
Cybercriminals have been putting an added strain on the financial sector for the past few years. A report in November 2020, showed that 65% of the financial services firms suffered a cyberattack last year. However, the majority of these cyberattacks originated from phishing or ransomware attacks. But it seems like the new year has brought in a new methodology of attacks in the cybercrime world. A cyber intelligence report from Group-IB, a global threat hunting company, has found traces of an ongoing fraudulent campaign based on Twitter targeting Indonesia’s largest banks.
The Massive Cybercriminal Campaign
To lure and gain the trust of its victims, cybercriminals are posing as bank representatives or customer support team members on Twitter and laying the booby trap. This massive campaign, which began in January 2021, has already ballooned 2.5-fold (from 600 in January) to a total of 1,600 fake Twitter accounts impersonating banks, until early March.
Digging deep, the security analysts found evidence of at least seven large Indonesian financial institutions that have been targeted under this campaign. The scam affects over two million Indonesian bank customers who are active on the legitimate bank handles on Twitter. Upon discovery of this fraud, Group-IB has informed the banks impacted so that they take the necessary steps to remedy the situation.
The Modus Operandi
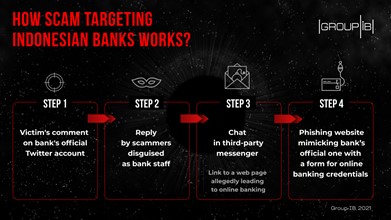
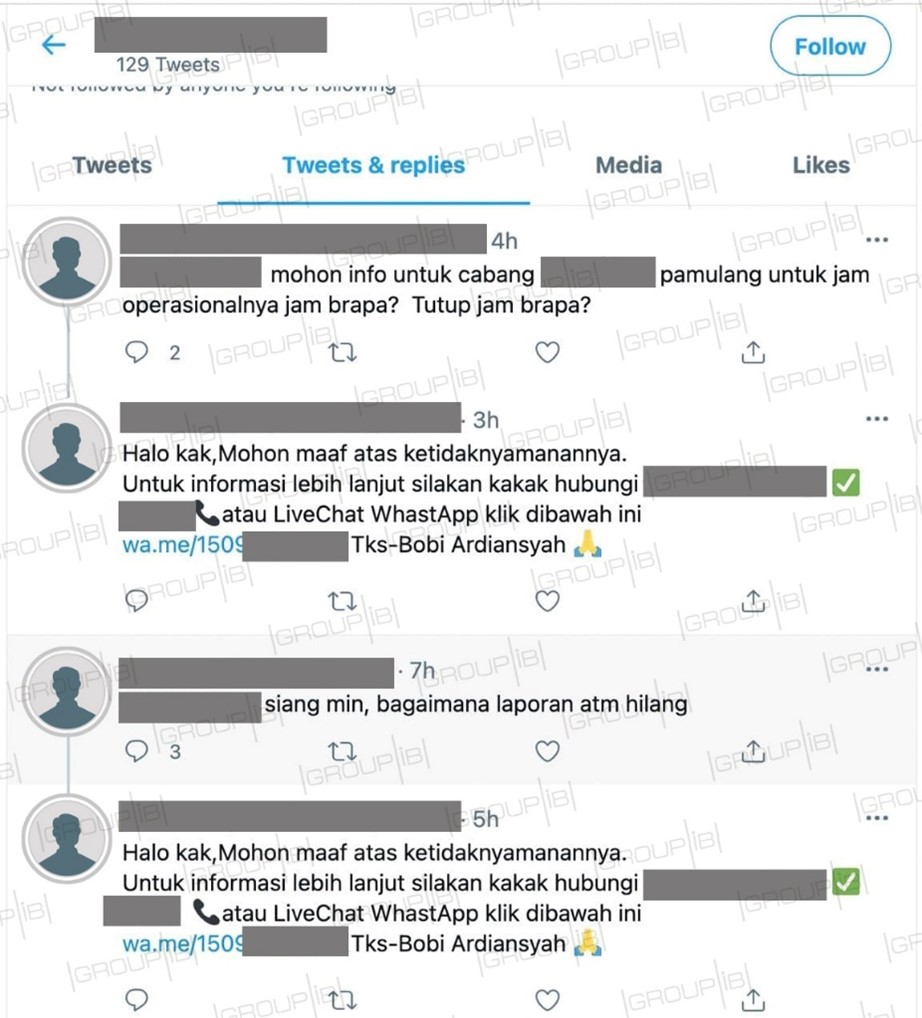
Cybercriminals zero down on their victims after a bank customer asks a question or leaves their feedback on the bank’s official Twitter page. They are then promptly contacted by fraudsters who use fake Twitter accounts with a profile photo, name, header, and description, identical to those of the real ones. After engaging in a talk with the victim, attackers soon invite them to take the conversation off-line on a third-party messenger – WhatsApp or Telegram. Furthermore, fraudsters send the bank customers a link asking them to log in there for solving their problem through a complaint. The link redirects to a phishing website identical to the official one. Once they enter their online banking credentials, which include username, email, and password, cybercriminals exfiltrate this data.
Group-IB DRP analysts have recorded similar attempts of implementing a fraudulent scheme on other social media channels, like Facebook, however, the number of such cases is insignificant compared to Twitter.
Ilia Rozhnov, Group-IB head of Digital Risk Protection in APAC, said, “The case with the Indonesian banks shows that scammers have managed to solve one of the major challenges of any attack — the issue of trapping victims into their scheme. Instead of trying to trick their potential victims into some third-party website, cybercriminals came to the honey hole themselves. This campaign is consistent with a continuous trend toward the use of multistage scams, which helps fraudsters lull their victims. They become successful due to the lack of comprehensive digital asset monitoring by financial institutions.”
How to Identify such Scams
The fact that the fraudulent scheme begins on the bank’s official Twitter account makes it challenging for a victim to identify it. To avoid being a victim, one should carefully check the account they are being contacted from. The majority of known brands have verified accounts on social media. If the account does not have “verified” status, then you can check the account’s ID and map it with the ID mentioned on the company’s official website. Also, look out for any phishing links. Spend some extra seconds to check if the link you are going to click is identical to the domain of the official website. Fraudsters often register domain names mimicking official ones, changing one letter in it, or adding a punctuation mark. As rightly suggested by the Group-IB’s DRP team, “The critical examination of any website on which you plan to enter your data is a habit that must be developed by everyone willing to keep their money safe.”
Related News:
Group-IB Finds Half a Million Credit Cards of Indian Banks on Darknet
The Pandemic-hit World Witnessed a 150% Growth of Ransomware










