“Meow” seems to be on the prowl of unsecured Elasticsearch and MongoDB databases on the web. We’re not talking about cute, furry four-legged creatures. Rather, a new form of attack that is “fast and searches and destroys new clusters pretty effectively,” tweeted Bob Diachenko, a cybersecurity specialist, known to find potentially threatened and unsecured databases in the cyberspace.
— Bob Diachenko (@MayhemDayOne) July 20, 2020
The speed and agility of the attack indicates that it is a bot attack, which detects and destroys its target almost immediately. He further notes that attackers do not have any monetary intention behind the “Meow” attack. It does not leave any ransom note or explanation behind the attack and simply deletes the data without intimation to its owner.
Meow’s Discovery
The attack is called “Meow,” due to the fact that the attacker renames databases, its tables, and indices by appending “-meow” to the end of the original or randomly generated alphanumeric names.
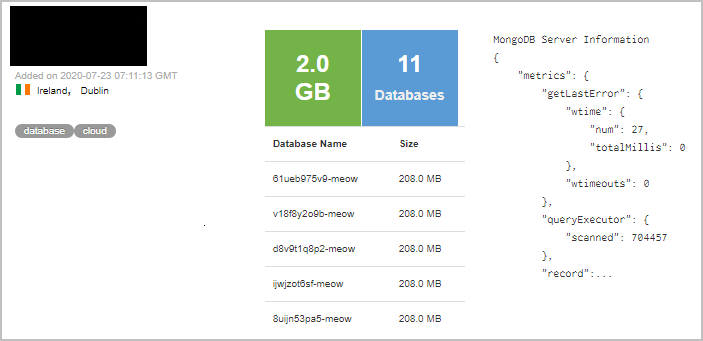
Diachenko, who leads the cybersecurity research team at Comparitech, first discovered this type of attack on a Hong Kong-based VPN provider company, UFO VPN. It failed to secure a database consisting of user logs and API access records including plain text passwords and other information of their users. This discovery was made on July 1, 2020 and was spontaneously reported to the parent company. UFO secured the exposed database on July 15 only to be “Meowed” by the attackers within next four days.
On July 19, 2020, another dataset of UFO appeared on a different IP address, which seemed to have an even greater number of records exposed. This time though it was not noticed by anyone but by “Meow” bots. The user logs and API access records potentially included the following info:
- Unencrypted user account passwords
- VPN session and tokens details
- User devices and connected VPN server IP addresses
- Timestamps
- Geo-tags
- Device and OS information, etc.
Looking at the pattern and nature of the attacks, it is being said that the attacker can be a vigilante trying to teach a lesson on securing databases the hard way by destroying the unsecured ones.










