
Every minute is an opportunity for threat actors when they found a server left online unsecured. A latest security experiment by Comparitech led by cybersecurity researcher Bob Diachenko discovered that cybercriminals attacked a model of an unsecured database 18 times in a single day.
In a security alert, Comparitech explained how unauthorized third parties find, gain access, and alter exposed data without any authentication process, leaving users’ privacy at risk.
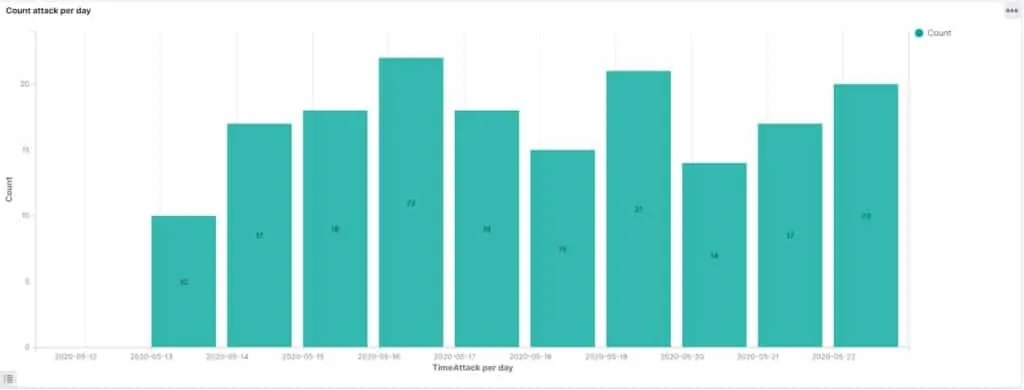
The company set up a honeypot to know how quickly the hackers would attack an Elasticsearch server with a dummy database and fake data in it. Comparitech left the exposed data from May 11 until May 22, 2020. It found 175 attacks in just eight hours after the server deployed, with the number of attacks in one day totaled to 22.
“The first attack came on May 12, just 8 hours and 35 minutes after deployment. Our honeypot averaged 18 attacks per day,” Comparitech said in a statement.
Comparitech also pointed out that hackers used IoT search engines like Shodan.io or BinaryEdge To find vulnerable servers online. “Within just one minute of being indexed by Shodan, two attacks took place. It’s worth noting that over three dozen attacks occurred before the database was even indexed by search engines, demonstrating how many attackers rely on their own proactive scanning tools rather than waiting on passive IoT search engines like Shodan to crawl vulnerable databases,” the statement added.
Attackers Location
The researchers found attackers’ locations based on their IP addresses. The highest numbers of attacks originated from:
- 89 attacks came from the U.S.
- 38 attacks came from Romania
- 15 attacks came from China
Attack Methods Used
Researchers found that most requests were aimed at getting information about the status of the database and its settings. These include:
- 147 attacks used the GET request method
- 24 attacks used the POST method, which was particularly popular for attacks originating in China
- One attack used the PUT method with the intent to change the server configuration
- One attack used the OPTIONS method to get information about the connection
- One attack used the HEAD method to get the headers of requests without receiving the responses
All attackers were not looking to steal data. Some targeted servers to mine cryptocurrency, steal passwords, and destroy data, Comparitech stated.















