
The U.S. National Security Agency (NSA). and the Australian Signals Directorate (ASD) recently issued a joint security advisory “Cybersecurity Information Sheet” (CSI), which details threat actor activities. The security agencies stated that hackers are exploiting web application vulnerabilities to deploy the malicious web shell. The advisory contains a wide range of information for security teams who want to detect hidden web shells and to block malicious actors from deploying such tools on unpatched servers.
“Malicious cyber actors have increasingly leveraged web shells to gain or maintain access on victim networks. This guidance will be useful for any network defenders responsible for maintaining web servers,” the advisory stated.
What Is Web Shell Malware?
Web shell malware is a software deployed by a hacker on a compromised internal or internet-exposed server to gain access by executing arbitrary code remotely and delivering the malicious payloads. These web shells provide hackers with a visual interface that allows them to communicate with a hacked server and its file system. The web shells enable hackers to rename, copy, delete, edit, and upload files to the server.
“Web shell malware has been a threat for years and continues to evade detection from most security tools. Malicious cyber actors are increasingly leveraging this type of malware to get consistent access to compromised networks while using communications that blend in well with legitimate traffic. This means attackers might send system commands over HTTPS or route commands to other systems, including to your internal networks, which may appear as normal network traffic,” the NSA said.
Attackers install malicious web shells on the internet-connected servers or in web applications like CMS, CMS plug-ins, CRM-systems, and corporate applications to exploit the vulnerabilities in them.
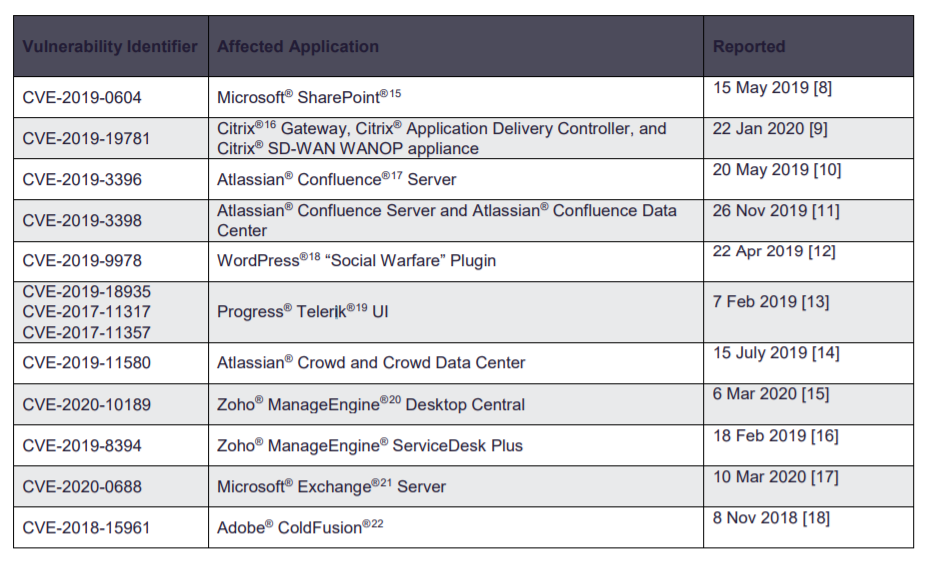
Web Application Vulnerabilities Used to Install Web Shells
The NSA and ASD provided a list of commonly exploited web application vulnerabilities in web applications. These include:
The advisory listed instructions on web shell detection, prevention, and mitigation strategies. “Web shells can play the role of tenacious backdoors or relay links to route malicious programs or scripts to other systems. Usually, hackers connect web shells on several compromised systems simply to route traffic over networks, from the internet-connected systems to internal networks,” the advisory added.















