
The key message that came through at the Akamai Edge Live APAC Virtual Summit 2020 on July 2, 2020, was that the nature of cyberattacks on organizations was growing in scale and sophistication. And the only way to contain DDoS and other attacks and mitigate the impact was to opt for automation, sophisticated monitoring tools, and expertise provided by security operations centers (SOCs) and managed service providers (MSPs).
–Brian Pereira, Principal Editor, CISO MAG

Delivering the keynote, Dr. Tom Leighton, CEO and Co-Founder, Akamai, spoke about Internet security and some of the trends observed in the past few months. Dr. Leighton said, “There is a lot of business disruption out there… companies are dealing with the new reality. There are workforces working remotely, people are unable to travel, and this is creating a lot of security concerns. The trends that we are seeing on the Internet have been pretty much stable over the past few months. Traffic continues to be at a very high level and the attack rates continue to be very high. The bad actors are not disrupted by having to work remotely because they have been doing it for a long time, and they are trying to take advantage of the new situation, where the security levels could be lower with remote workforces.”
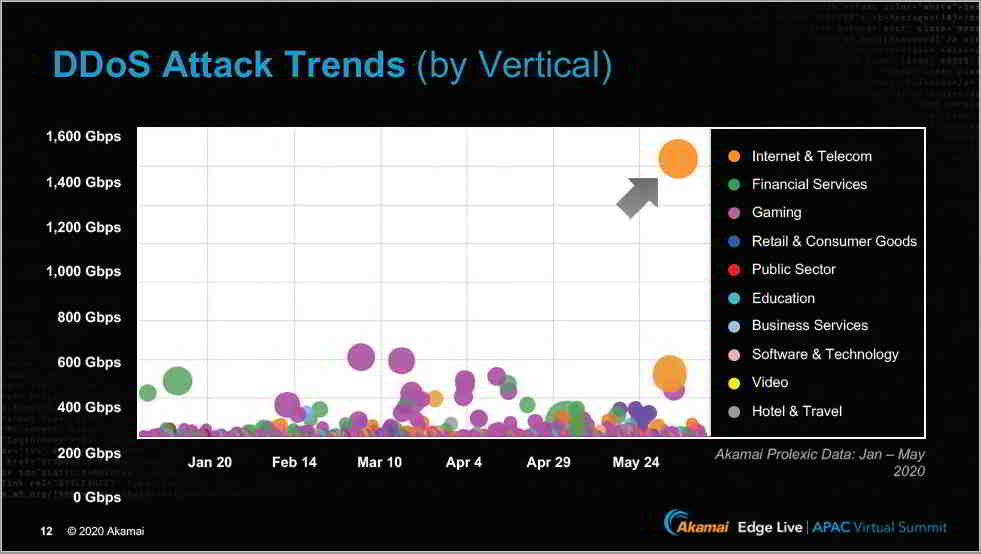
Dr. Leighton pointed out that there were a lot of DDoS attacks happening and companies in all industries were getting attacked. In recent weeks, there were targeted DDoS attacks on gaming companies, financial services, and internet and telecom firms.
He gave an example of a global DDoS attack against an internet hosting provider on June 4. The attack was huge and was directing 385 million packets per second at the server or 1.44 Tbps (Terabits per second) over a two hour stretch; there were 9 different attack vectors. Dr. Leighton said the bulk of the attack was “automatically and instantly mitigated” by Akamai Prolexic Services, which is a DDoS mitigation service for Terabit scale attacks. The remainder was mitigated by Akamai’s SOCC (global Security Operations Command Center).
“Our customer was able to maintain operations through a large DDoS attack,” said Dr. Leighton. The point he was trying to make was, the attacks are getting more sophisticated and targeted, and no single organization can block these on its own. DDoS attacks can be contained only with SOCC expertise and managed services, with automated capabilities.
Dr. Leighton also disclosed an on-going attack against a major gaming company. “There are 30 billion bot requests against this website and 6 billion malicious login attempts. These anomalies were identified and blocked by the Akamai Bot Manager and Akamai SOCC,” informed Dr. Leighton.
He also noted that web application attacks have grown 42% year-on-year. Web apps and their APIs continue to be exploited. Commerce, high-tech and financial services are the most targeted sectors for these types of attacks.
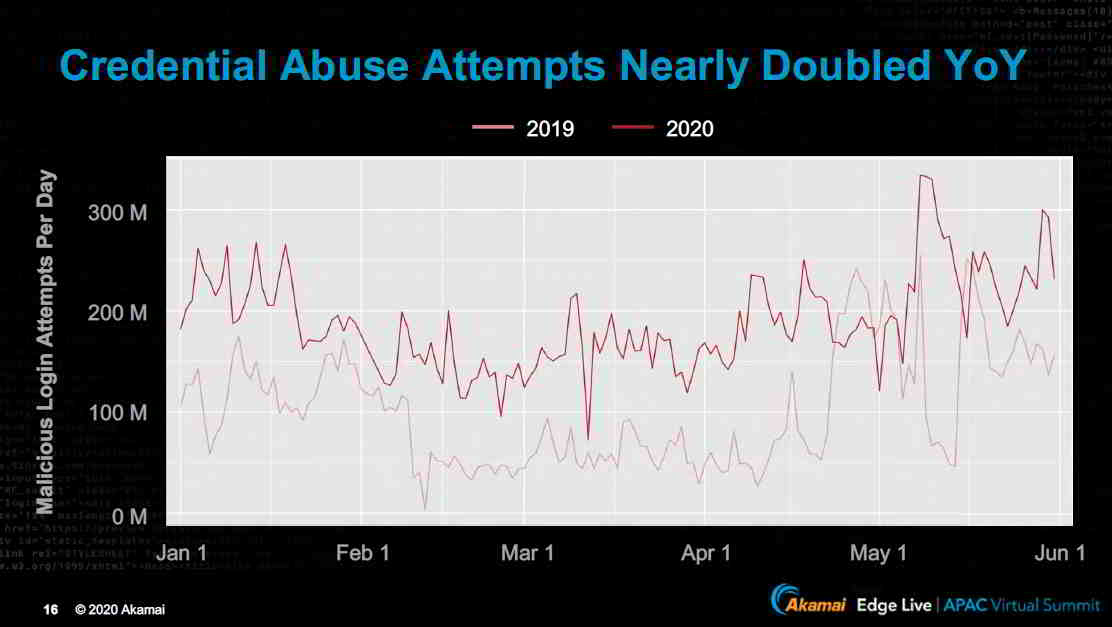
“Credential abuse attempts have nearly doubled compared to last year. Credential abuse attacks are the toughest and criminals are trying to take over accounts to steal merchandise, personal information and money,” said Dr. Leighton.
The other type of attacks that are increasing are malware injected by third-party scripts on retail websites. This is called Formjacking and the MageCart malware is the most infamous example.
“Third and fourth parties add their scripts to a shopping website, so most of what comes to a customer’s browser isn’t authored by the shopping website,” said Dr. Leighton. “61% of desktop content and 68% of mobile content comes from third parties.”
Compromised third-party scripts and domains can result in data breaches wherein customer credentials and card details are stolen.
John Summers, SVP and CTO, Akamai said there are typically 20 – 50 Javascripts executing on customers’ browsers when a web page downloads at their end. And each Javascript calls additional fourth and fifth-party scripts to enhance the customer experience.
Akamai offers a tool for anyone to test their page integrity at akamai.com/pageintegrity. With this tool one can determine from where their third-party and fourth-party content is coming from.










