
Threat intelligence team from GreatHorn uncovered a series of ongoing phishing campaigns targeting users of Microsoft’s Office 365 and Google’s Gmail. The attackers are using imposter open redirector domains and subsidiary domains of various popular brands and sending tens of thousands of emails to corporate account users globally.
The comprehensive and multi-pronged attack campaign has multiple hosting services and web servers that are used to host fraudulent Office 365 login pages. It is also found that malicious links and fraudulent emails/attachments are bypassing users’ security controls and email security platforms.
 Complete the Endpoint Security Survey and win lots of amazing prizes.
Complete the Endpoint Security Survey and win lots of amazing prizes.
Spoofing the Popular
GreatHorn researchers stated that phishing actors attempt to steal corporate email credentials, along with malicious JavaScript that deploys various Trojans and malware on any user who visits these fraudulent links/web pages, even if they do not submit their credentials. The attackers are spoofing well-known applications like Microsoft Office, Zoom, and Microsoft Teams to evade detection.
“The phishing webpages impersonate a Microsoft Office 365 login, use the Microsoft logo and request that users enter their password, verify their account, or sign-in. Given this campaign’s breadth and highly targeted nature, the sophistication and complexity suggest that the attackers’ significant coordinated effort is underway,” the researchers said.
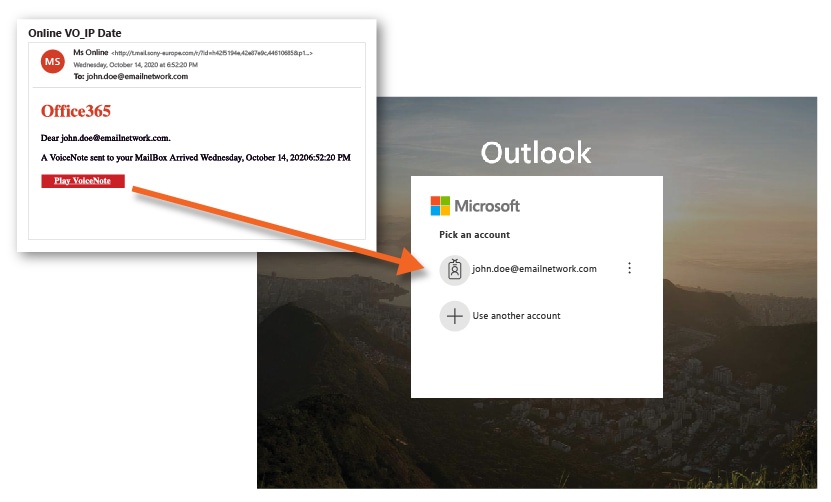
The researchers also identified hackers’ attempts to deploy the Cryxos Trojan on multiple browsers, including Chrome and Safari. The domains redirecting the users to the phishing kit and fraudulent login pages include:
- sony-europe.com (Sony)
- com (TripAdvisor)
- co.uk (RAC)
Webpage services hosting the phishing kit include digitaloceanspaces.com (DigitalOcean) and firebasestorage.googleapis.com (Google).
GreatHorn recommended organizations to search their email networks for messages containing URLs that match the threat pattern (http://t.****/r/) and remove if found any. “The GreatHorn Threat Intelligence Team has identified senior executives and finance personnel being targeted within the phishing campaigns. For organizations who are using role-based email security, users within these roles can be placed on more restrictive policies to minimize the risk associated with these attacks,” GreatHorn researchers added.















