
Security experts from risk protection solutions provider Digital Shadows found threat actors trading more than 15 billion usernames and passwords, including over 5 billion unique credentials on various hacking forums.
In its security investigation study, “From Exposure to Takeover,” Digital Shadows explained how cybercriminals exploit users’ stolen credentials to bank accounts, social media handles, and video streaming services to their advantage. The number of stolen and exposed credentials has increased to 300% from 2018 from more than 100,000 data breach incidents.
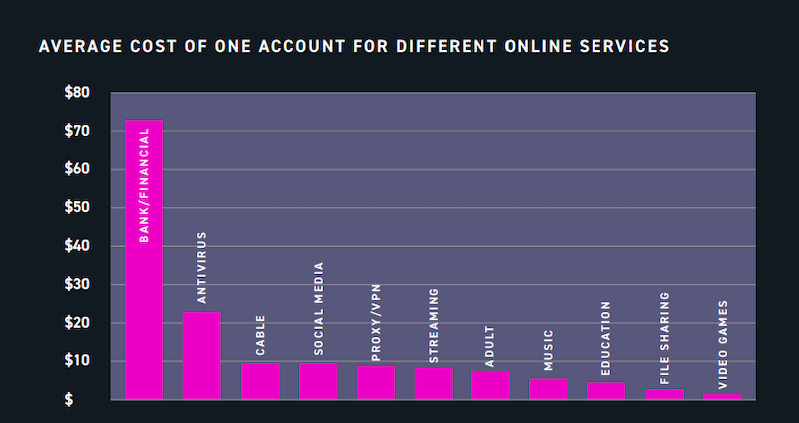
While most of the account details are made available on the dark web for free, the average amount that hackers trade on account is $15.43. The survey also highlighted that bank and financial account credentials are the most expensive commodities on the darknet, averaging from $70.91 to $500, depending on the quality of the account. The researchers also observed the growth of “account takeover as-a-service,” in which cybercriminals prefer renting a credential or fingerprint data like cookies and IP addresses for some period for less than $10, than buying it. Hackers also use dark web marketplaces to discuss various techniques on how to bypass two-factor authentication.
“Usernames with invoice or invoices were by far the most common advertised and comprise 66% of the 2 million usernames assessed. Partners and payments came in a distant second and third place, both with 10% each. Dozens of advertisements for domain admin access are also advertised, and in many cases, are being auctioned to the highest bidder with prices ranging from $500 to $120,000 – on an average $3,139. Digital Shadows cannot confirm the validity of the data that the vendors purport to own, but listings included those for large corporations and government organizations in multiple countries,” the report said.
Mitigation Measures
Researchers at Digital Shadows advised organizations to adopt certain security practices, these include:
- Monitor for leaked credentials of your customers, allowing you to take a more proactive response. Consider alerting your customers that their email has been involved in a breach, prompting them to reset their password if they have reused credentials
- Deploy an online Web Application Firewall. Commercial and open source web application firewalls can be used to identify and block credential stuffing attacks
- Increase user awareness. Educate your staff and consumers about the dangers of using corporate email addresses for personal accounts, as well as reusing passwords
- Keep an eye on the development of credential stuffing tools and monitor how your security solutions can protect against evolving capabilities. Some credential stuffing tools are able to bypass some CAPTCHAs, for example
- Some element of 2FA is always better than none but try to phase out multi-factor authentication using SMS. This can help to reduce account takeovers, but make sure this is balanced against the friction (and cost) it can cause










