
According to a report from Fireeye, the Vietnamese threat group APT32 is suspected to have carried out a series of attacks aimed at the Wuhan province government and China’s Ministry of Emergency Management to collect intelligence on the COVID-19 crisis. The researchers noted that the attackers targeted multiple users through a spear-phishing campaign run from at least January to April 2020.
The COVID-19 crisis poses an intense, existential concern to governments, and the current air of distrust is amplifying uncertainties, encouraging intelligence collection on a scale that rivals armed conflict.
– Fireeye
Brief History of APT32
APT32 aka OceanLotus or APT-C-00, is suspected to be backed by the Vietnamese government. APT32 is popularly known to carry out cyber espionage campaigns against companies and countries doing business, manufacturing, or preparing to invest in Vietnam. The threat actors leverage a phishing mail to initiate an attack that contains ActiveMime files. They make use of social engineering as a bait to lure the victim into enabling the macros. Once executed, the initialized file downloads multiple malicious payloads like Soundbite, Windshield, Phoreal, Beacon, and Komprogo from a remote server.
Phishing Emails with Tracking Links
The first phishing attack was traced to January 6, 2020, when APT32 sent an email to China’s Ministry of Emergency Management using the sender address as lijianxiang1870@163[.]com and the subject 第一期办公设备招标结果报告 (translation: Report on the first-quarter results of office equipment bids). The email’s content had an embedded link that sent the victim’s email address and codes back to the threat actors indicating them that the email was opened.
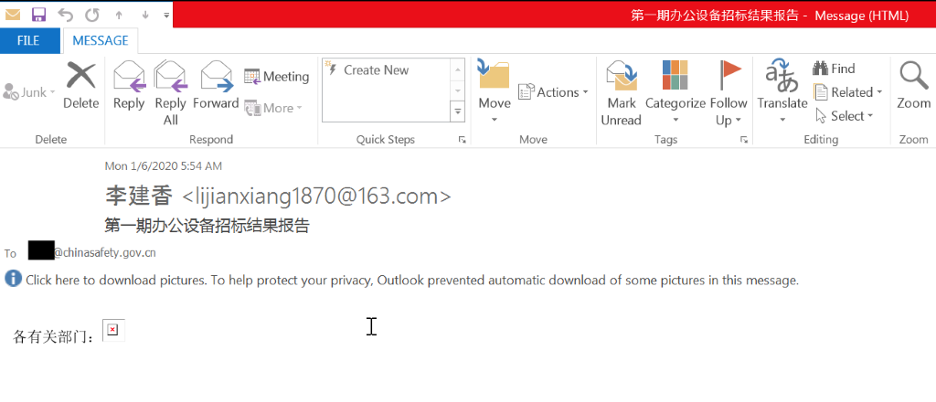
Researchers also found that the libjs.inquirerjs[.]com domain was being used since December as a C2 domain for a METALJACK phishing campaign to target Southeast Asian countries. APT32 likely used COVID-19-themed malicious attachments in Chinese-Language as a decoy to drop a METALJACK payload.
Threat Summary |
|
| Threat Group | APT32 |
| Threat type | Spear-phishing, phishing |
| Payload Name | METALJACK |
| Target Audience | South-east Asia, Chinese speaking |
| Campaign Active Since | From at least January 2020 |
| Domain Indicators | · m.topiccore[.]com
· jcdn.jsoid[.]com · libjs.inquirerjs[.]com · vitlescaux[.]com |
| Email Address Used | lijianxiang1870@163[.]com |
| Malicious File Names | MD5: d739f10933c11bd6bd9677f91893986c – METALJACK loader
MD5: a4808a329b071a1a37b8d03b1305b0cb – METALJACK Payload MD5: c5b98b77810c5619d20b71791b820529 – Decoy Document (Not Malicious) |
| Damages caused | Intellectual and confidential COVID-19 related state and government data can be compromised. Additional trojans and malware infections can be installed to exfiltrate data in future. |
Researchers added that, “The COVID-19 crisis poses an intense, existential concern to governments, and the current air of distrust is amplifying uncertainties, encouraging intelligence collection on a scale that rivals armed conflict. National, state or provincial, and local governments, as well as non-government organizations and international organizations, are being targeted. Until this crisis ends, we anticipate related cyber espionage will continue to intensify globally.”










