
McAfee’s advanced threat research team discovered a new phishing campaign linked to the North Korean hackers targeting the U.S. defense and aerospace sectors with fake job opportunities. The campaign, which is dubbed as “Operation North Star,” began in late March and lasted till May 2020, McAfee said in a security alert.
Operation North Star’s Modus Operandi
The hackers impersonated recruiters and sent malicious emails with Microsoft Office templates to high-profile employees with an aim of injecting malware in the targeted devices to obtain network systems access and steal data. The Microsoft Office templates were hosted on a command and control server and the download link was embedded in the first stage document. The malicious documents contained job postings from leading U.S. defense contractors to lure victims into opening them and ultimately execute the payload.
The hackers coaxed the victims to recruit for leading U.S. defense and aerospace programs and groups including:
- F-22 Fighter Jet Program
- Defense, Space and Security (DSS)
- Photovoltaics for space solar cells
- Aeronautics Integrated Fighter Group
- Military aircraft modernization programs
McAfee researchers also observed fake job offers pertaining to sectors outside of defense and aerospace, such as a finance position for a leading animation studio.
Attack Overview
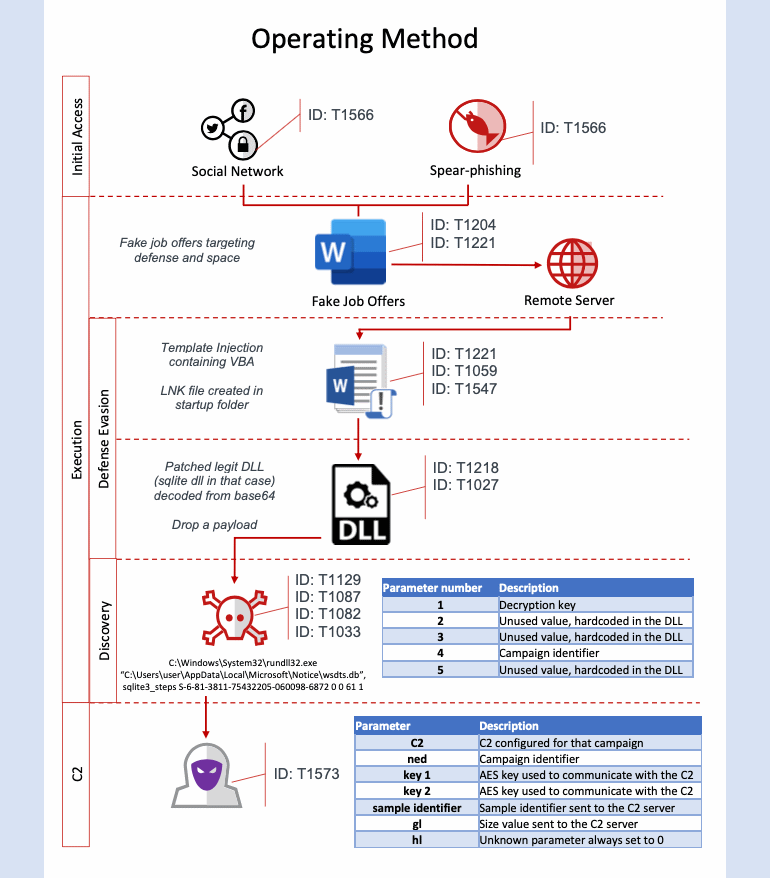
The researchers also stated that the attack techniques or TTPs (Techniques, Tactics, and Procedures) of Operation North Star are similar to previously discovered campaigns associated with “Hidden Cobra,” a North Korean state-sponsored hacking group which was active from 2017 to 2019.
Hidden Cobra group consists of multiple threat actor groups like Lazarus, Kimsuky, KONNI, and APT37, which target organizations around the world by gathering data around military technologies to cryptocurrency theft from leading exchanges.
“Our analysis indicates that one of the purposes of the activity in 2020 was to install data gathering implants on victims’ machines. These DLL implants were intended to gather basic information from the victims’ machines with the purpose of victim identification. The data collected from the target machine could be useful in classifying the value of the target. McAfee ATR noticed several different types of implants were used by the adversary in the 2020 campaigns,” the researchers said in a report.
“The TTPs of this campaign align with those of previous Hidden Cobra operations from 2017 using the same defense contractors as lures. The 2017 campaign also utilized malicious Microsoft Word documents containing job postings relating to certain technologies such as job descriptions for engineering and project management positions involving aerospace and military surveillance programs. These job descriptions are legitimate and taken directly from the defense contractor’s website. The exploitation method used in this campaign relies upon a remote Office template injection method, a technique that we have seen state actors use recently,” the report added.










