
Man-in-the-middle (MITM) attacks are gaining importance in the cyberattack landscape as threat actor groups are leveraging it more often to harvest users’ sensitive data and break into targeted network systems. Personal information obtained via MITM attacks could be used to launch various cyberattacks, including identity theft, illicit fund transfers, and credential stuffing attacks.
By Rudra Srinivas, Senior Feature Writer, CISO MAG
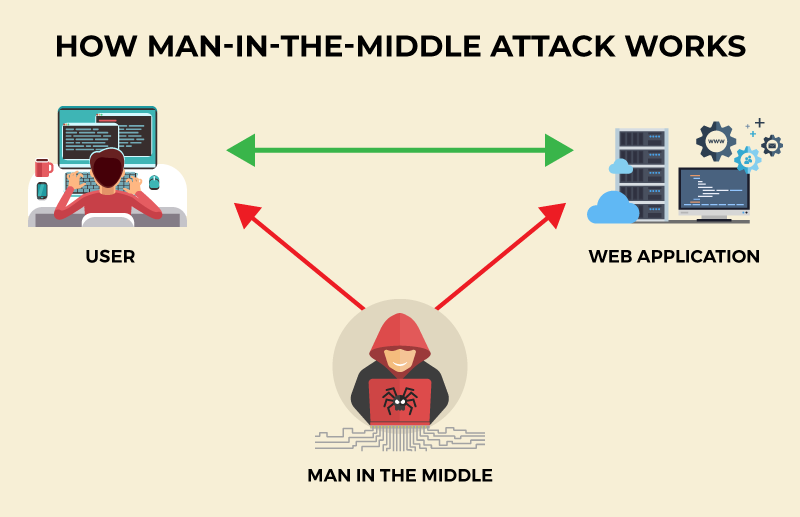
What is Man-in-the-Middle Attack?
In a man-in-the-middle attack, the perpetrator places himself in an ongoing communication or data transfer between an application/service and its user to spy or impersonate someone. The MITM attackers mainly focus on stealing personal information like bank account numbers, credit/debit numbers, account login credentials, and other banking-related data. They primarily target e-commerce sites, financial applications and websites, other websites, where logging in is involved.
The MITM attack typically occurs between two genuine communicating hosts, between a machine and a user; two machines; two users, enabling a hacker to snoop a conversation or exploit the targeted system.
Impacts of MITM Attack
A successful MITM attack could enable an attacker to:
- Position themselves as proxies in an ongoing conversation or data transfer
- Exploit the communication and data transmission stealthily
- Steal confidential information regarding trade secrets or fund transfer details
- Insert malicious codes or links disguised as legitimate data
Types of Man-in-the-Middle Attacks
1. Email Hijacking
In email hijacking, threat actors compromise victims’ email account and eavesdrop on the email conversations. Email hijackers also leverage phishing lures like social engineering tactics to obtain sensitive information or inject malware by impersonating an authorized person.
2. IP Spoofing Attacks
In an IP spoofing or IP address spoofing attack, hackers create a false IP address source to impersonate another computing system to break into a network monitor the activities silently. Threat actors primarily leverage IP spoofing attacks to launch Denial of Service (DoS) attacks.
3. Session Hijacking
Session hijacking, also known as cookie hijacking, is a process of exploiting an online session to illicitly gain access to the information or services on the website, application, or device. Session hijackers typically target browser or web application sessions while you are shopping online or paying bills.
4. DNS Spoofing
Also known as DNS cache poisoning or DNS poisoning, a DNS spoofing attack corrupts the DNS server by changing the actual IP address with the bogus one in the server’s cache memory. Attackers use this technique to redirect the web traffic to the hackers-controlled site to harvest sensitive data.
5. Wi-Fi Eavesdropping
Most public Wi-Fi networks are insecure and easy to tamper with. Threat actors often rely on public Wi-Fi hotspots to infiltrate into user networks to eavesdrop on the activities.
Cybercriminals could also launch a Wi-Fi Eavesdropping attack by creating their Wi-Fi hotspot called Evil Twin – a fraudulent Wi-Fi access point disguised as legitimate that spies on wireless communications.
6. Man-in-the-Browser
In man-in-the-browser attacks, threat actors try to exploit vulnerabilities in browsers and web applications to deploy malware, Trojans, and malicious Java codes to capture users’ private information in real-time.
Real-World MITM Attacks
From exploiting Cable Haunt vulnerability that exposed over 200 million modem gateways in Europe to snooping more than 500 million UC Browser users, the MITM attacks have increased their reach in the security landscape. The man-in-the-middle attack is also included in the primary attack techniques used by cybercriminals to launch significant cyberattacks along with Distributed Denial of Service Attack (DDoS), SQL Injection attack, and phishing attacks.
How to Prevent Man-in-the-Middle Attacks
In general, most MITM attacks can be detected and prevented by following basic security and encryption measures. Users must:
- Avoid public and insecure Wi-Fi connections while using e-commerce or banking websites
- Pay attention to browser notifications for unsecured websites.
- Properly log out from all applications online after the session.
- Secure your device with an intrusion detection system. Deploy strong firewalls and protocols to prevent unauthorized intrusions.
- Secure communication protocols like TLS and HTTPS with robust encryption and authentication procedures.
- Verify domain names and browsers before visiting an unknown or insecure website.
- Check for a green or gray padlock located to the left of the web address for legitimacy. In case the browser shows a red padlock, the website might be insecure.
About the Author:
Rudra Srinivas is a Senior Feature Writer and part of the editorial team at CISO MAG. He writes news and feature stories on cybersecurity trends.
More from Rudra.











