
When it comes to cybersecurity, no organization can be 100 percent safe. Even organizations that use advanced security technologies may face problems with such key elements as people, business processes, technologies, and associated intersection points.
There are many methods that help to evaluate the protection level: analysis of the security of systems and applications, penetration testing, assessment of personnel security awareness, etc. However, due to the constant change in the cyberthreat landscape, and the emergence of new hacking tools and criminal groups, new types of risks arise that are difficult to identify using traditional methods.
By David Balaban, Computer Security Researcher
One of the most advanced approaches to test the security level of any organization is Red Teaming — a continuous assessment of the security of information systems, as well as the preparedness of incident response specialists, and the infrastructure’s resistance to new types of attacks, including APT and targeted attacks.
By utilizing the Red Teaming approach and practicing the response to controlled attacks, the internal security teams can enhance their skills in identifying previously undetected threats and thus stop real intruders in the early stages of the attack preventing monetary and reputation damages to the business.
Red Teaming. What is it?
Red Teaming is a comprehensive and most realistic way to test an organization’s ability to resist complex cyberattacks using advanced methods and tools from the arsenal of hacker groups.
The main idea of this exercise is not only to identify potential weaknesses and vulnerabilities that were not detected using standard testing methods, but also to assess the organization’s ability to prevent, detect, and respond to cyberattacks.
Red Teaming helps an organization to understand:
- How security tools protect important assets.
- Whether the early warning and monitoring systems are configured correctly.
- What opportunities attackers must penetrate the internal infrastructure.
Security assessment and training should strive to be maximally realistic and close to real-life situations. The organization’s security team (Blue Team) should not be informed of the start of the project so that the Red Team can model the actions of real attackers based on specific threat analysis and try to breach the infrastructure.
“Cyber-drills” that use the Red Teaming format are most effective for companies with a mature level of information security. Such drills are not limited in time and are focused on achieving different goals, whether it is gaining access to network nodes or sensitive information by any available means. The actual scenarios of Red Teaming are unique for each organization and depend on the goals set.
Commonly used scenarios include:
- Active Directory forest take over.
- Getting access to top managers’ devices.
- Imitation of theft of sensitive customer data or intellectual property.
Read Teaming vs. Penetration Testing
Despite the fact that Red Teaming and Penetration Testing use similar cyberattack tools, the goals and results of both approaches are different.
Red Teaming
The Red Teaming process simulates real targeted attacks aimed at an entire organization. The essence of this approach is the continuous probing of information systems attack resistance. Continuous deep probes provide a comprehensive understanding of how secure the infrastructure is, whether employees are aware of new threats and whether the internal processes of the organization are effective when they are exposed to a real attack.
Penetration Testing
Penetration testing specialists attempt to exploit vulnerabilities and increase their privileges in the systems in order to assess the possible risk from these rogue activities. Pentests do not test readiness to identify and respond to information security incidents.
Below are some of the differences between Red Teaming and Penetration Testing:

Red Teaming and Penetration Testing complement each other. Each approach is important and useful for the organization in its own way, since in the course of such a combined test, it is possible to evaluate both the passive security of the systems and the active security of the company.
Red Teaming in Action
Red Teaming can be divided into several successive stages. To increase efficiency, and considering the limited time, some activities within the main stages, may begin earlier or be performed in parallel with others. Therefore, in practice, the Red Teaming process is not such a clear linear sequence of steps.
More information about each stage:
1. The preparatory stage. Duration: 4 to 6 weeks.
During this stage, the current needs of an organization get assessed, and the amount of work gets calculated. Also, at this stage, the key points for conducting Red Teaming are specified and the official launch of the project is announced:
- A working group is created consisting of representatives of the Customer and the Contractor.
- The scope of work is determined (duration, volume, prohibited actions, etc.)
- Interaction protocols get created.
- The Red Team is formed according to the needs of the current project.
2. Active Red Teaming stage. Duration: 12 weeks or more.
At this stage, the Red Team:
- Runs Threat Intelligence.
- Develops scenarios based on crucial system functions and threat models.
- Forms a plan and attempts to attack agreed targets (assets, systems, and services that contain one or more important business functions.)
This stage can be divided into two sub-stages: cyber intelligence and scenario development, as well as testing/attacking in the Red Teaming format.
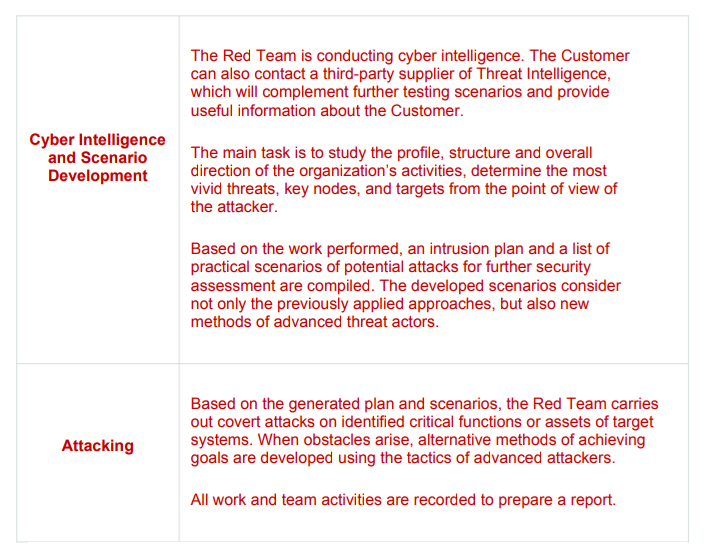
3. The final stage. Duration: 2 to 4 weeks.
All penetration activities get completed once all the planned steps have been successfully completed, or the time allotted for work has expired.
At this stage:
- The Red Team prepares a report describing its work, prepares conclusions and observations on the company’s ability to detect and respond to threats.
- The Blue Team prepares its own report describing the actions taken based on the chronology of the report of the Red Team.
- All participants exchange results, analyze them, and plan further steps to improve the organization’s cyber protection.
Parties involved in the Red Teaming process are:
- The White Team, which consists of a manager, representatives of the Customer’s business units, and the required number of security experts who will know about the project.
- The Blue Team – Customer’s security department responsible for the detection and response to information security incidents.
- The Red Team, which consists of a manager and several security experts simulating targeted attacks.
Methodology
To simulate attacks on a specific target, Red Teams should use proven methodologies that include best practices and adapt them to a specific Customer’s cyber landscape.
The life cycle of security assessment utilizing the Red Teaming format follows the model of The Cyber Kill Chain and has the following general steps: reconnaissance, weaponization, delivery, exploitation, installation, obtaining control, and performing actions in relation to the target.
The Real-life Red Teaming Case
Accessing Active Directory
The Customer was a group of companies operating in the heavy equipment production segment. The goal is to gain administrative access to the Active Directory domain controller at the company’s headquarters.
In the course of the project, it was found that the Customer uses multi-factor authentication (smart cards) for all types of access, including remote and external web services. The use of social engineering was prohibited.
The Red Team actions and results
Security experts conducted a thorough reconnaissance and determined that this organization acquired 12 companies and reorganized them into its subsidiaries right at the time of the Red Teaming operations.
The Red Team managed to get permission to conduct an attack on all the new companies in this group. One of the subsidiaries had very weak cyber-protections. Domain controllers – branchoffice1.domain.com were “hacked” and a VPN was discovered connecting the branch office local networks (Full-Mesh site-to-site VPN.)
The network connection was well protected but trust mechanisms between Active Directory forest domains did not work for controllers on the branchoffice1.domain.com so it was possible to spread the attack and breach the branchoffice2.domain.com, gaining administrator rights there.
Using the Kerberos “golden ticket” attack, the Red Team bypassed the smart cards protection at a “low level” due to the implementation features/failures of the Kerberos protocol. By exploiting the trust mechanism between Active Directory domains, the Red Team managed to obtain administrative rights at the head office. Thus, the domain controllers at headquarters were successfully hacked and experts achieved the goal of the Red Teaming project.
Conclusion
By conducting Red Teaming and practicing the response to controlled attacks, the internal security team can improve its skills in identifying previously undetected threats and stop real attackers in the early stages of the intrusion.
Security training that utilizes the Red Teaming approach gives the organization an idea of the strengths and weaknesses of its cybersecurity posture and allows to define an improvement plan for the continuity of business processes and the protection of valuable data.
By adding Red Teaming as part of its security strategy, a company can measure security improvements over time. Such measurable results can be used for the economic feasibility of additional information security projects and the introduction of new technical means of protection.
About the Author
 David Balaban is a computer security researcher with over 15 years of experience in malware analysis and antivirus software evaluation. David runs the Privacy-PC.com project which presents expert opinions on contemporary information security matters, including social engineering, penetration testing, threat intelligence, online privacy, and white hat hacking. As part of his work at Privacy-PC, Mr. Balaban has interviewed such security celebrities as Dave Kennedy, Jay Jacobs and Robert David Steele to get firsthand perspectives on hot InfoSec issues. David has a strong malware troubleshooting background, with the recent focus on ransomware countermeasures.
David Balaban is a computer security researcher with over 15 years of experience in malware analysis and antivirus software evaluation. David runs the Privacy-PC.com project which presents expert opinions on contemporary information security matters, including social engineering, penetration testing, threat intelligence, online privacy, and white hat hacking. As part of his work at Privacy-PC, Mr. Balaban has interviewed such security celebrities as Dave Kennedy, Jay Jacobs and Robert David Steele to get firsthand perspectives on hot InfoSec issues. David has a strong malware troubleshooting background, with the recent focus on ransomware countermeasures.
Disclaimer
Views expressed in this article are personal. The facts, opinions, and language in the article do not reflect the views of CISO MAG and CISO MAG does not assume any responsibility or liability for the same.















