
Cybersecurity researchers from ESET have discovered a new backdoor malware deployed by the scandalous Lazarus hacking group to target freight and logistic organizations in South Africa. Dubbed Vyveva, the malware is capable of performing certain backdoor functionalities like exfiltrating files, harvesting information from an infected system, and running arbitrary code by remotely connecting to a command-and-control (C2) server. The malware also leverages fake TLS connections for network communication to connect to its C2 via the Tor network. While Vyveva was first spotted in June 2020, the researchers stated that the malware could have been active since 2018.
The Lazarus Link
Lazarus is a North Korea-based hacking group active since 2014 and accused of several cybercriminal acts. It has often targeted global companies with new malware strains such as AppleJeus, Fileless, ThreatNeedle, and MATA.
ESET researchers stated that the new Vyveva malware has similarities to Lazarus’s NukeSped malware. Besides, malware functionalities like using fake TLS in network communication, command-line execution chains, and the way of using encryption and Tor services are similar to Lazarus operations.
“Our telemetry data suggests targeted deployment as we found only two victim machines, both of which are servers owned by a freight logistics company located in South Africa. The backdoor features capabilities for file exfiltration, timestomping, gathering information about the victim computer and its drives, and other common backdoor functionality such as running arbitrary code specified by the malware’s operators. This indicates that the intent of the operation is most likely espionage,” security researcher Filip Jurčacko said.
Vyveva’s Components
So far, the researchers found three components of Vyveva malware – Installer, Loader, and Backdoor.
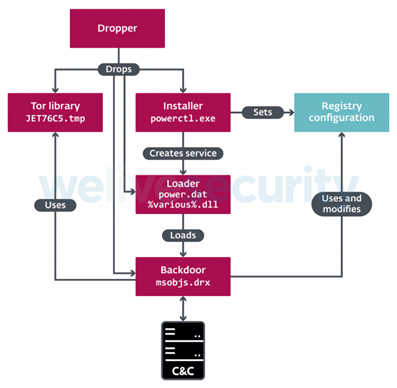
Among its various capabilities, the Vyveva backdoor allows attackers to alter any file’s date using metadata from other files on the system or by setting a random date between the years 2000 to 2004.
Besides, Vyveva uses the Tor library based on the official Tor source code to communicate with a C&C server at three-minute intervals. The Tor library transfers information about the victim system and its drives before receiving commands. And the backdoor function exports the directory contains – TorSocket.dll with self-explanatory exports close_ch, connect_ch, open_ch, read_ch, write_ch.
“Vyveva constitutes yet another addition to Lazarus’s extensive malware arsenal. Attacking a company in South Africa also illustrates the broad geographical targeting of this APT group,” Jurčacko added.
Lazarus’ Recent Threat Activity
A recent joint advisory from the FBI, the Cybersecurity and Infrastructure Security Agency (CISA), and the U.S. Department of Treasury (DoT) revealed that the Lazarus hacking group is using different kinds of AppleJeus malware to target cryptocurrency exchanges and crypto-wallets. The agencies stated the Group developed seven fake cryptocurrency trading applications Celas Trade Pro, JMT Trading, Union Crypto, Kupay Wallet, CoinGoTrade, Dorusio, and Ants2Whale to steal cryptocurrency. Read More…










