
A report from global investigations firm Kroll revealed that ransomware attacks were the most observed security threats in 2020, accounting to one-third of all cyberattacks as of September 1, 2020. It highlighted that the impact of rising ransomware attacks on organizations globally of all sizes and sectors, with IT, professional services, telecoms, and health care sectors being the most targeted and affected.
Common Attack Gateways
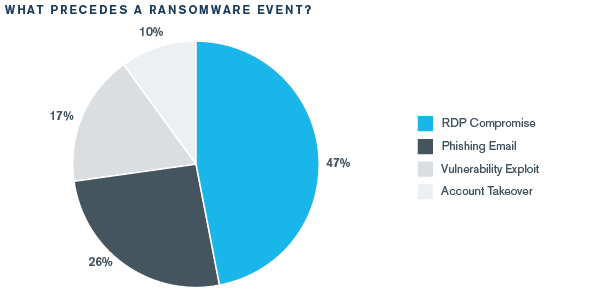
Kroll stated that in most of the ransomware incidents, attackers leveraged Open Remote Desktop Protocol (RDP) (47%), Phishing (26%), Vulnerability Exploits (17%), and Account Takeovers (10%). Attackers exploited Microsoft’s proprietary network communications protocol, Citrix NetScaler CVE-2019-19781, and Pulse VPN CVE-2019-11510 vulnerabilities to compromise user accounts. Besides ransomware, business email compromise (BEC) attacks remain a top threat for organizations globally followed by Unauthorized Access, Web Compromise, Malware attacks.
Top Ransomware Variants
Ransomware such as Ryuk, Sodinokibi, and Maze are the most observed variants so far in 2020, according to Kroll’s report. “After launching several high-profile attacks earlier in 2020, the actors behind Ryuk ransomware seem to have gone on a hiatus near the end of Q2. However, in Kroll’s experience, crimeware and their developers often have periods where they go dormant or spend time re-tooling, followed by a resurgence of activity,” Kroll said.
Ransomware actors target victims by encrypting their sensitive files, paralyzing operations, and demanding high ransoms. Kroll observed a new tactic of attackers threatening victims by posting the stolen data on darknet forums. Around 42% of ransomware variants are connected to a threat group actively exfiltrating and publishing victim data on the dark web.
Devon Ackerman, Managing Director and Head of Incident Response, North America, said, “While actors say they will delete data upon payment of the ransom, recent events belie that claim. Rogue members of ransomware groups have approached and demanded a second payment from at least two victims who had already paid a ransom. When one of the victims balked at paying the second time, the data, which was supposed to be destroyed upon the first payment, ended up on an actor-controlled site.”










