
Security researchers from Trend Micro revealed that threat actors compromised government websites of eight U.S. cities across three states through Magecart card skimming attack. The attack occurs when users make a payment on the compromised Click2Gov website.
“These sites all appear to have been built using Click2Gov, a web-based platform meant for use by local governments. It is used to provide services such as community engagement, issues reporting, and online payment for local governments. Residents can use the platform to pay for city services, such as utilities. Breaches in these sites, however, are not new, in 2018 and 2019, the websites of several towns and cities using Click2Gov were compromised,” researchers said in a statement.
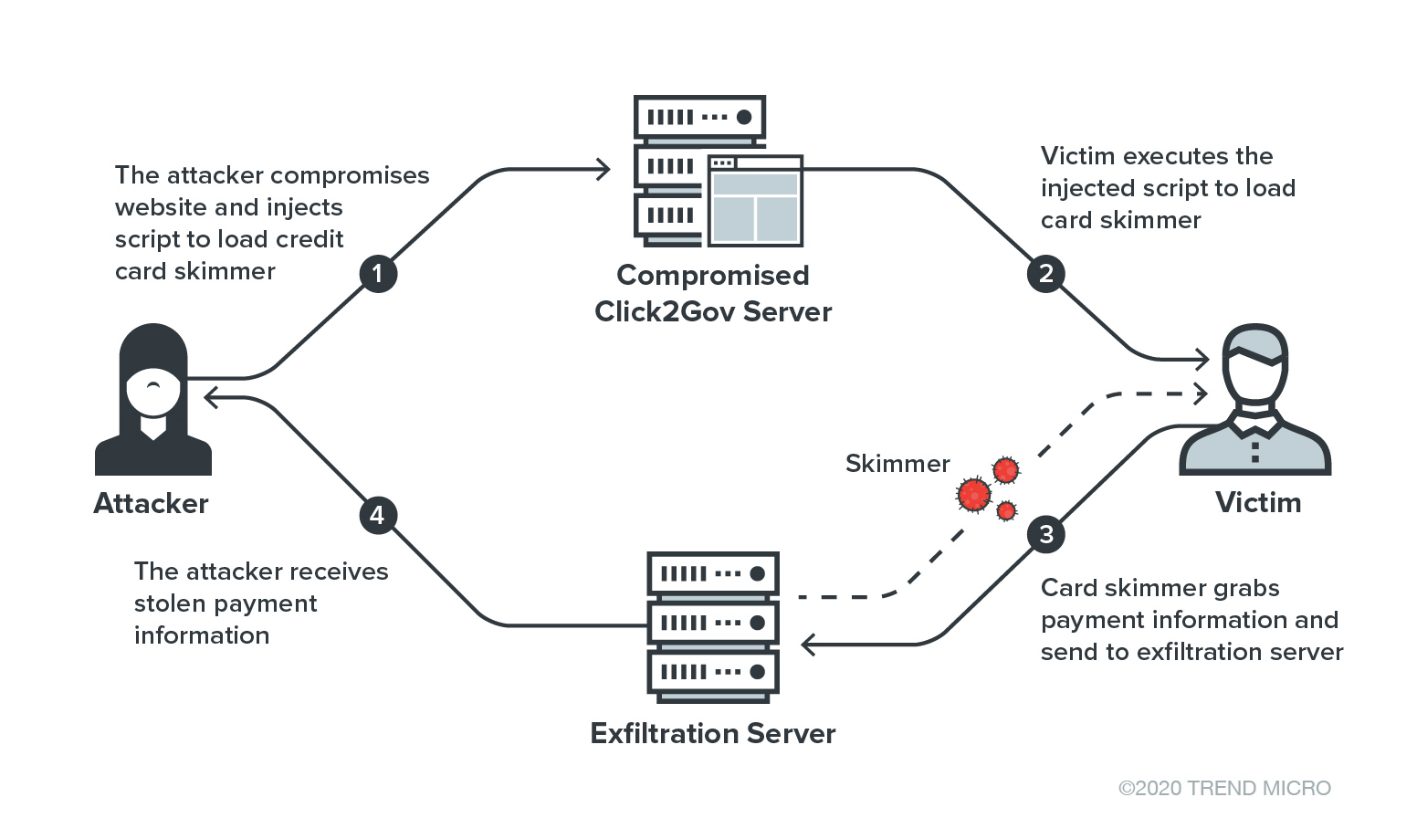
“Unlike other skimmers which grab data on various types of payment forms, the skimmer used here is rather simple and only works on a Click2Gov payment form. No obfuscation or anti-debugging techniques were used. The skimmer hooks the submit event of the payment form; when a victim clicks the button to send the payment information, the skimmer will grab the information from the selected columns inside the payment form and immediately send the collected information to remote server via a HTTP POST request,” the researchers added.
The attackers obtained users’ personal information like names, phone numbers, addresses, along with financial data like credit card numbers, expiration dates, and CVV details.
How Magecart Attack Works
Magecart attack, also known as web skimming or e-skimming, is a form of cybercrime where attackers plant malicious JavaScript code on online stores. In Magecart attacks, hackers gain access to a company’s website by compromising and hiding malicious code in it. The malicious code then collects the payment card information from users while making purchases on the infected site. Hackers either sell the stolen card data on the darknet or use it to make fraudulent purchases.
Not the First Time
Multiple security incidents have been reported on Magecart hackers. In its earlier security report, Trend Micro stated that Magecart attackers used a malicious code designed to steal the data from around 201 online campus stores that were catering to 176 colleges and universities in the U.S. and 21 in Canada. Hackers used a skimming script to compromise users’ card and personal details entered on the payment page.
Magecart Hackers Arrest
In a recent development, Indonesian Police and Interpol arrested three men who belong to Magecart hacking group for their involvement in Magecart attacks. The police officials stated that it is the first arrest of Magecart gang members. The suspects, identified by initials ANF (27 years), K (35 years), and N (23 years), were accused of injecting JavaScript sniffers into websites to capture information entered by the site visitors. It is said that the suspects allegedly used the stolen payment card data to purchase electronic and luxury goods.










