Tag: Compliance
“More States Move to Comprehensive State Laws Like the CCPA to...
As 2022 peeks from the corner, there is anticipation that the year will, maybe, witness better security management to address the continued sophistication of...
How to Ensure Data Management Excellence
In response to high-profile data breaches, staggering fines, and rapidly evolving privacy and data requirements, CIOs and CISOs are facing a critical mandate: to...
How is Automation Helping in Security?
If you are looking at automation in regard to PKI, there are four areas in security where automation can be applied: Efficiency, Security, Crypto-agility,...
Corporate Compliance Strategies to Protect Data
The pandemic has pushed the corporate workforce to remote locations, which has resulted in increased risk to corporate data. As corporations rise to the...
CISOs Must Declare an End to the War Between Security and...
The time has long passed for CISOs and other security leaders to shift their perception regarding cybersecurity compliance assessments. These assessments have traditionally been...
Emphasize the “Spirit” of Compliance Over Simply “Checking all the Boxes”
If you’re about to face a compliance audit, undergo an assessment, or produce an industry certification — and are doing so without much serious...
Compliance Standards and the Changing Nature of Data Privacy
As the world continues to embrace newer and better technologies like virtualization, SDN, or pure Cloud-based SaaS, coordinate values in all the 4V dimensions...
Episode #6: How Insurance Fraud is Evolving (and Anti-fraud Measures)
Insurance Fraud continues to evolve as it has done for centuries. Fraudsters, too, have evolved their techniques and upped their game. Dennis Toomey, Global...
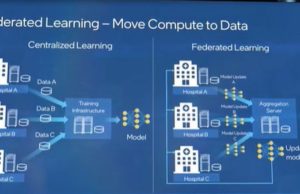
Federated Learning Can Solve Security and Data Privacy Challenges: Intel Labs
In many fields like medicine and financial services, the owners of data are bound by regulatory restrictions around data privacy. That can be a...
Streamline Your Compliance Needs with ByteChek
Cybersecurity assessment is the need of the hour for all organizations as security breaches become daily news for organizations around the globe. But these...