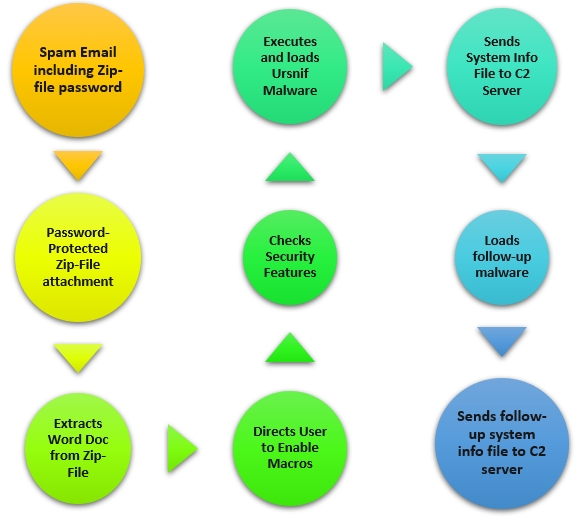
- The campaign begins with a spam email containing a password protected zip file being sent to the targeted victim. The email content contains the password to this zip file. In this campaign, researchers have found 3-digit passwords being used, such as 111, 333, 555 and 777.
- On entering the password given in the email text, a Microsoft Word document is extracted from the password-protected zip file. These Word documents are named doc. The Word document also contains a text message written in German. This message directs the user to enable macros in MS Word.
- Once the macros are enabled, other security features such as Protected Mode are checked by the malware dropper. On confirming a vulnerable Windows host, the dropper pushes the Ursnif malware into the system.
- Ursnif further loads (executes .exe) into the system and begins stealing multiple sets of information from the system and stores them in a file. It then connects to a malicious command and control (C&C or C2) server and transfers the info file into it.
- What differentiates the German version of Ursnif malware is this step. The loaded Ursnif malware is seen dropping a few other follow-up payloads that are variants of the original Ursnif source code.
Indicators of Compromise
Main Ursnif malware IoC details are as follows:
- 85.157[.]246 port 80 – emblareppy[.]com GET /gunshu/lewasy.php?l=ambobi9.cab
- port 80 – settings-win.data.microsoft[.]com – GET /images/[long string].avi
- 85.153[.]218 port 80 – pzhmnbarguerite4819[.]com – GET /images/[long string].avi
- 169.181[.]33 port 80 – n60peablo[.]com – GET /images/[long string].avi
- port 443 – settings-win.data.microsoft[.]com – HTTPS traffic
- 141.103[.]204 port 443 – nk47yicbnnsi[.]com – HTTPS traffic
Follow-up Ursnif malware variant IoC details are as follows:
- port 80 – google[.]com – GET /
- port 80 – www.google[.]com – GET /
- DNS queries for onionpie[.]at – no response from the server
- DNS queries for tahhir[.]at – no response from the server
- 249.145[.]116 port 80 – limpopo[.]at – GET /images/[long string]
- 175[.]7.8 port 80 – estate-advice[.]at – GET /images/[long string]
- 56.73[.]146 port 80 – sweetlights[.]at – GET /g32.bin
- 56.73[.]146 port 80 – sweetlights[.]at – GET /g64.bin
- 56.73[.]146 port 80 – estate-advice[.]at – POST /images/[long string]
- 95.185[.]58 port 80 – estate-advice[.]at – GET /images/[long string]
- 249.145[.]116 port 80 – limpopo[.]at – POST /images/[long string]
- 51.223.47[.]15 port 80 – estate-advice[.]at – POST /images/[long string]















