
Security experts from AddressIntel discovered a new strain of Android malware that exploits accessibility services in the compromised devices to steal users’ login credentials and media content. Dubbed “Oscorp” by Italy’s Computer Emergency Response Team (CERT-AGID), the malware prompts the user to install an accessibility service through which it can read what is present and typed on the screen.
The Oscorp Malware
Oscorp was identified in a domain supportoapp.com from which it downloads the malicious file clientassistance.apk uploaded to the remote server. Upon installation, the user is asked to enable the accessibility services, which will be used to access a series of permissions and establish communications with a C2 server to retrieve additional commands.
“If the user has not enabled the accessibility service, the malware keeps reopening the settings screen to do so. This way the user is pressured to accept in the hope that the screen will stop showing up. If the accessibility service is enabled, but the permission to access the device usage statistics is not enabled, the malware continually reopens its settings screen. This allows the accessibility service to automatically set permissions to the malware. Finally, the same mechanism is used to enable the malware to interrupt Doze mode and to obtain at least one of the permissions requested in the manifest,” CERT-AGID explained.
The permissions allow Oscorp to display various phishing pages when the user opens specific apps. Below is the list of permissions Oscorp asks:
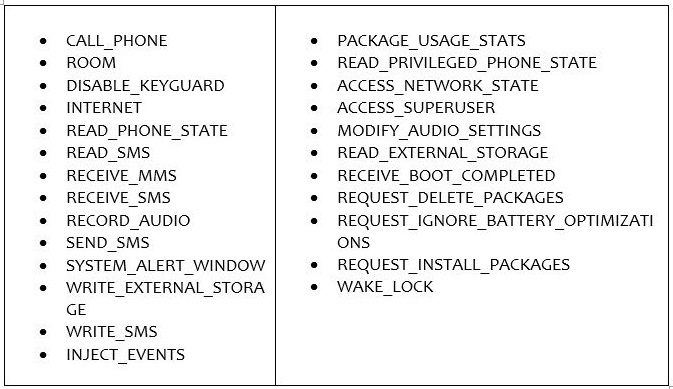
“As soon as the permissions are granted, a first call is made to ‘checkip.amazonaws.com’ from which it obtains the IP address of the compromised device and subsequently communicates with the C2 at this address ‘montanatony.Xyz’ on port 443. The C2 domain is reported in clear text within the APK but the commands for subsequent queries are obtained by decoding a series of strings encrypted with AES-CBC and embedded key,” CERT-AGID added.
Oscorp’s Capabilities
Oscorp malware leverages multiple capabilities to perform privileged actions automatically. These include:
- Enable keylogger functionality
- Automatically obtain the permissions and capabilities required by the malware
- Uninstall app
- Make calls
- Send SMS
- Stealing cryptocurrency
- Stealing the PIN for Google’s 2FA
While there is no evidence on what type of applications Oscorp targets, the CERT-AGID stated that this kind of malware mostly focuses on apps that store sensitive information like banking and messaging apps.










