
CYFIRMA, a Singapore-based cybersecurity firm, has released the India Threat Landscape Report 2020. The researchers at CYFIRMA have been actively observing global cyberattack trends and major state-sponsored threat actors using its cyber threat intelligence (CTI) platform, DeCYFIR. From time to time, it has warned private establishments and Indian Computer Emergency Response Team (CERT-In) authorities about the impending cyberattacks. It has helped them thwart some vicious campaigns aimed at top private companies, media, and the government itself.
Key Highlights
- Top threat actors targeting India’s digital frontier include the Lazarus group, APT36, MISSION2025, Stone Panda/APT10.
- The upcoming trends used to target Indian audience include ransomware, phishing and social engineering, reconnaissance activities, brute force and DDoS attacks, and commodity malware.
- Top attack methods used include attack on Linux servers, Email Servers, and web applications.
CYFIRMA’s India Threat Landscape Report 2020
In the Indian Threat Landscape Report’s summary, Kumar Ritesh, Founder and CEO of CYFIRMA, said,
India is a haven for startups, a fertile ground for technological innovation, sparking the generation of massive amounts of data that attracts cyber criminals. While digital adoption is breaking new grounds, the corresponding cyber maturity is low and not keeping pace with technological strides. All these factors are prompting more nations, especially India’s geopolitical foes, to partake in the cyber game targeting India. The Big 3, namely China, North Korea and Russia, authoritarian regimes that are suspected of aiding state-sponsored cybercriminal activities have shown interest in breaching India’s security perimeters.
The report highlights key findings such as top threat actors, evolving malware and their methodologies, tools used for targeting organizations in India, and much more.
Threat Actors and Their Attack Methods Targeting India
- Lazarus Group: The North Korean threat actors’ activities surged in 2020, which involved fileless attack, spreading new malware samples, attacking cryptocurrency businesses and more. They are believed to be using a new malware variant, known as COPPERHEDGE RAT, to target crypto exchanges.
- APT36/ Mythic Leopard: These are reportedly backed by the Pakistani government and known to have targeted Indian diplomats in the past. In H1 2020, the threat actors impersonated the Indian Government to send emails containing malware. These emails contained bogus health advisories on COVID-19. A spear-phishing campaign, aimed at computers belonging to the Indian Railways, was also detected.
- MISSION2025: Suspected to be a Chinese state-sponsored threat actor, this group has been active since as early as 2012. MISSION2025 is suspected of carrying out various campaigns against multiple industries such as Automotive, Retail, Healthcare, Energy, Media, Finance, and many more. The group is believed to have targeted other nations such as the U.S., the U.K., Japan, France, South Korea, Hongkong, and Thailand, for financial gains and/or corporate espionage.
- Stone Panda/ MenuPass/ APT 10/ Cloud Hopper: This Chinese threat actor group had traditionally shown interest in stealing international trade data and supply chain information from various enterprises across several countries such as India, Japan, Canada, Brazil, etc. It also tends to target Managed Service Providers (MSP), alongside Government agencies, Financial institutions, and entities in the Energy & Resources domain.
Top Attack Methods Used to Target India
The researchers at CYFIRMA observed a steady increase in attacks in H1 2020. They further studied these attack vectors and have listed the following methods as being the most potent forms of attacks to be used in H2 2020 and beyond.
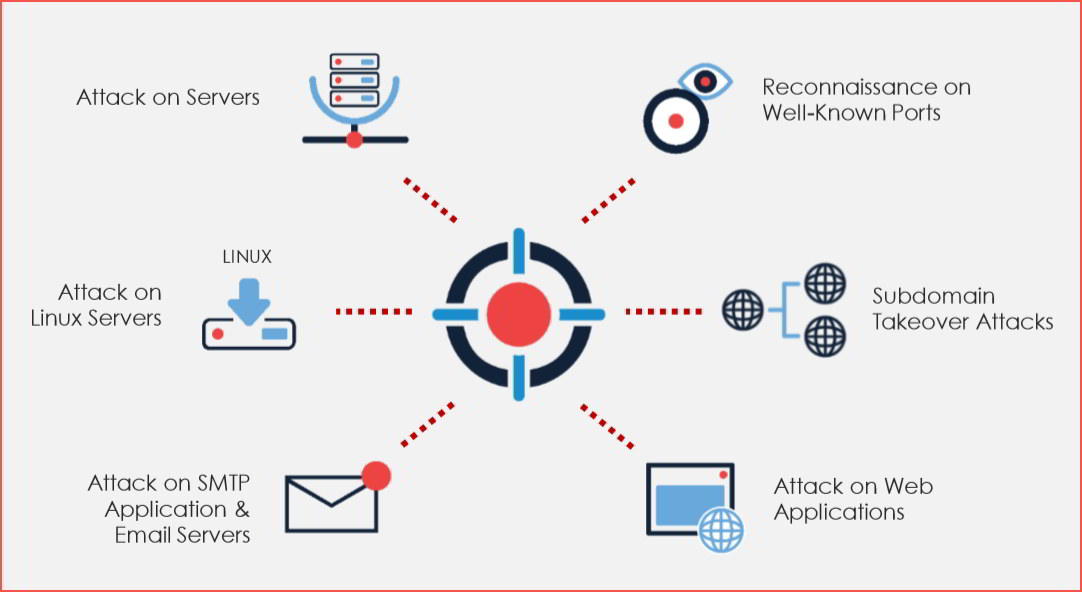
Malware Trends to Watch-out
H1 2020 saw criminal organizations, state-actors, and even well-known businesses being accused of deploying various malware targeting Indian businesses and organizations. Listed below are malware trends with a likely impact on India through H2 2020 and beyond.
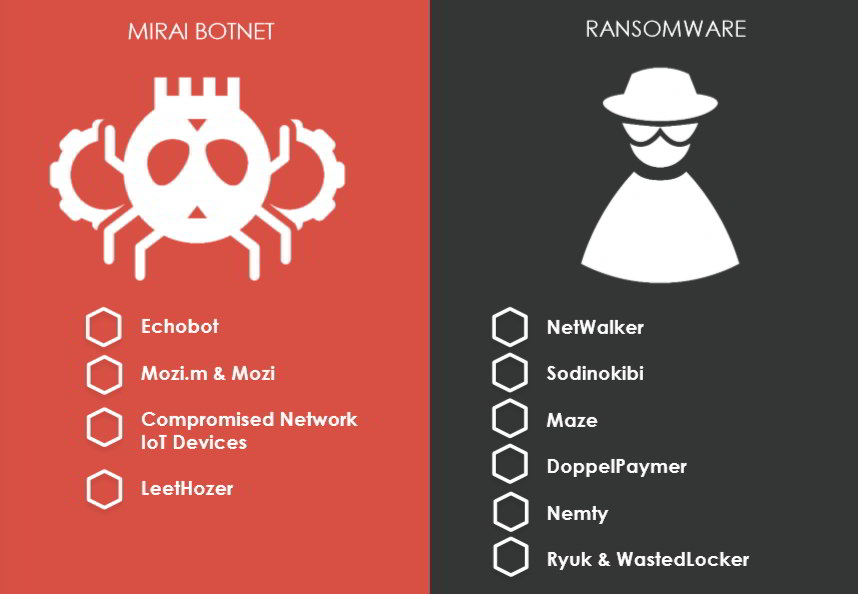
Related News:
CYFIRMA’s DeCYFIR Platform Can Predict Hacker Motives Before an Attack!










