
The threat research team from security firm SonicWall Labs stated that they found multiple fake Aarogya Setu apps carrying spyware components.
Aarogya Setu is a smartphone application developed by the Indian government to help people assess themselves on the risk of infecting with Coronavirus. The app determines the risk if one has been near a COVID-19 infected person (within six feet distance) by scanning through a database of known cases across India. The app detects other devices via GPS or Bluetooth range and gets information about positive cases. The app gained huge popularity in the country; however, it also became a target for cybercriminals.
The SonicWall researchers also disclosed multiple scenarios on how these malicious apps function.
Scenario 1
The researchers stated that they found several fake apps with the package name “cmf0.c3b5bm90zq.patch”. It is observed that the malware operators used the same code for a majority of fake apps, by re-branding the icon and application name.

In this case, the app impersonates the legitimate Aarogya Setu App. However, the copy is imperfect, the icon appears stretched and can be identified by seeing along-side the legitimate app.
“Upon execution, we do not see any activity on the screen. However, after some time, the app icon disappears from the app drawer. This contains reference to a domain – johnnj2-37916.portmap.io – in the patch_preferences.xml file. During an analysis, the malware did not try to communicate with this domain, however this domain is connected to malicious apps,” the researchers said.
Scenario 2
Like in the first scenario, several fake apps have been found with the package name “yps.eton.application”. In this case, the app has been shown as an Aarogya Setu Add-on app, which is not an official app.
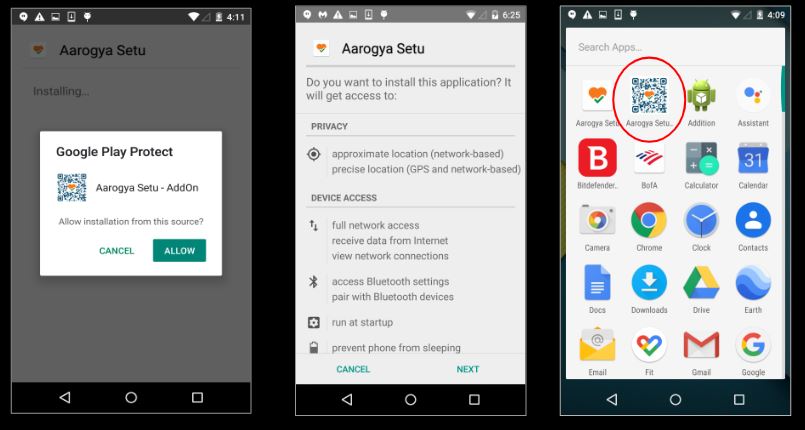
If the user installs the app, it requests for the Device-Admin privileges and permission for installation from this source. The fake app automatically installs the legitimate Aarogya Setu App from its resource folder to look less suspicious to users.
Scenario 3
In this case, hackers successfully duplicated the official Aarogya Setu icon, making it difficult to identify whether it is legitimate or fake. “There was no network activity witnessed during our analysis session but there was a record of a domain – 204.48.26.131:29491 – within an xml file belonging to the app. This domain is related to another malicious Android app,” the researchers said.

The common element in all the three scenarios is the containment of spyware components, which comprise malicious codes like the Android spyware SpyNote. Once downloaded, this spyware can make phone calls, recording audio, send SMS, take pictures, and record videos from the camera, and start the spyware every time the device reboots.
How to Delete Fake Apps
If the user deletes the Aarogya Setu app from the device by simple uninstalling method (by long pressing the icon), only the genuine app is removed, while the malicious app would still be available in the background of the device. The only way to remove the malicious apps is to remove it from settings > apps > uninstall.
Debasish Mukherjee, Regional Sales – APAC at SonicWall, said, “As the Aarogya Setu App gained popularity in India, it became a target for malware creators. The outbreak of Covid-19 has created new avenues for cyber attackers to explore, innovate and strike in every malicious way. With increasing cyberthreats it appears that cybercriminals are working overtime to create dissonance among mass app users. We advise Android users to exercise maximum caution while downloading and using the Aarogya Setu App.”
The Government of India made the Aarogya Setu app open source this week. The source code for Android is now available on GitHub and the Government has said that all future app updates will be made through this dedicated repository. This was reported by The Financial Express. Researchers and cybersecurity experts will now be able to audit the Aarogya Setu app at their full discretion. But hackers may also be taking advantage of this as they have access to the source code.










