
Based on the inputs from the threat hunting and analytics company, Group-IB, the INTERPOL conducted “Operation Falcon,” which saw three Nigerian BEC scammers getting arrested from the city of Lagos. The three alleged members belong to a larger cybercriminal group dubbed TMT. This group is popularly known to distribute malware through phishing; in other words they carry out business email compromise (BEC) attacks.

Operation Falcon, which was led by INTERPOL, had able and active support from the Nigerian Police Force and Group-IB’s APAC Cyber Investigations Team. The cybercriminals have been active since at least 2017 and have compromised more than 500,000 government and private sector companies in over 150 countries. The investigation continues as some of the gang members remain at large.
What is Business Email Compromise (BEC)?
BEC is a type of email phishing attack that employs social engineering techniques. As part of BEC, phishing emails can target people within an organization or send it to a particular group or department. It is often disguised as money transfer requests, HR-communications, or business proposals so that the cybercriminals can lay hands on confidential data.
About the Cartel
The data discovered on the devices of the arrested TMT members have confirmed their involvement in the criminal practice. The Nigerian Police Force has also identified the stolen data from at least 50,000 targeted victims.
Based on the infrastructure that the attackers use and their techniques, Group-IB was also able to establish that the gang is divided into subgroups with several individuals still at large. Researchers at Group-IB have already shared their findings on other suspected gang members with INTERPOL’s Cybercrime Directorate.
Modus Operandi
The analysis of their operations has revealed that the gang focuses on the distribution of phishing emails that contain popular malware strains under the guise of purchasing orders, product inquiries, and even COVID-19 aid impersonating legitimate companies.
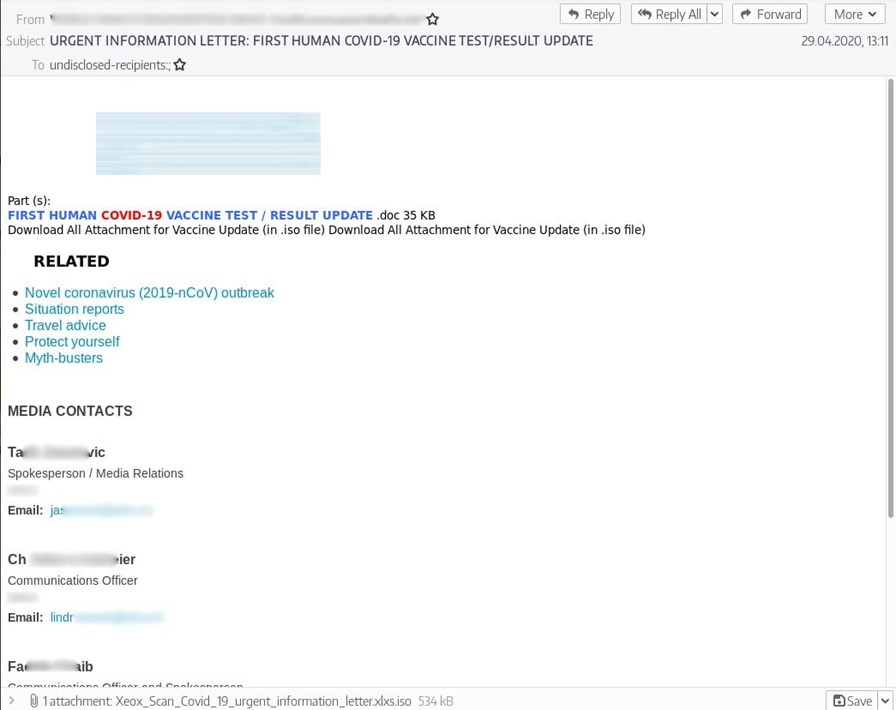
The attackers then use Gammadyne Mailer and Turbo-Mailer to send out phishing emails, which are then tracked using MailChimp to see whether a recipient victim has opened the message.
Group-IB researchers note that the cybercriminals behind these BEC operations rely exclusively on a variety of publicly available Spyware and Remote Access Trojans (RATs), such as AgentTesla, Loky, AzoRult, Pony, NetWire, etc. To avoid detection and tracking by traditional security tools the gang uses public crypters. Most often malware operated by TMT communicates with the attackers’ C&C server using SMTP, FTP, HTTP protocols.
TMT’s end goal has always been to steal authentication data from browsers, email, and FTP clients. While the monetization methods of this gang are still being investigated, it is a known fact that PII and other critical data are sold easily on the dark web, which could be the case here as well.
Related News:
Group-IB Finds Half a Million Credit Cards of Indian Banks on Darknet
Craig Jones, INTERPOL’s Cybercrime Director said, “This group was running a well-established criminal business model. From infiltration to cashing in, they used a multitude of tools and techniques to generate maximum profits. We look forward to seeing additional results from this operation.”
Related News:
Nigeria Among Top 10 Countries Impacted by Mobile Malware: Kaspersky Lab










