
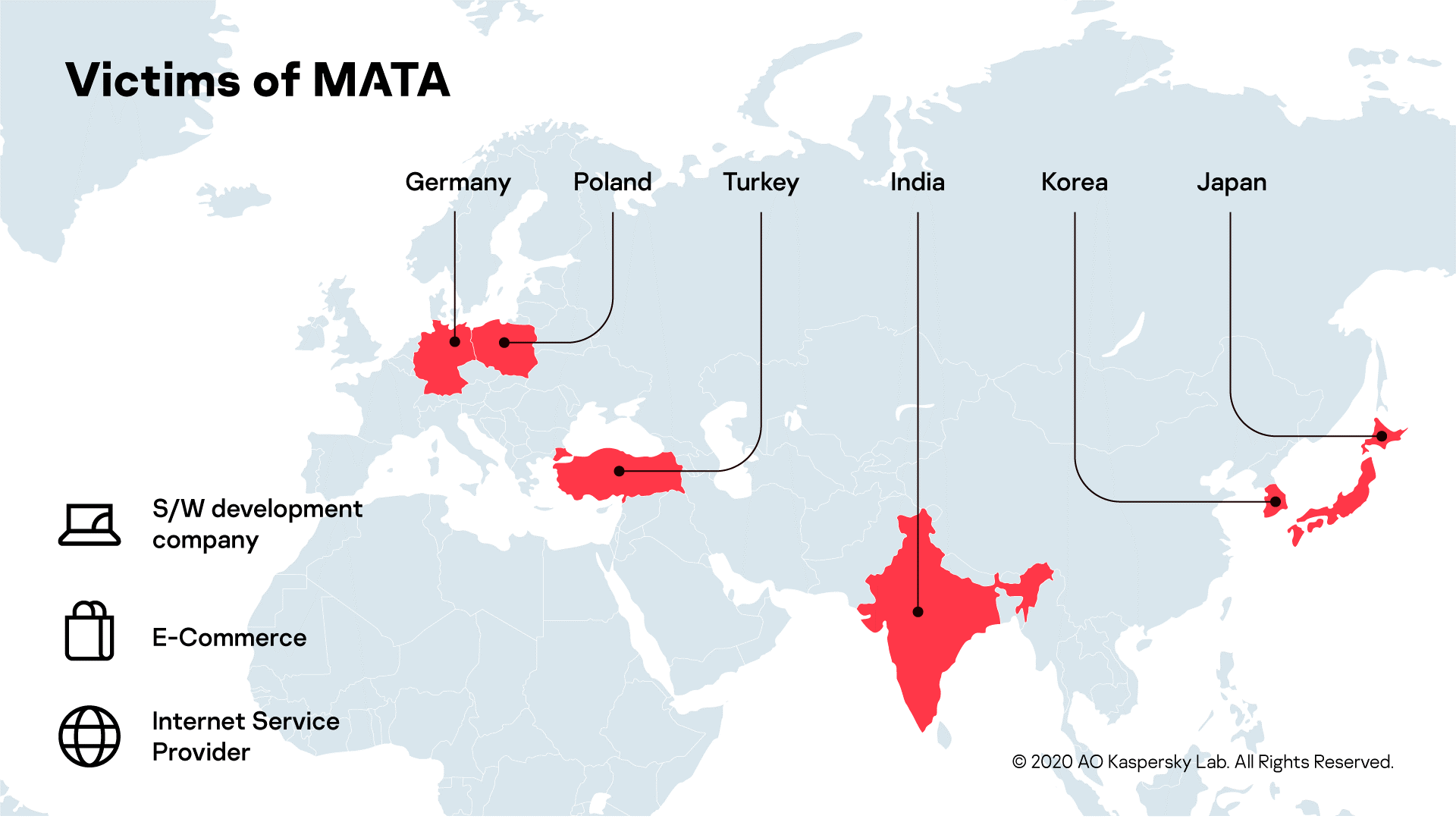
Threat intelligence team at Kaspersky warned about a new malware campaign linked to the infamous North Korean Lazarus hacking group. Dubbed as “MATA,” the malware targeted e-commerce and IT firms in Poland, Germany, Turkey, Korea, Japan, and India to spread ransomware and steal sensitive information. The MATA malware possesses several components like loader, orchestrator, and plugins to infect Windows, Linux, and macOS operating systems.
Researchers stated that the MATA malware campaign began as early as April 2018. “The actor behind this advanced malware framework used it aggressively to infiltrate corporate entities around the world. We identified several victims from our telemetry and figured out the purpose of this malware framework,” the researchers said.
How MATA Spreads
According to Kaspersky, MATA malware is used to load plugins into the operating system’s running commands to infect and manipulate files and processes by injecting DLLs, creating HTTP proxies, and tunnels on targeted Windows devices. Once the malware successfully deployed, the attackers find databases with customers’ sensitive information and run database queries to acquire customer data.
“During our research, we also found a package containing different MATA files together with a set of hacking tools. In this case, the package was found on a legitimate distribution site, which might indicate that this is the way the malware was distributed. It included a Windows MATA orchestrator, a Linux tool for listing folders, scripts for exploiting Atlassian Confluence Server (CVE-2019-3396), a legitimate socat tool and a Linux version of the MATA orchestrator bundled together with a set of plugins,” the researchers added.
The Lazarus Timeline
The Lazarus hacking Group was involved in multiple cyberattacks earlier. In 2018, Kaspersky uncovered AppleJeus, a malicious operation by Lazarus Group to intrude on cryptocurrency exchanges and applications. In December 2019, the researchers discovered a malware dubbed as “Fileless” distributed by the Lazarus group. According to the security researchers, the hacking group was spreading malware targeting MacOS users, to create fake cryptocurrency trading applications.










