
This whitepaper is contributed by Tari Schreider, Chief Cybersecurity Strategist and Author, Prescriptive Risk Solutions, LLC
What is a Bug Bounty Program?
Bug or hacker bounty programs go by several names including vulnerability reward program, flaw disclosure, and hacker crowdsourcing. They all have one thing in common; they pay people for finding bugs in code. With few exceptions, programs pay cash for results. Once a bounty hunter submits proof of a vulnerability and the company sponsoring the program validates, cash is paid. Programs come in all sizes from small software companies who rely on voluntarily bug finding to large companies like Google and Facebook that pay out millions of dollars annually.
Today, several thousand companies offer a bounty program. HackerOne maintains what they claim is the most exhaustive list of known bug bounty programs.
How a program essentially works is you invite people to attempt to penetrate your network, web sites, etc. If they find a vulnerability, they document the flaw, you verify it and then issue a payment based on the conditions of your bounty. Easy peasy.
Bug Bounty Program Budgeting
Budgeting for a bounty program is a risk-based proposition. Ask yourself, what would it cost to fix a bug in production versus development or testing? Next, determine if that has ever happened, I am sure it has. Keep in mind that you only pay for successes in a bounty program. How much does it cost to keep a team of in-house security testers employed to find minimal bugs?
You can design a bounty program around any budget, even free, well almost – you still have to pay for using the platform. Bounty hunters want to make a name for themselves so some will work with programs that only provide kudos for finding bugs. This goes toward building their reputation and goal of becoming a much sought after super bug hunter.
Consider structuring your program around the priority rating of the bugs found. You may feel you want your bounty dollars to go only toward finding critical bugs and not those that pose an acceptable risk. Funding for the program can also be subsidized my marketing, as it is a way to promote your company as doing the right thing.
Penetration Testing vs. Bug Bounty Programs
Bounty programs have introduced an interesting argument, should I reduce my security testing staff and essentially outsource my security testing through a bug bounty program? In my experience, my clients that have compared results of in-house testing versus a bounty program has stated that bounty programs were far more successful in finding critical code flaws fast. The two main reasons are one, internal security testers do not think like hackers and two, the shear metric tons of hacker brainpower who are financially motivated to find bugs.
Penetration testing has become too bureaucratic with lawyers, contracts, rules of engagement, etc. I have seen many penetration testing projects take weeks or months to negotiate all while a bug bounty program at similar companies finding dozens of bugs in that same period of time. Now I am not advocating eliminating penetration testing from the mix, but rather that you consider it as an essential strategy to fast-path security testing of public facing critical code.
Unique Bug Bounty Programs
Bounties paid by companies can average from $200 to $200,000; however, an average reported by bugcrowd was $505.79. With a growing number of bounty hunters and bounty platforms, companies are looking for ways to gain notice by the industry’s top bug researchers. United Airlines for example offers frequent flyer miles.
The following are several bounty programs that standout from the crowd:
| Company | Bounty |
| Apple | $200,000 for highest category of bug – secure boot firmware bugs. |
| Donations to charities in conjunction with bounties. | |
| Hack The Pentagon | Pilot bug bounty program of $150,000 for hackers in return for the vulnerabilities they find in its public facing websites. |
| Kraken | Payments made in bitcoins. |
| Netgear | Submit a chain of bugs to receive a bonus. |
| PayPal | Payments made to a PayPal account. |
| Uber | Hacker loyalty reward program and bug treasure map. |
| United Airlines | 50,000 to 1 Million award miles. |
I suggest you work with your organization’s marketing department to come up with a unique and noticeable bounty payment to attract the best bug researchers. You certainly do not want to do what Yahoo did in 2013 and offer t-shirts to bug hunters for finding critical bugs in their code. This touched off such a hail of negative press against Yahoo the press referred to the incident as t-shirt gate. So a word to the wise, really think through what message your bounty program sends.
Bug Bounty & Disclosure Programs
A great way to model your bug bounty program is to view what other organizations have implemented. Thanks to bugcrowd and HackerOne, you can view nearly 2,000 with just a click of your mouse. Bugcrowd maintains an updated list on bounty and disclosure programs with direct links to respective program sites.
Think of this as security crowdsourcing of thousands of white hat hackers and professional security vulnerability researchers.
Bugcrowd can manage your program through a number of programs ranging from public (collective of thousands of hackers and researchers), private (invite only researchers) or on-demand (project-based invited researchers).
Bugcrowd provides a template for branding your bounty page, handles bounty payment, performs bug reporting triage and validation as well as provides comprehensive reporting on your program.
Bounty programs are effective and indispensable to your SDLC or DevOps operations. HackerOne and Detectify are two other bounty platforms you may wish to compare to bugcrowd. Bounty Factory is a European-based platform that focuses on EU rules and regulations related code flaws.
If you are just looking for a list of bug bounty programs, checkout bugsheet. This site offers a curated list of over 370 programs offering a collective 150 bounties.
Evolution of Bug Bounty Programs
Bounty programs have been around for many years. Jarrett Ridlinghafer while working at Netscape in 1995 established the first bounty program. He also coined the phrase “Bugs Bounty.”
Programs have progressed from casual in-house programs to sophisticated managed programs attracting only the highest profile bug hunters and everything in between. Bounty hunting has become an industry with providers ranging from hunters who just triage code with vulnerability scanners looking for low hanging fruit counting on the fact the sponsoring company never bothered to scan their own code to professional bug researchers.
Bounty hunting has also created a new breed of super hunter who devote their full-time energies to finding bugs as a profession.
What Type of Bugs are Found?
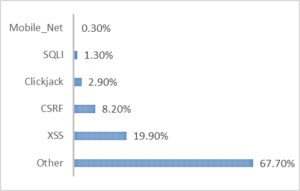
Bugcrowd reports the following types of critical bugs found by their researchers:
Bug Bounty Program Tips
- Brand your program – marketing matters and bounty programs attract public attention.
- Make your program payout unique – you want to attract the most experienced bug hunters.
- Use a commercial bounty program management platform – do not reinvent the wheel.
- Clearly document the types of bugs you are willing to pay – ambiguous hunter instructions leads to wasted time and money.
- Scan your code before releasing it for bounty – you do not want to pay for bugs you should have caught.
- Structure a loyalty program to attract the best bug hunters – build a rapport with your star hunters.
- Integrate the bug bounty in DevOps – focus on finding bugs in development.
- Carefully document dupe flaws – the fastest way to tank your bounty program is to issue the kirk response “dupe” without proof.
- Expect poor submissions – over 90% of bounty programs will have little to no value, many researchers do not read the bounty guidelines.
- Expect your network probing – once the bounty is announced, researchers will start probing your network.
Conclusion
Bug bounty programs are a great strategy to include in your arsenal of secure coding and testing processes. They provide a vulnerability perspective that in-house programs typically cannot. These programs are ideal for due diligence and fast-pathing testing on highly visible and critical web sites. Invitation only bounties have approximately twice the success rate as public bounties due primarily to the quality of the bug researchers attracted, but they do cost more. Overall, this is something to consider in your mix of cybersecurity program practices.










