The latest string of Ryuk ransomware attacks on multiple U.S. hospitals is a cold reminder of a similar methodology implied by WannaCry operators back in 2017. The cybercriminals who are reportedly from the Eastern European region have already targeted multiple hospitals in Oregon, California, and New York. The extent of disruption can be gauged from the fact that six hospitals targeted on the same day have already been forced to go offline and revert to pen and paper to continue operations.
Following the tough task of maintaining cyber safety and security from such a penetrative and destructive form of cyberattack, CISA, FBI, and DHS, have jointly issued a red alert to all hospitals and health care institutes across the U.S.
Key Highlights
- CISA, FBI, and DHS (also known as HHS) have found that malicious cyber actors are targeting the HPH Sector with Trickbot malware, often leading to a Ryuk ransomware attack, data theft, and the disruption of health care services.
- The so-called UNC 1878 hacking group is said to be behind these attacks.
- Multiple hospitals in Oregon, California, and New York, have already been hit with a wave of new Ryuk ransomware variant forcing them to go offline.
The Big Game Hunting
GRIM SPIDER, a subset of WIZARD SPIDER cybercrime group, had been operating the Ryuk ransomware since August 2018, targeting large scale enterprises for a high-ransom return. This methodology of targeting the bigger enterprises is called “big game hunting,” which the GRIM SPIDER seems to have successfully employed ever since. Their operations were always limited to banking and financial institutions in the European region, however, off late, there seems to be a shift in the operational geography for the Ryuk ransomware operators. They have zeroed down on the health care sector in the U.S. which is currently highly overworked, vulnerable, and more valuable than the other sectors; as many hospitals and institutes are actively researching and testing probable vaccination candidates during the ongoing COVID-19 pandemic.
Related News:
Sopra Steria Confirms Being Hit by New Variant of Ryuk Ransomware
Adam Myers, SVP for Intelligence at CrowdStrike said, “The recent Ryuk attacks on U.S.-based hospital systems indicate the continued proliferation and evolution of ransomware. Among the 25 adversaries CrowdStrike tracks that are engaged in Big Game Hunting (a.k.a. Enterprise Ransomware), we’re seeing two categories emerge: ransomware-as-a-service groups that adopt a revenue-share model, and closed groups, such as WIZARD SPIDER’s TrickBot, who fully manage ransomware operations and reap all the benefits. We have also witnessed a disturbing trend in the last 18 months in which adversaries are moving beyond encrypting files to exfiltrating data and threatening to release it if demands are not met. In fact, in some cases the attackers demand two ransoms – one to delete the data and another to decrypt it.”
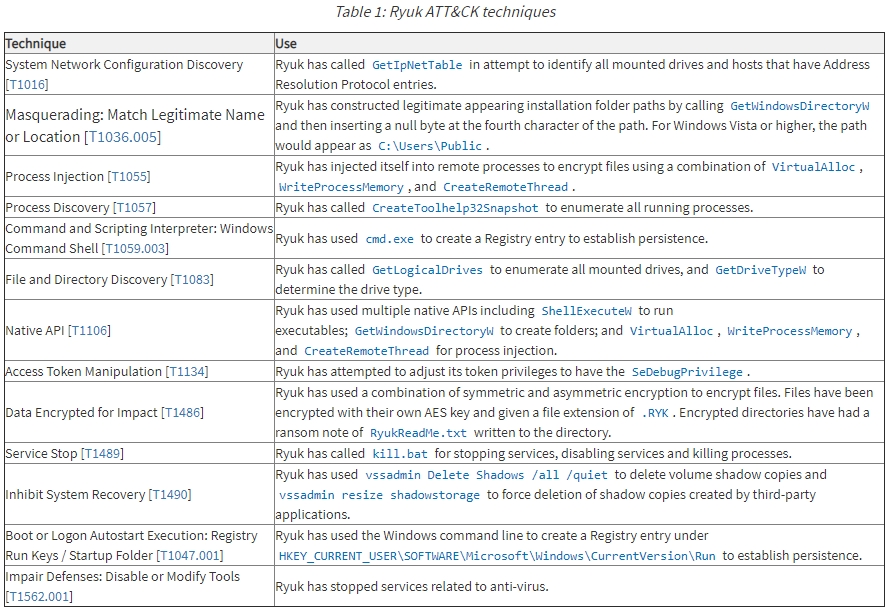
According to MITRE, Ryuk uses the following ATT&CK techniques:
CISA Says…
In its advisory, CISA has actively urged the HPH sector to patch its operating systems and implement network segmentation as primary mitigation steps against such ransomware attacks. It also recommended not paying ransoms, stating that it may encourage threat actors to target additional organizations.
To have a quick and effective incident response in an event of a ransomware attack, CISA urged organizations to “Regularly back up data, air gap, and password-protect backup copies offline.” It added, “Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, secure location.”
Related News:
Ryuk Ransomware Campaign Targets Port Lavaca City Hall
North Korea Behind ‘WannaCry’ NHS Cyberattack: UK










