
A cybercriminal gang, named as “FIN7 APT” has been found launching a social engineering attack. According to the security firm Trustwave Spider Lab, unknown attackers posed as Best Buy officials mailed letters via postal service to the targeted victims, which contained a gift card and USB drive. The matter in the letter contained a socially engineered message intended to lure the recipients to place the USB drive on their computer. It says the gift card is a thank you gesture for being a great Best Buy customer and the USB drive contains a list of products that can be purchased using the gift card.
According to the FBI, the FIN7 group mailed these letters to several businesses, via the U.S. Postal Service, targeting employees in human resources, IT, or executive management departments. In addition to the gift cards and USB, the attackers also sent teddy bears for some employees. There is nothing on the gift cards, however the USB contains malware.
The researchers at Trustwave found the USB drive was programmed to emulate a USB keyboard, as most PCs and software by default allows a USB keyboard to connect.
The Attack Process
Once the drive is inserted, a payload is injected, and a malware payload is downloaded. After that, a fake message pops up on the screen that says, “the USB device is not recognized”, which is to confuse the victim. During this time, an additional JavaScript is downloaded to register the infected device with the command-and-control (C2) server, which later sends encoded data containing the info-stealing software.
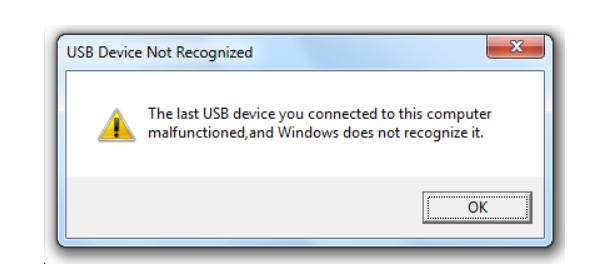
Massive Data Theft
Once the malware is downloaded successfully, it collects a huge amount of information from the infected device, which includes:
- Username
- Hostname
- User’s System Privilege
- Uses WMI query to get the:
- Process owner
- Domain name
- Computer model
- Operating system information
- Office and Adobe acrobat installation
- List of running Processes (including PID)
- Whether the infected host is running in a virtualized environment
The Bad USB Drive
Trustwave stated “One of our digital forensics and incident response retainer clients brought this device to our attention. One of their business associates received this suspicious letter. Fortunately, our client and their associate did not plug the drive into any computer.”
The researchers found some inscriptions on the head of the drive on the printed circuit which says, “HW-374”, and quick search of this serial number led to a product described as “BadUSB Leonardo USB ATMEGA32U4” for sale on shopee.tw.
If the users are not vigilant, attackers use these kinds of USB controller chips, programmed for malicious use, to launch an attack and infect users’ computers without knowing them.















