
Security researchers have warned that hackers could take advantage of unsecured connected devices to take control of corporate networks. A recent report from Shadowserver Foundation, revealed that internet-connected printers at corporate enterprises expose sensitive information like device names, locations, device model, firmware versions, organization names, IPP (internet printing protocol) port, and WiFi SSIDs.
Researchers at Shadowserver scanned around four billion routable IPv4 addresses to find connected printers that are exposing their IPP port. They found around 80,000 printers exposing themselves online via the IPP port per day.
“We scan by sending an IPP Get-Printer-Attributes request to TCP port 631. We started regular scanning of all 4 billion routable IPv4 addresses on June 5, 2020, and added Open IPP reporting as part of our daily public benefit remediation network reports on June 8, 2020,” the researchers said.
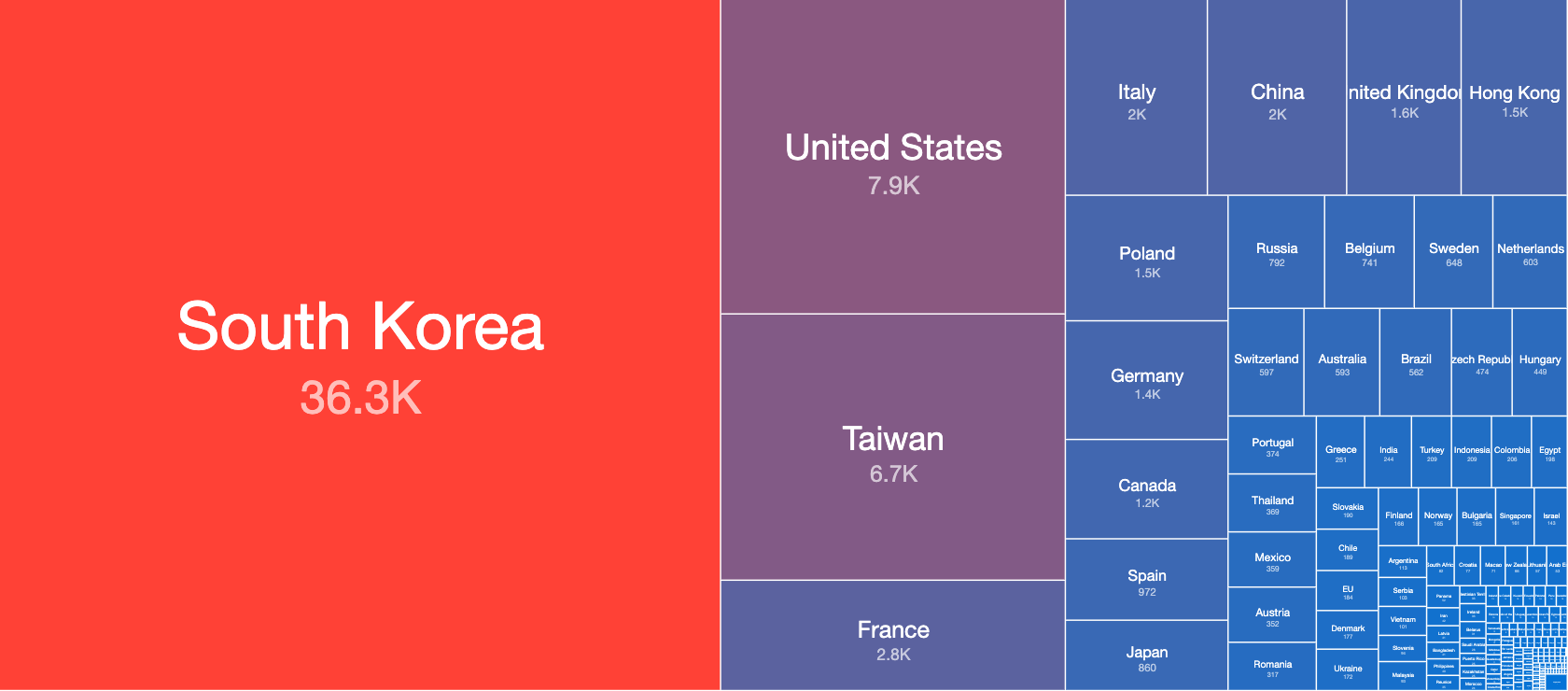
According to researchers, South Korea (36.3k) is the most affected country due to unsecured IPP ports, followed by the U.S. (7.9k), Taiwan (6.7k), and France (2.8k).
How IPP Works?
IPP is a protocol that allows users to manage their internet-connected printers and send print jobs to printers hosted online. The difference between IPP and other printer management protocols is that IPP allows a secure protocol for accessing control lists, encrypted communications, and authentication.
Issues with Unsecured IPP Ports
Unsecured IPP ports are vulnerable to several kinds of attacks. It is found that a quarter of the total number of printers with IPP capability (over 20,000 devices) have exposed information about their brand and model.
“Out of the roughly 80,000 exposed services, a large percentage returned additional printer information attributes, such as printer names, locations, models, firmware versions, organizational units and even printer wifi ssids,” the researchers added.
“Exposing printer devices with anonymous, publicly queryable vendor names, models and firmware versions obviously makes it much easier for attackers to locate and target populations of devices vulnerable to specific vulnerabilities,” the researchers added.
60% of Enterprises Suffer Printer Security Breaches
A similar research from Quocirca revealed the risks of unsecured printers. It stated that 60% of businesses in the U.K., U.S., France, and Germany suffered a print-related data breach last year, which resulted in a data loss that cost companies an average of more than $400,000. In addition to financial loss, data breach victims also suffer damage to productivity, consumer confidence, and brand value, the report said.










