
A vulnerability in almost all antivirus software platforms could have been exploited to disable anti-malware protection and turned into destructive tools, security researchers from RACK911 Labs revealed. RACK911 Labs has found a unique method of using directory junctions (in Windows) and symlinks (in macOS and Linux) to turn antivirus software products into self-destructive tools. However, it was reported that most of the antivirus companies have now fixed the vulnerability in their products.
How the bugs are exploited
Researchers stated that an attacker must be highly time-sensitive and should know when to exploit the directory junction or symlink vulnerabilities. “What most antivirus software fail to take into consideration is the small window of time between the initial file scan that detects the malicious file and the cleanup operation that takes place immediately after. A malicious local user or malware author is often able to perform a race condition via a directory junction (Windows) or a symlink (Linux & macOS) that leverages the privileged file operations to disable the antivirus software or interfere with the operating system to render it useless,” the researchers explained.
Researchers used their proof-of-concept (PoC) to exploit Norton Internet Security for macOS and downloaded the EICAR test-string from Pastebin to evade protection that prevents the antivirus to download the test-string from the Norton official website. They also attempted the antivirus exploitation process against McAfee Endpoint Security for Windows using the same POC and were able to delete the EpSecApiLib.dll file.
Affected Antivirus Software
The researchers also listed all the vulnerable antivirus software products, which include:
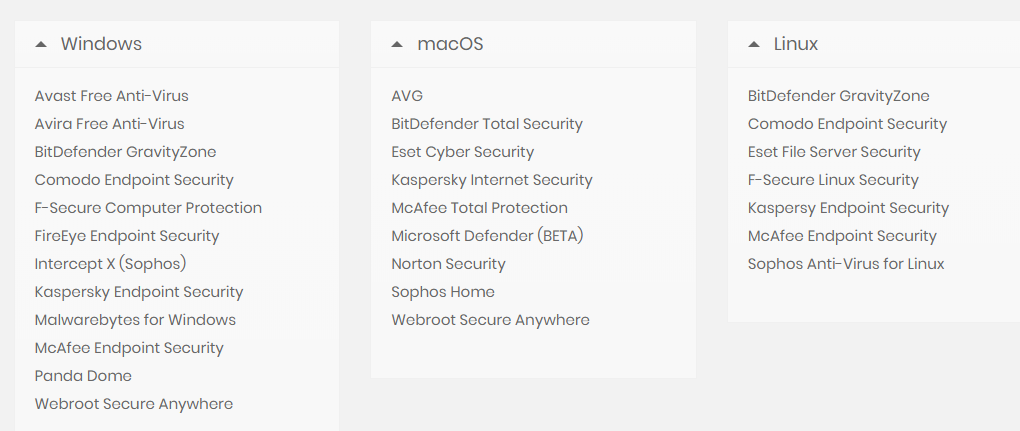
RACK911 Labs stated that it notified all the antivirus vendors about the security vulnerabilities affecting their platform. It also clarified that most of the antivirus vendors have fixed the vulnerabilities in their antivirus products.
“Whether it’s Windows, macOS or Linux, it’s extremely important that file operations happen with the lowest level of authority to prevent attacks from taking place. One must always assume the user is malicious and by performing privileged file operations within reach of the user, it’s opening the door to a wide range of security vulnerabilities,” RACK911 Labs concluded.










