
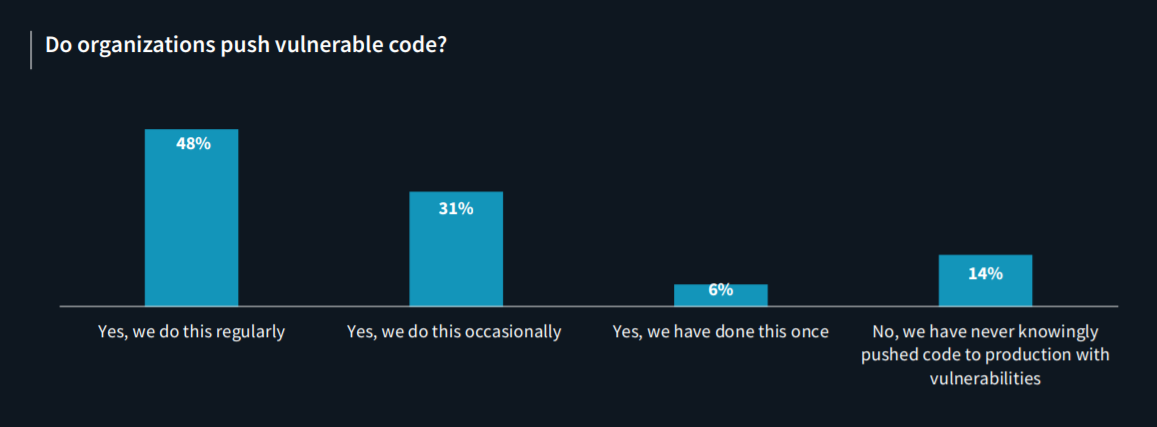
According to a research report from Synopsys, 48% of organizations deliberately push vulnerable code in their application security programs due to time pressures. As a result, 60% of respondents stated that their production applications were exploited by OWASP top-10 vulnerabilities in the past 12 months.
The report entitled “Modern Application Development Security” highlights the extent to which security teams understand modern development and deployment practices, and where security controls are required to lower the risk.
Pushing Vulnerable Codes
The research stated that certain organizations push vulnerable codes knowingly and with a thorough understanding of the risks that they are taking.
“Application security requires a constant triage of potential risks, involving prioritization decisions that allow development teams to mitigate risk while still meeting key deadlines for delivery. Note that vulnerabilities discovered too late in the cycle often don’t get mitigated, reinforcing the importance of shifting application security as far left as possible to leave enough runway to resolve critical issues in time for delivery,” the report said.

Other insights from the study include:
- Most organizations believe their application security program is effective, though many still push vulnerable applications into production. 69% of survey respondents rate the efficacy of their current program as an 8 or higher on a scale of 0 to 10 (with 10 being the most effective). However, as nearly half of the organizations consciously push vulnerable code on a regular basis, most have experienced production application exploits involving OWASP Top 10 vulnerabilities in the past 12 months.
- DevOps integration is a critical element for improvement. More than one-quarter of respondents say that their current application security tools add friction and slow down development cycles, while 23% identify poor integration with development/DevOps tools as a common challenge. Additionally, 26% of respondents note a difficulty with or lack of integration between different application security vendor tools as a common application security challenge.
- Developers play an important role in application security, but they lack the skills and training. Nearly one-third (29%) of respondents express that developers within their organization lack the knowledge to mitigate issues identified by their current application security tools. Furthermore only 17% say that their developers utilize just-in-time training available within their security tools and just 29% are required to participate in training at least once per quarter.
- Organizations are planning to increase application security spending. More than half (51%) of respondents report plans for significant increases in application security spending over the next 12 months. 44% plan to target application security investments toward cloud.
- AppSec tool proliferation is driving many organizations to invest in consolidation. Many organizations are struggling to integrate and manage the number of tools in place, often leading to a reduction in the effectiveness of their security program while also directing an inordinate amount of resources to manage them. With 70% utilizing more than ten tools, complexity becomes a key issue, and as a result, more than a third are focusing investments on consolidation.
Patrick Carey, Director of Product Marketing for the Synopsys Software Integrity Group, said, “The key insights identified within this study underscore the fact that organizations need to address application security holistically throughout the development life cycle. Of the organizations consciously pushing vulnerable code into production, 45% do so because the vulnerabilities identified were discovered too late in the cycle to resolve them in time. This reaffirms the importance of shifting security left in the development process, enabling development teams with ongoing training as well as tooling solutions that complement their current processes so that they may code securely without negatively impacting their velocity.”










