Cybersecurity experts from Ironscales identified an organized spear phishing campaign targeting Microsoft 365 users in multiple business sectors including financial services, insurance, health care, manufacturing, and telecom industries. The researchers claimed that Microsoft failed to block spoofed emails that are sent from Microsoft.com. It is found that over 200 million Microsoft 365 users globally are targeted in this email spoofing campaign. Nearly 50% of phishing emails bypass Microsoft 365 Advanced Threat Protection (ATP).
“This spear phishing campaign is putting companies at high risk since even the savviest employees — those who know how to check sender addresses — are likely to perceive the message as legitimate. To date, almost 100 Ironscales customers with a combined total of a few thousand mailboxes have been targeted by this email spoofing attack,” Ironscales said.
How The Microsoft 365 Spoofing Attack Works
- Attackers send an email to Microsoft 365 users from a fraudulent domain that is a lookalike of the original brand’s domain.
- Threat actors then create a realistic email from sender “Microsoft Outlook,” to send malicious links or attachments to the users.
- Once clicked, users are directed to an imposter login page that asks users to enter their Microsoft 365 login credentials.
- All the harvested users’ credentials are then exploited by threat actors to perform scams or sell on the dark web.
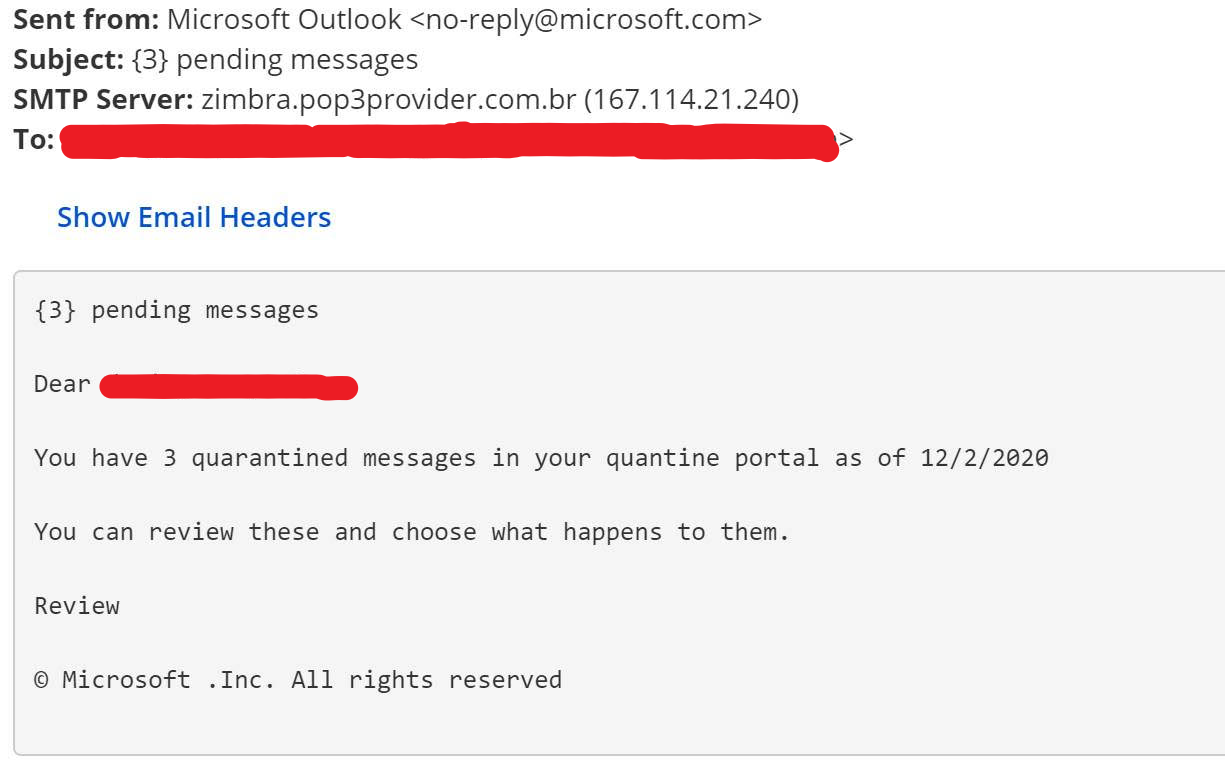
“Specifically, the fraudulent message is composed of urgent and somewhat fear-inducing language intended to convince users to click on what is a malicious link without hesitation. As inferred by the message, the link will redirect users to a security portal in which they can review and act on quarantined messages captured by the Exchange Online Protection (EOP) filtering stack,” Ironscales added.










