The outgoing President of the United States, Donald J. Trump, has been extensively grabbing headlines for his and his supporters’ actions. With his name being one of the most trending keywords globally, cybercriminals are trying to make the best of the situation with fake threads indicating a sex tape of the departing POTUS. The Java Archive (JAR) file called “TRUMP_SEX_SCANDAL_VIDEO.jar” is a new remote-access trojan (RAT) variant that aims to lure unsuspecting users to deliver a malware package.
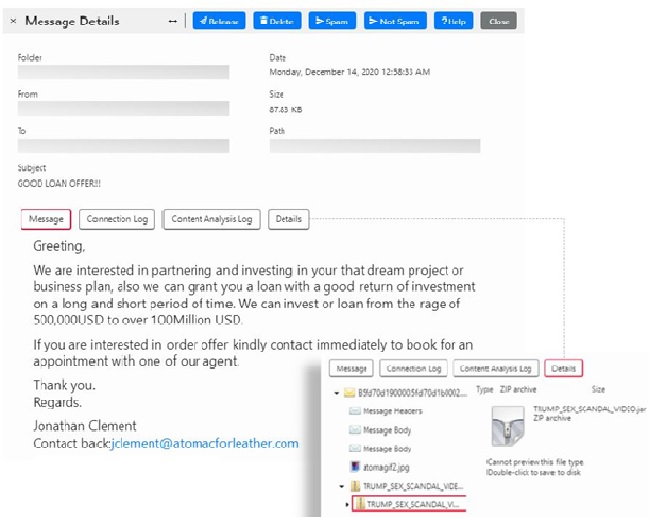
Researchers at Trustwave were the first to stumble upon this new thread while reviewing their spam traps. The most peculiar thing about the campaign was that, on the surface, it appeared like a typical investment scam with the subject “GOOD LOAN OFFER” but had an attachment called TRUMP_SEX_SCANDAL_VIDEO.jar— unrelated to the email theme.
The RAT file is of an unusual kind. Named as “QNODE DOWNLOADER,” this a variant of earlier seen Node.Js QRAT downloaders. Once a user clicks on the attachment, a copy is created and then executed from the %temp% folder while the user is greeted with a pop-up message that reads, “remote access software and is mainly used for penetration testing”. As soon as a user clicks “Ok, I know what I am doing,” the malicious activities begin.
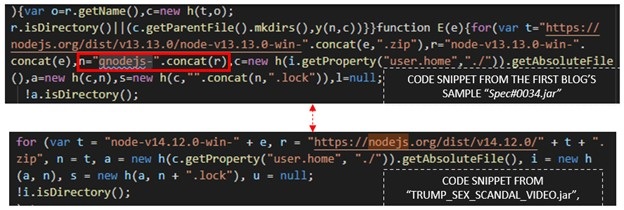
“Third, the string “qnodejs” which previously identified the files associated with this threat, is not in this variant,” the researchers noted. “The Node.Js installation folder is still at %userprofile%, however, the folder is not prepended with “qnodejs-“ anymore. Fourth, when downloading next stage malware, only the argument “–hub-domain” is required when communicating to the command-and-control servers (C&Cs). After setting up the Node.Js platform, a Node.Js process is created to download the next malware in the infection chain. The argument “–hub-domain” along with the C&Cs is the only data supplied to the process. The information about the QHub service subscription user we observed in the earlier variant is no longer contained in the JAR file.”
And in the end, JAR file downloads a file named “boot.js” and saves it at: %temp%\_qhub_node_{random}.
In comparison to the previous variant, the new one is significantly enhanced to infect the system with a QNode RAT. Several characteristics and behavior were also improved. These include downloader being split-up into different buffers inside the JAR to evade detection, names of the other files it created and downloaded being changed put into different locations, and not inside the Node.Js installation folder, among several other new features.
What is QRAT?
A Qua or Quaverse Remote Access Trojan (QRAT) is a Java-based RAT, which first made its appearance in 2015. The Trojan can be used to gain complete take over of a compromised device. It was initially advertised as a SaaS Java RAT.